OSI Layer Characteristics
The OSI Reference Model describes how information from a user or client application in one host, or computer, moves through an internetwork to an application on another host. The OSI Reference Model, illustrated in Figure 2-1, is a conceptual model composed of seven layers, each specifying particular network functions.
Figure 2-1. OSI Reference Model
The model was developed by the International Organization for Standardization (ISO) in 1984 and is considered the primary architectural model for internetwork communications. Each layer of the model is reasonably self-contained, so that tasks assigned to each layer can be implemented independently. This self-containment enables the solutions offered by one layer to be updated without adversely affecting the other layers. This is critical among internetwork vendors who want to focus their Research and Development (R&D) on one particular function rather than the entire OSI Model.
Figure 2-2 illustrates the OSI Model, identifying common internetworking components and the layer at which these components operate.
Figure 2-2. Components of the OSI Model
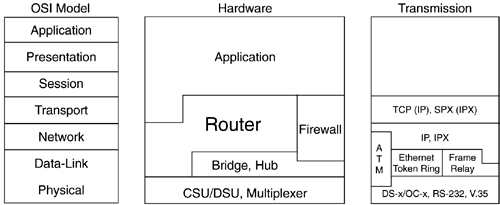
The seven layers of the OSI model are divided into two categories:
Upper layers (5 7) These layers deal with user data and application issues and are implemented only in the client software. The highest layer, Layer-7 (Application), is the layer closest to the end user and functions as the user-data interface.
Lower layers (1 4) These layers handle data transport across the internetwork. The Physical and Data-Link layers are implemented in hardware and software. The other lower layers, Network and Transport, are implemented in the communications software. The lowest layer, the Physical layer, is closest to the physical network medium, such as network cabling. The Physical layer is responsible for placing information on the medium (in the form of bits).
Each of the layers is discussed in more detail in the following sections.
NOTECommunications software is designed for the transmission of data across a connection. Some examples of communications software are ProComm Plus or WinFax. |
Layer-1: Physical Layer
The Physical layer specifications address the physical characteristics of the physical medium. Connectors, pins, use of pins, electrical currents, encoding, and light modulation are all part of different Physical layer specifications.
Examples of Layer-1 (Physical) implementation are as follows: EIA/TIA-232, EIA/TIA-449, V.35, V.24, RJ45, Ethernet, IEEE 802.3, IEEE 802.5, Fiber Data Distributed Interface (FDDI), Non-Return-to-Zero-Inverted (NRZI), Non-Return-to-Zero (NRZ), and Binary 8-Zero Substitution (B8ZS).
Layer-2: Data-Link Layer
The Data-Link layer specifications are concerned with getting data across one particular link or medium, such as a LAN (local area network) or WAN (wide area network). Data-link protocols are concerned with the type of media in question; for example, these data-link specifications define how Ethernet or point-to-point WAN links work.
The Data-Link layer is made up of two sub-layers:
Media Access Control (MAC) Protocol controlling access to the LAN's physical transmission medium
Logical Link Control (LLC) Provides a common interface point to the MAC layers specifying the access method to be used
Examples of the Layer-2 (Data-Link) implementation are Frame Relay, High-level Data-Link Control (HDLC), Point-to-Point Protocol (PPP), IEEE 802.3/802.2, FDDI, Asynchronous Transfer Mode (ATM), and IEEE 802.5/802.2
Layer-3: Network Layer
The Network layer defines end-to-end delivery of packets by defining logical (network) addressing so that any endpoint can be identified. Logical addressing is not hard-coded into the network device and can be changed, unlike physical addressing which is hard-coded into the network device and cannot be changed. The Network layer defines how routing works and how routes are learned so that packets can be delivered. The Network layer also defines fragmenting a packet into smaller packets to accommodate media with smaller maximum transmission unit (MTU) sizes.
NOTEMTU is an acronym for maximum transmission unit, it is the largest frame size that can be transmitted over the network. Messages longer than the MTU must be divided into smaller frames by the network layer protocol. For example, the Layer-3 protocol, such as IP, learns the MTU from the Layer-2 protocol, such as Ethernet, fragments the datagrams into that frame size and makes these datagrams available to the lower layer for transmission. |
Examples of Layer-3 (Network) implementation are Internet Protocol (IP), Novell's Internetwork Packet Exchange (IPX), and AppleTalk Datagram Delivery Protocol (DDP).
Layer-4: Transport Layer
The Transport layer includes the choice of protocols that either do or do not provide error recovery, reordering of the incoming data stream, and reassembly of the data if the packet is fragmented during transmission. For example, Transmission Control Protocol (TCP) may give a 4200 byte segment of data to IP (Internet Protocol) for delivery. IP will fragment the data into smaller sizes if a 4200 byte packet cannot be delivered across the media. The receiving TCP will get three different segments of 1400 bytes apiece, and may receive them in a different order than originally sent. TCP reorders the received segments, compiles them into the original 4200 byte segment, and then acknowledges the data to the sender.
Examples of Layer-4 (Transport) implementation are TCP, User Datagram Protocol (UDP), and Novell's Sequenced Packet Exchange (SPX).
Layer-5: Session Layer
The Session layer defines how to start, control, and end conversations (called sessions), including the control and management of multiple bi-directional acknowledgement messages. Acknowledgement messages serve to notify the application if a series of messages are missing. For example, an Automated Teller Machine transaction in which you withdraw cash from your checking account should not debit your account and fail before handing you the cash, and then record the transaction even though you did not receive money.
Examples of Layer-5 (Session) implementation are Remote Procedure Call (RPC), Structured Query Language (SQL), UNIX Network File system (NFS), NetBIOS names, AppleTalk ASP, and DECnet SCP.
Layer-6: Presentation Layer
The Presentation layer defines data formats, such as ASCII text, EBCDIC text, binary, Binary Code Decimal (BCD), and Joint Photographic Experts Group (JPEG). Encryption also is a Presentation layer service. The Presentation layer is the only layer that can manipulate or change user data. This change is brought about when data encryption is implemented.
Examples of Layer-6 (Presentation) implementation are Tagged Image File Format (TIFF), Graphics Interchange Format (GIF), JPEG, Apple Macintosh Picture (PICT), American Standard Code for Information Interchange (ASCII), Extended Binary Coded Decimal Interchange Code (EBCDIC), encryption, Moving Pictures Experts Group (MPEG), Musical Instrument Digital Interface (MIDI), and HyperText Markup Language (HTML).
Layer-7: Application Layer
The Application layer is the user's interface to generate data for transmission using the application's communications services. For example, a standard word processing software package does not have communications capabilities, and therefore will not be concerned with communications requirements. However, e-mail applications, such as Microsoft's Outlook or Qualcomm's Eudora, are applications requiring communications and therefore will be enabled with communications capabilities.
Examples of Layer-7 (Application) implementation include File Transfer Protocol (FTP), World Wide Web (WWW) browsers, Telnet, UNIX Network File System (NFS), Simple Mail Transfer Protocl (SMTP) gateways (Eudora, cc:mail), Simple Network Management Protocol (SNMP), X.400 mail, and File Transfer Access and Management (FTAM).
EAN: 2147483647
Pages: 269