Section 9.2. Locks and Keys: Old and New
9.2. Locks and Keys: Old and NewThe first line of defense against intruders is to keep them outout of your building, out of your server room, out of your telecommunications closets. In the past this was easier. The locked or guarded computer room has historically been the primary means of protecting an organization's computer equipment and information from physical intrusion and unrestricted access. The terminals that were on desktops were very thin clients, "dumb terminals" in fact, capable of manipulating data only in the mainframe. In most organizations these days, everyone has a workstation, from which information can be removed easily on a USB memory stick or floppy disk, for instance. Printers, from which documents can be collected, are distributed around the office. Locking up is harder in this kind of environment, but it still is a good idea. Kick the janitor out of the telecommunications closet and spill the cleaning supply storage shelves into the hallway. Boot the network administrators out of the server room and put on a combination lock. Gather up the backup tapes and the old hard drives and installation CDs for operating systems and office applications, and store them in a locked metal cabinet. To gain access to a locked facility, a user should have to pass an authentication test. Remember from Chapter 3 that there are three classic ways in which you identify yourself (i.e., prove that you are who you say you are):
All of these authentication techniques can be used for physical security (e.g., building or computer room access) as well as for system access control. When a smart card or a fingerprint is used for computer access, it's usually only a first step. Passwords are typically required as well. When two distinct techniques are used for authentication in this way, it's called two-factor authentication. One factor is something you have; for example, you present your smart card or have your fingerprint or voiceprint scanned. The other factor is something you know; for example, you type a personal identification number (PIN) or a password into the system. Multifactor identification systems promote a "defense in depth" environment.
Some organizations add another dimension of security to a locked facility by using surveillance devices, such as closed-circuit television and more sophisticated access detectors that use infrared, ultrasonic, laser, or audio technologies. Advanced digital video recorders can record multiple cameras and cause an alarm when images change, such as people appearing in certain hallways or going through certain doors. Highly secure facilities can install elaborate turnstiles called mantraps (see Figure 9-1). Systems of this kind route personnel through a double-doored facility in which you show a badge to a guard or are subjected to verification techniques, such as weight checks (to ensure against your entering the facility with an unauthorized buddy), key checks, and biometric checks, such as those described later. If you fail to pass the tests, you are trapped between the double doors, unable to enter or exit the facility until a security officer investigates the incident! Figure 9-1. A mantrap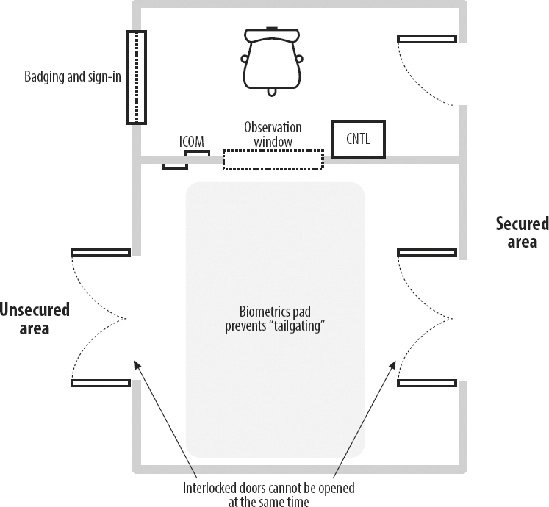 9.2.1. Types of LocksIn addition to locking up buildings and computer rooms, you can also secure your computer, your network, your disk drives, and your disks. Here are two lock examples:
9.2.2. TokensA token is an object that you carry to authenticate your identity. In ancient times, a trusted courier might have carried the king's ring to a foreign kingdom to prove that he could speak for the king. Modern tokens are electronic devices, usually containing encoded information about the user who's authorized to carry it. Typically, a token is used in conjunction with another type of authentication, in a two-factor authentication system. For example, with certain types of PC security packages, you must insert an electronic, key-shaped token during login and authentication. After the system recognizes the token, it prompts you to type identifying information (e.g., ID and password) and compares your entry with the information encoded on the token. If the two match, you'll be allowed access. If they don't, you'll usually be given a few more chances. After multiple failures, you'll be locked out, and an alarm will sound. These tokens do not require user interaction; for this reason they are sometimes referred to as passive tokens. Modern token systems are packaged as PCMCIA (PCCARD) or USB form factor devices that fit into your computer. Soft tokens, secure passwords that are unique to your computer, can also be installed. In most cases, tokens are used as part of a VPN secure transmission path, which allows a portable computer to log onto a corporate network from out of the office or on the road, and implements encryption on the data that is transferred. 9.2.3. Challenge-Response SystemsSome public key authentication products are more sophisticated versions of electronic tokens. These can be called active tokens. Challenge-response systems typically use a hand-held device containing an encryption program and a key. When you try to log in, the system challenges you with a random number. You type this number into the hand-held device, which encrypts it and displays the result. Now, you type that number into the system. The system compares the typed response with the result of its own encryption of the random number. If the two numbers match, you're allowed access. Versions of this kind of device include smart cards that display a code periodically. To log into a system or enter a secure facility, you identify yourself (by typing your PIN or password), and you also type the code that's currently displayed on your smart card. The card is synchronized with network timing signals, so that a stolen sequence is valid for only a short time. Such systems offer a number of other special features. For example, the card can be designed to stop and erase its memory at the end of its programmed lifetime. If you attempt to open the card to replace batteries or change it in any way, the card is permanently disabled. 9.2.4. Cards: Smart and DumbFor many years, ID badges, often with photos, have served as credentials. You must present your license to the bank teller or supermarket clerk before you're allowed to cash a check. You must flash your employee badge before the building guard allows you to enter the building. Authentication works by having someone visually match your face to your picture. Automatic teller machine cards and certain types of credit cards use a more reliable type of matching that magnetically encodes identifying information on the card. For example, an ATM works by comparing the information on the card to the information you enter at the ATMusually some combination of account number, PIN, and/or passwordand allowing you to withdraw money only if the match is successful. Increasingly, more advanced types of cards are being used to control access to buildings, computer rooms, and computers themselves. The typical access card is the size of a credit card. It usually contains an encoded identifying number, password, or other type of prerecorded information, often in encrypted form. Depending upon the sophistication of the system, the card may contain a large amount of additional information. The newest types of access cards are called smart cards. Smart cards come in different sizes and shapes. Some look like credit cards, some look like memory sticks, and some are shaped like a watch fob. One popular version provides secure transmission information using state-of-the-art encryption algorithms, and fits on a standard key ring. A disadvantage to tokens is that they are small and easily misplaced, and they can be costly, from $25 to over $100 dollars. These cards contain microchips that consist of a processor, memory used to store programs and data, and some kind of user interface. Sensitive information, which typically includes the user's PIN and/or password, is kept in a secret zone of the read-only memory. This zone is encoded during manufacturing, using cryptographic techniques, and is inaccessible even to the card's owner. The newest forms of smart cards are ultra-small modules that communicate via radio with sensors on the device or doorway to be protected. These usually contain not only the information required to access the protected area or device, but also personal information related to what you can or cannot do once you have entered of logged on. Advanced versions of these identifiers may contain health related information, which can be used if you are found unconscious or disabled, or man-down sensors, which can alert personnel if you fall or come under duress.
Unlike most of the other types of access cards that are typically used (like badges) simply to gain entry to a facility, smart cards are often used for authentication. When a user attempts to log in or enter a secure facility, the computer system may transmit information to the smart card, which performs a series of complex calculations on it and transmits the result back to the computer. If the transmitted result matches the expected result (which is possible only if you have an authentic smart card), you're allowed to enter. Many smart cards are built to work with card readers. You insert the card in the reader. The system displays a message, and you enter your personal identifier in response. If the identifier matches the one expected, you're allowed access. |
EAN: 2147483647
Pages: 121