Section 8.4. Network Security
8.4. Network SecurityIn the early days of networks, a network administrator usually had tight control over whether a system could connect to another remote system. These days, with the proliferation of interconnected networks and easy remote access and resource sharing, it's often impossible to identifynever mind to trustall of the points of access to a system. There are a number of different strategies for accomplishing security in a network environment. The choice of which and how many strategies to use depends largely on the type and scope of the network, the level of trust that can be placed in the users, and the value of the data that's being transmitted.
8.4.1. Access Control MethodsAn interesting problem with security is that not only must information be protected from outsiders, it must sometimes be protected from insiders as well. For instance, patient information in a doctor's office can be accessed by medical staff, and in fact in an emergency should be readily available. However, vendors who visit the office must not be allowed to see it, nor should cleaners or facility maintenance personnel. Keeping information stratified inside an organization is a form of access control. Various methods that control access to network environments are described in the following sections. 8.4.1.1. Discretionary access controlIn an operating system, discretionary access control (DAC) can be used to restrict file access to certain users or groups. In a network environment, DAC may restrict access to certain remote users and/or systems. A particular network service might be available only to a certain group, which might be defined in a network environment as a particular Internet address (e.g., all the users of a particular system in the network). 8.4.1.2. Role-based access controlIn many cases, it is not so much the person as their position in the organization that determines whether or not they should have access to a given record or file. Engineers rarely need access to payroll data. They would likely look up coworkers' salaries, get jealous or gloat, and perhaps post the information on the Internet somewhere. Accountants rarely require access to the wind-tunnel test data of the secret new fighter aircraft. It might not mean much to them, and they may try to correct minor math errors they may come across. (On the other hand, this can be an advantage. One very sensitive national defense project was discovered to be flawed when the calculations regarding thrust of a rocket engine were found to contain an incorrect formula. The engineers did not detect their error mathematically; it first showed up when a computer artist modeled the burn on PC and the graphic results changed unexpectedly at the point where the formula was flawed.) To separate information by department rather than by person is called role-based access control. 8.4.1.3. Mandatory access controlEvery system in a trusted network must label its data with security attributes (e.g., sensitivity labels, information labels, login IDs, etc.). This way, the sensitivity of the data will be recognized if the data is sent to another system. Because different networks support different security policies, these labels are not necessarily in the same format. In certain types of secure networks, each system may effectively have a label. Mandatory access control keeps TOP SECRET data, for example, from being sent over the network to a system labeled as SECRET. It is actually quite challenging to insure that no TOP SECRET documents are read by persons with only SECRET clearance, a condition called read down. Similarly, it must be made impossible for persons with SECRET clearance to save documents with a TOP SECRET classification (write up). 8.4.2. AuditingIn a network environment, additional networking events must be audited on both sides of the network connection. Examples include establishing or dropping a network connection, security violations such as lost or misrouted data, and failure of a network component. 8.4.3. Perimeters and GatewaysThe simplest way to protect a network from access by unauthorized users is to keep that network physically securefor example, to provide physical protection of all internal network switches and connections, no telephone connections, and no network cabling to the outside world. As mentioned previously, such a system can be nicknamed as an airwall, because there is a effectual gap between external elements and internal elements. But with trends toward wider communication, most organizations will at least occasionally have to communicate with outside systems and networks. Communication between trusted and untrusted networks must have very clear rules associated with it. A trusted local area network can be thought of as being inside a security perimeter. Inside the perimeter, access controls and other security features determine who can access what information. For example, in a trusted system supporting multilevel military security, some users are cleared to access TOP SECRET data, others only SECRET, CONFIDENTIAL, or UNCLASSIFIED data. In a fairly simple network environment, all information originating outside the trusted network might be treated at a single sensitivity level. In such an environment, a gateway system, known as a firewall, or a firewall computer if it is built out of a PC with two network cards, might separate the trusted system or network from the untrusted systems or networks outside it. Untrusted systems can communicate with trusted systems only through a single communications channel controlled by a trusted gateway. The gateway controls traffic from both inside and outside the network and effectively isolates the trusted network from the outside world. Because the firewall protects the other machines within the perimeter, security can be concentrated on the firewall. In the simplest case, where everything inside the perimeter is trusted and everything outside is untrusted, the gateway system labels and filters data. When information is imported into a trusted system from an untrusted system, the gateway system puts a sensitivity label (usually "UNCLASSIFIED") on this data. When information is exported from a trusted system to an untrusted system, the gateway system filters that information by exporting only data that the untrusted system is allowed to process (usually UNCLASSIFIED data). If multilevel security is supported, more complex network solutions are required to regulate access to the different security levels, as described in the next section. 8.4.4. Security in Heterogeneous EnvironmentsMore and more modern networks are attempting to serve heterogeneous computing environments. Networks must have facilities for supporting a whole range of security environments, corresponding to the host systems they serve. Using a trusted gateway to partition trusted networks from untrusted networks, as described in the previous section, works only if communications from outside the trusted network can be treated at a single level of security. In more complex environments supporting multilevel communications, more complex solutions are needed. On the trusted network side, a system must make decisions about requests originating outside the trusted network. It must regulate which information remote users are cleared to access, and it must control which system services remote users are granted. In standard networks, in which the security attributes of the remote user aren't transmitted, the local system doesn't have sufficient information to make access decisions. This can lead to major security problems. For example, if a trusted network server on the trusted network side processes requests on behalf of an untrusted remote user, the security of the whole system is at risk. There must be some way to propagate to the local process (the process on the trusted network side) the security attributes of the remote user (the process on the untrusted network side). This isn't as simple as sending a "TOP SECRET" label, for example, from one side to the other. Even if a user is cleared for TOP SECRET information on one system, he's not necessarily given the same courtesy when he accesses another system. Each system in the network must be able to compare the attributes of the process performing an operation with those of the file or other object on which the operation is performed, and make access decisions that are appropriate to the local system's security policy. To do otherwise invites incredible risk, especially in this day when snippets of code are passed readily between computers for execution. 8.4.5. Encrypted CommunicationsEncryption, a process that transforms information into another form that cannot be read by unauthorized users, is a very important part of network security. Because information is so vulnerable to attack when it's being transmitted over a network, encryption offers a strong assurance that even if the information is intercepted, it won't be comprehensible. (See Chapter 7 for a detailed description of encryption.) In addition to protecting the secrecy of messages transmitted over a network by transforming them into data that appears to be unintelligible, encryption can also ensure the integrity and authenticity of those messages. Message authentication provides a critical network security tool; it ensures that a message was received in exactly the form sent. At the sending end, the encryption process appends a message authentication code to the encrypted message. At the receiving end, the decryption process independently calculates a message authentication code and compares it with the code sent with the message. If the two are identical, the message was sent and received accurately. A digital signature is another network security tool that provides electronic evidence that you, and only you, sent a signed message. Because the message incorporates a secret key that only you possess, it can't be forged. It's an immutable proof that you sent a message. A message that's proved to be authentic by an outside authority, sometimes called a notary, is said to be arbitrated. As with a traditional notary, who provides independent evidence that someone is who she claims to be, a digital notary attests that a message is genuine. The notary may also provide proof that the message was sent and received at a particular, recorded point in time. This keeps the message from being repudiated by the sender and/or the receiver later on. There are two communications levels at which encryption can be performed, each with different implications for network security: end-to-end encryption and link encryption. 8.4.5.1. End-to-end encryptionWith end-to-end encryption (sometimes called off-line encryption), a message is encrypted when it's transmitted and decrypted when it's received. The network may not even need to be aware that the message is encrypted. This type of encryption sometimes may be selected as an option by the user. The message remains encrypted through the entire communications process, from start to finish, as shown in Figure 8-1. See "End-to-End and Link Encryption" in Chapter 7 for more information. Figure 8-1. End-to-end encryption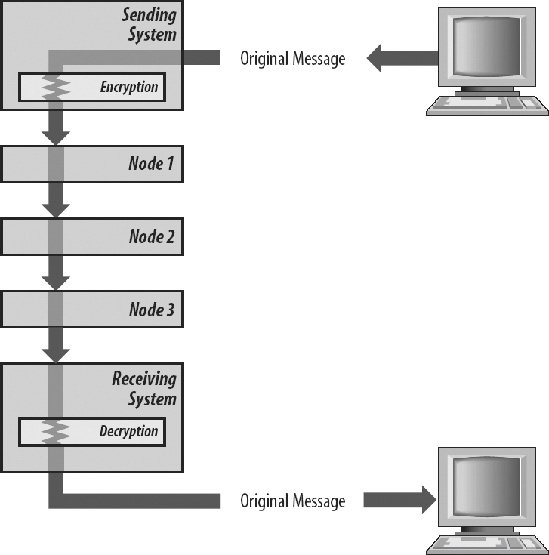 8.4.5.2. Link encryptionWith link encryption (sometimes called online encryption), a message is encrypted when it is transmitted, but is decrypted and then encrypted again each time it passes through a network communications node. The message may therefore be encrypted, decrypted, and reencrypted a number of times during the communications process, and the message is exposed within each node, as shown in Figure 8-2. With link encryption, the encryption is performed just before the message is physically transmitted. Encryption is typically invisible to the user; it is simply part of the transmission process. See "End-to-End and Link Encryption" in Chapter 7 for more information Figure 8-2. Link encryption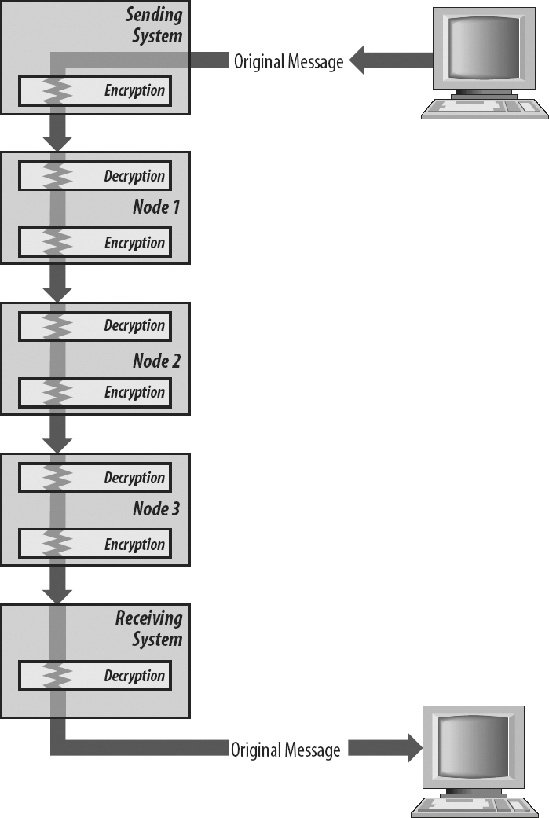 8.4.6. Through the TunnelOne popular technique of encrypting traffic as it travels over a link is called tunneling. As mentioned previously, one of the problems with encrypting a link is that the headers and trailers of each packet, which are the points in the packet where the addressing occurs, have to remain in the clear. This may reveal as much information as if the packet itself was open. (Encoded messages to the enemy's Weapons of Mass Destruction department must always be looked at carefully.) To encrypt the addresses requires that the network be secured in its entirety, drastically increasing expenses. At the very least it requires a system of leased lines, to which no unauthorized parties have access. Maintaining such a network can also be quite expensive, and it doesn't truly guarantee that the lines are not monitored by spies, only that they are not supposed to be. In addition, the cost of such networks may vary by the mile or by the amount of capacity used. This means that the more you use your network, the more costly it can become. In other words, it is difficult to scale a network that consists of many dedicated circuits. Tunneling is the basis of a host of secure technologies. To create a tunnel, packets are placed in a wrapper, which contains the network addressing information. While the wrapper is in place, it handles the navigation through the network. The actual packets are securely encoded inside the wrapper. Once the wrapper carries the packet across the uncontrolled network, the wrapper can be taken off, and the packet decrypted so that its address can be interpreted normally within the secure domain. Tunnels are the basis of virtual private networking (VPN). Basically, a VPN is a private network that uses a public network, often the Internet, to connect remote users and sites together. Because the network behaves as if it was under private control even though it is not, it is called a virtual private network. A VPN uses virtual, non-physical connections that are routed through a public network or the Internet to tunnel packets from the company's private network to the remote site. This means that the user can obtain the utility of dedicated links without having to maintain all those links. 8.4.6.1. VPNs for remote accessVPNs have grown in popularity because they support remote access service. In recent years, many organizations have increased the mobility of their workers by allowing more employees to telecommute. Employees also continue to travel and face an increasing need to stay "plugged in" to the company network. Leased lines don't support mobile workers well because the lines fail to extend to people's homes or their travel destinations. Companies that don't use VPNs must resort to implementing specialized "secure dial-up" services. To log in to a dial-up intranet, a remote worker must call into a company's remote access server using either a toll-free number or a local number. The overhead of maintaining such a system internally, coupled with the possibility of high long distance charges incurred by travelers, make use of VPNs instead an appealing option here. Figure 8-3 illustrates a VPN remote access solution. A remote node (client) wanting to log into the company VPN calls into a local server connected to the public network. The VPN client establishes a connection to the VPN server maintained at the company site. Once the connection has been established, the remote client can communicate with the company network just as securely over the public network as if it resided on the internal LAN itself. Figure 8-3. VPN Remote Access Architecture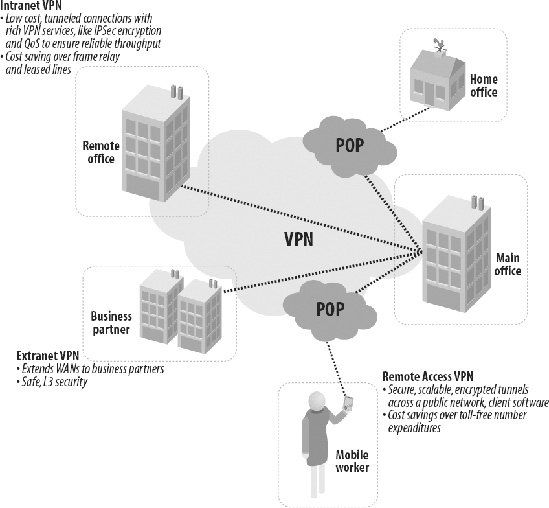 8.4.6.2. VPNs for internetworkingA simple extension of the VPN remote access architecture allows an entire remote network (rather than just a single remote client) to join the local network. Rather than a client-server connection, a server-server VPN connection joins two networks to form an extended intranet or extranet. 8.4.6.3. VPNs inside the firewallIntranets can also use VPN technology to implement controlled access to individual subnets on the private network. In this mode, VPN clients connect to a VPN server that acts as a gateway to computers behind it on the subnet. Note that this type of VPN use does not involve an ISP or public network cabling. However, it does take advantage of the security features and convenience of VPN technology. 8.4.6.4. VPN tunneling protocolsSeveral interesting network protocols have been implemented specifically for use with VPN tunnels. The three most popular VPN tunneling protocols are listed next. These protocols are generally incompatible with each other.
8.4.7. Network Security TasksProviding a secure connection between sender and receiver is a technical challenge. It is divided into several subtechnologies that are described in the following sections. 8.4.7.1. Communications integrityCommunications integrity services ensure that network communications are transmitted accurately. This means that messages aren't forged, modified during transmission, or repudiated by either the sender or the receiver of the messages. (See Table 8-1.)
8.4.7.2. Denial of serviceDenial of service services are designed to ensure that the network keeps working and that all services needed by users are fully available. This means that the network supports good system administration and that there are methods for keeping threats such as message flooding and worms out of the network. (See Table 8-2.)
8.4.7.3. Compromise protectionCompromise protection services are designed to keep information transmitted over the network a secret from those not authorized to access it. This means that the network provides methods for keeping intruders out of the networkboth physically and remotely. (See Table 8-3.)
8.4.8. Securing CommunicationsTo sum up, you need to provide data privacy, authenticity, integrity, and protection against replay attacks for network traffic whether communications are between a client and a server, between two servers, or between two clients. You also need to provide protection when clients access the network remotely, in case you do not want to use a VPN. PPTP and L2TP can provide the security that you need for remote access. The technique discussed next, IPSec, is not designed to be used for VPN remote access. 8.4.8.1. Internet Protocol Security (IPSec)To secure communications over the Internet, which is an open network, requires some additional tools. Internet Protocol Security (IPSec) can provide security across public networks or private networks that you may lease but do not control or for which you cannot guarantee physical security. IPSec was designed by the Internet Engineering Task Force. It defines IP packet formats and related infrastructure to provide end-to-end strong authentication, integrity, antireplay, and if you add an encryption layer, message confidentiality for traffic on networks. An automatic key management service, using the IETF-defined Internet Key Exchange (IKE) based on RFC 2409, can be integrated into the connection. Using IKE provides Kerberos authentication, public/private key signatures, and passwords to establish authenticity and to establish trusted communications between computers. The latter two technologies have been discussed earlier. Kerberos will be detailed in the next section. Once two communicating computers have authenticated each other, they use computer algorithms to generate encryption keys that are known only to the two computers. This allows them to protect the data against modification or interpretation by attackers who may be lurking in the network. The generated keys are created in bulk, because they are automatically refreshed according to IPSec policy settings defined by the administrator, and only a true communications partner would have the correct next key. Making sure both computers start from the same position is the task of the IKE, which insures that the type and strength of keys to use for authentication, and which type of security should be applied to the application traffic being communicated, are the same at each end of the link. 8.4.9. KerberosKerberos is an authentication system for open systems and networks. Developed by Project Athena at the Massachusetts Institute of Technology, Kerberos can be added to any existing network protocol. Historically, Kerberos has been used with Unix-oriented protocols such as Sun's Network File System and in the exchange of certificates. Kerberos uses an encryption system based on the Data Encryption Standard (described in Chapter 7). Each user has a private authentication key. How does Kerberos work? Like its namesake, the many-headed dog who guards the entrance to the underworld, Kerberos guards the data transmitted between machines that communicate over the network. Kerberos uses cryptographic keys known as tickets to protect the security of the messages you send to the systemand the messages the system sends back to you. Kerberos never transmits passwords, even in encrypted form, on the network. Passwords reside only in a highly secure machine called a key server. Kerberos performs authentication both when you log into the system and when you request any type of network service (e.g., a printer or a mail system). The Kerberos authentication sequence works like this:
|
EAN: 2147483647
Pages: 121