Tunneling Protocols
Tunneling is the second major component of a VPN. With the growth of dial-up services and the availability of many different protocols, a method was required to create a virtual dial-up scenario in which these non-IP protocols could take advantage of Internet connectivity. Cisco defined the concept of tunneling, which means the encapsulation of non-IP packets. Tunneling is used to encapsulate network protocols (TCP/IP, Novell IPX/SPX, AppleTalk, and NetBEUI) into an IP packet that can travel across the Internet.
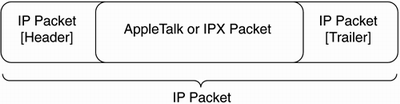
Tunneling is similar to sending an envelope with a postage stamp using an overnight service. The overnight service won't accept the first-class stamp for postage, so the envelope is packaged within an overnight envelope, which the overnight service will accept. Tunneled protocols operate in the same fashion. An AppleTalk or Internet Packet Exchange (IPX) packet cannot be sent across the Internet without being tunneled because the Internet is an IP network. Figure 16-2 illustrates what this tunneled packet looks like.
Figure 16-2. AppleTalk or IPX Packet Tunneled within an IP Packet
NOTETCP/IP could travel across the Internet on its own, but it would not be a part of the tunnel or the VPN, which means that it would be left unsecured. |
Technical Note: PPPTunneling protocols require an underlying infrastructure protocol, which is often the Point-to-Point Protocol (PPP). PPP is one of the most common access protocols in use today and is the default for most desktop operating systems. PPP is a suite of standardized protocols, much like TCP/IP, that provides the following features:
|
PPTP
The Point-to-Point Tunneling Protocol (PPTP) enables remote users to dial into a local Internet Service Provider (ISP) and tunnel across the public Internet to their respective corporate intranet server. PPTP uses PPP to establish the dial-up connection. Because of the reliance on PPP, PPTP uses encryption algorithms (PAP/CHAP) to provide encryption.
L2F
Cisco Systems developed Layer 2 Forwarding (L2F) to be used in combination with Microsoft's PPTP. After the PPP connection to the local ISP is made, L2F connects users to their corporation's intranet servers.
L2F enables the following:
Protocol independence (IPX, SNA)
Authentication (PPP, CHAP, TACACS)
Address management (assigned by destination)
Dynamic and secure tunnels
Accounting
Media independence (L2F over ATM, Frame Relay, X.25)
Both L2F tunneling and local Internet access
L2TP
Layer 2 Tunneling Protocol (L2TP) is to replace PPTP as the tunneling protocol of choice by such vendors as Cisco, Microsoft, 3Com, and others. L2TP is based on PPTP and the L2F protocol. L2F was designed by Cisco supporting the encapsulation of additional protocols, such as AppleTalk and IBM's Systems Network Architecture (SNA).
Like PPTP, L2TP relies on PPP to establish a dial-up connection; but unlike PPTP, L2TP defines its own tunneling protocol. L2TP uses PAP/CHAP for user authentication and allows for transportation of non-IP protocols (such as AppleTalk, SNA, or IXP).
NOTEL2TP is optimized for dial-up connections rather than site-to-site implementations. |
EAN: 2147483647
Pages: 269