LAN Characteristics
LAN Characteristics
LANs are grouped according to four key characteristics:
The types of transmission media over which they can operate
The transport technique they use to transmit data over the network (that is, broadband or baseband)
The access method, which is involved in determining who gets to use the network and when they get to use it
The topology, or mapping, of the network (that is, the physical and logical connections between the nodes on the network)
The following sections describe each of these four characteristics in detail.
LAN Transmission Media
Chapter 3, "Transmission Media: Characteristics and Applications," describes the advantages and disadvantages of the media types, and this section talks specifically about the considerations in selecting the appropriate media for a LAN.
First and foremost, as with selecting transmission media for metropolitan area network (MAN) or wide area network (WAN) environments, you need to think about bandwidth. You need to evaluate the kind of capacity you need: How much do you need per client? How much do you need per server? Typically servers require more capacity than clients because they service multiple simultaneous sessions, but some clients in an organization might use applications such as three-dimensional modeling and simulation and therefore require as much capacity as some of the shared servers. You should also evaluate the bandwidth based on traffic inside workgroups and traffic over the backbone between workgroups. Clusters or workgroups are made up of people who have the greatest community of interest, and therefore the majority of traffic sharing occurs within each cluster. However, there are reasons to have interdepartmental or interworkgroup communications as well, and therefore you need the backbone to provide connectivity between all the distinct clusters. So, the backbone should be engineered for great future capacity, and the workgroups should be set up so that they can easily be adjusted in the cases of moves, adds, and other changes.
The second consideration regarding LAN transmission media has to do with cost and ease of connectivity, and that speaks specifically to the installation, as well as to moves, adds, and other changes. In the average, rather stable, environment, at least 60% to 75% of the employees are relocated at least once a year, so equipment, features, and services must move along with them. And, of course, some environments have many reorganizations and require yet more consideration in this area. For example, in an enterprise where reorganization is common, a wireless LAN is probably the easiest way to support such a dynamic environment. The tradeoff is that wireless media provide less bandwidth than, say, fiber, and with a wireless LAN, you have to create smaller clusters. Again, what media you choose depends greatly on the application.
The third consideration regarding LAN transmission media is sensitivity to interference and noise. If a LAN is being deployed in a manufacturing plant where other equipment emits interfering levels of noise, the noise could play havoc with a twisted-pair or a wireless LAN, whereas coax and fiber would be much less susceptible to the interference.
Finally, of course, you need to consider security requirements. Again, there is no such thing as complete security, and each situation needs a different amount of security. You need to add encryption and other security mechanisms in almost any environment, but in some cases, you need to take the extra step of choosing a medium that's more difficult to tap into, such as coax or fiber.
Most of the LAN standards today support the full range of media types. They vary in terms of things such as the distances allowed between the devices and their backbones, so you need to choose the media that are appropriate given your situation.
LAN Transport Techniques
An important feature of a LAN is its transport technique: whether it is broadband or baseband (see Figure 8.2). Broadband means multichannel, so a broadband LAN implies that, through Frequency Division Multiplexing (FDM), multiple independent channels can carry analog or digital information, depending on the interfaces. This is essentially the way cable TV operates: There are multiple channels of programming, and each one runs over a different portion of the frequency band. When you request a particular channel from the interface device, the set-top box, the device selects the frequency band on which that channel is allocated. Cable TV is a multichannel coaxial system. The vast majority of LANs (probably 85% or so), however, are baseband LANs that use the Ethernet standard.
Figure 8.2. Broadband versus baseband
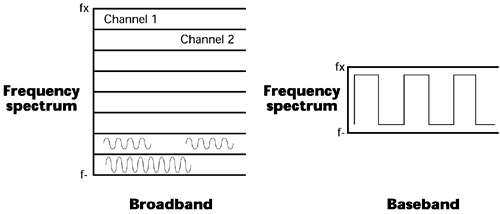
Table 8.1. Traditional LAN Standards | |||
| Characteristic | Ethernet | Token Ring | FDDI |
| Standard | IEEE 802.3 | IEEE 802.5 | ANSI X3T9.5 |
| Logical topology | Bus | Ring | Ring |
| Physical topology | Bus, star | Ring, star | Dual ring, dual bus |
| Media | Coax, UTP/STP, fiber | Coax, UTP, STP | Fiber |
| Transmission mode | Baseband | Baseband | Baseband |
| Bandwidth | 10Mbps, 100Mbps, 1000Mbps | 4Mbps, 16Mbps, 100Mbps | 100Mbps |
| Media access | Nondeterministic | Deterministic | Deterministic |
| Control | CSMA/CD, CSMA/CA | Token passing | Token passing |
Baseband implies a single-channel digital system, and this single channel carries information in containers that is, packets or frames that are specified by the LAN standard in use. The traditional LAN standards are Ethernet, Token Ring, and Fiber Distributed Data Interface (FDDI). Table 8.1 compares these three standards.
The most widely used of the baseband standards is Ethernet, which, as mentioned earlier, accounts for about 85% of the installed LAN base. IEEE 802.3 is the working group that creates the Ethernet standards. IEEE 802.3 defines the first generation of Ethernet (that is, 10Mbps); 802.3u defines Fast Ethernet (that is, 100Mbps); and 802.3z, which appeared at the end of 1997, defines Gigabit Ethernet (that is, 1Gbps). We're now awaiting 10Gbps Ethernet. Ethernet technology in general, but particularly Gigabit and 10Gbps Ethernet, is being considered as a very plausible solution for broadband in the local loop. You will increasingly see announcements about neighborhoods that will be testing this approach to creating what is essentially a high-bandwidth shared system. Token Ring originated in the IBM environment. It's specified under IEEE 802.5, and it appears as 4Mbps, 16Mbps, and 100Mbps. (The 100Mbps specification, called High-speed Token Ring, never gained acceptance in the marketplace.) Table 8.2 lists some of the most commonly used Ethernet LAN technologies and the cabling requirements for each.
Despite the fact that FDDI was the first LAN standard to provide 100Mbps for use in a backbone application, it did not capture a major market share. The transition to a higher grade of Ethernet is much simpler for companies than is a transition to an entirely new protocol.
Table 8.2. LAN Technologies and Cabling Requirements | |
| Technology | Type of Cable |
|
| Ethernet (10Mbps) |
| 10Base5 | Thick coax |
| 10Base2 | Thin coax |
| 10BaseT | 2-pair UTP |
| 10BaseFL | 2 strands of multimode optical fiber |
|
| Fast Ethernet (100Mbps) |
| 100BaseTX | 2-pair Cat 5 UTP |
| 100BaseT4 | 4-pair Cat 3 UTP |
| 100BaseT2 | 2-pair Cat 3 UTP |
| 100BaseFX | 2 strands of multimode optical fiber |
|
| Gigabit Ethernet (1Gbps) |
| 1000BaseSX | Short-wavelength multimode optical fiber |
| 1000BaseLX | Long-wavelength single-mode optical fiber |
| 1000BaseCX | Coax patch cable |
| 1000BaseT | 4-pair Cat 5 or Cat 5e UTP |
| 1000BaseTX | 2-pair Cat 6 (currently a TIA draft proposal) |
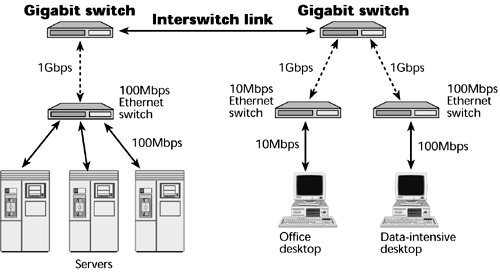
The prevailing standard in the world is Ethernet. It generally appears as Fast Ethernet or Gigabit Ethernet in the backbone, connecting together individual Fast Ethernet or 10Mbps Ethernet LAN segments (see Figure 8.3).
Figure 8.3. An example of Gigabit Ethernet
LAN Access Methods
The third main LAN characteristic is the access methods, which are involved in determining who gets to use the network and when they get to use it. There are two main approaches: token passing and carrier-sense multiple-access/collision detect (CSMA/CD).
Token Passing
Token passing is used with the Token Ring and FDDI architectures (see Figure 8.4). Here is how Token Ring works:
Figure 8.4. Token passing
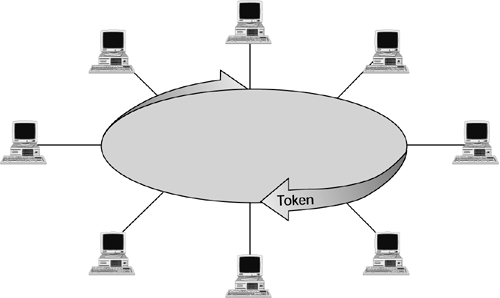
1. The active master, chosen through a process called beaconing, inserts a token (that is, specially formatted packet) into the ring.
2. The token circulates the ring and is regenerated by each workstation it passes. (In Token Ring networks, a workstation obtains data only from its upstream neighbor, regenerates it, and sends it to its downstream neighbor.)
3. When a workstation has data to send, it waits for the token to pass by and grabs it off the wire. The station then injects its data packets onto the wire.
4. The packets circulate the ring and are examined and regenerated by each workstation. Once the receiving workstation receives the packets, it marks them as received when it regenerates and reinjects them. This marking notifies the sender that the data was in fact received when it finally returns to the sender. The sender then generates a new token and injects it into the ring.
To prevent any particular workstation from hogging the ring, a transmitting station can hold the token (and thus transmit data packets) for a specific interval, called the token hold time. If the time expires before the station has transmitted all its information, it must stop transmitting and put a new token back on the ring so that other stations have a chance to communicate. When the token gets back to the waiting workstation, it can resume transmitting.
A benefit of token passing is that it is a deterministic technique: You can always calculate the maximum delay that you'll encounter in moving information between any two points on that network, and this is especially important for applications with defined response times, such as process control. For example, an oil pipeline may have sensors in the pipelines to detect minute leakage. The oil company wants to know exactly how long it will take for the alarm from the sensor to reach the control station to shut off the valve, in order to avoid leaking oil into the community. In a LAN where there's a need to determine the delay, token passing works very well. The disadvantage of token passing is that it occurs in a unidirectional ring, so it takes time to pass the tokens. A device has to wait until it receives a token before it can send it, and if the ring is broken because a device goes down, the ring is then unable to send tokens until the ring is recovered (that is, the failed device is either taken out of commission or reinitiated). Today, almost all Token Ring interfaces have an electrical shunt present to prevent this from happening.
CSMA/CD
CSMA/CD is used with the Ethernet standard. CSMA/CD is a nondeterministic access method, meaning that any device can send whenever it determines that the network is clear. However, each device must listen to the network at all times because there is the potential for a collision to occur. If a collision occurs, both sending devices back off the network and wait a random number of nanoseconds or milliseconds before attempting to retransmit.
Figure 8.5 shows an example of how CSMA/CD works:
Figure 8.5. CSMA/CD
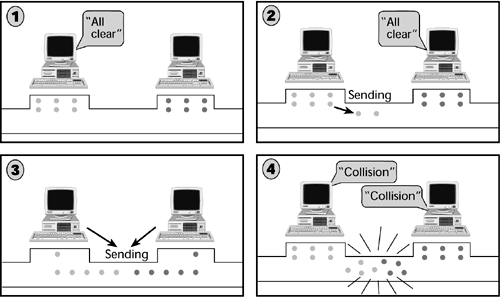
1. The terminals listen to the network.
2. Both of the terminals assume that the network is clear. They both start sending, but they continue listening because they know there's a chance that their messages will collide.
3. The messages do collide, so both terminals stop sending.
4. One terminal waits 20 milliseconds, and the other waits 50 milliseconds, and then they again attempt to transmit, assuming that their messages won't bump into each other. Because the terminals waited different amounts of time, most likely the messages don't collide and therefore get transmitted. However, if the messages collide again, the terminals repeat the back-off and random-wait procedure up to 16 times before the frames are dropped.
In this type of environment, the more devices you add and the greater the traffic volumes, the more likely collisions will occur. When collisions start to exceed the available throughput, you need to start segmenting the LAN into smaller clusters, called collision domains in Ethernet parlance, or consider making the move to switched Ethernet LANs.
LAN Topologies
The final characteristic of a LAN has to do with topologies the physical and logical mapping of the network. The most common LAN topologies are the tree, bus, ring, and star topologies, which are illustrated in Figure 8.6. The tree topology is commonly used in broadband LANs, and the bus, ring, and star topologies are used in baseband LANs. In today's environment, the most common physical topology is the star, and the most common logical topology that is, how the signals are exchanged between stations is the bus.
Figure 8.6. LAN topologies
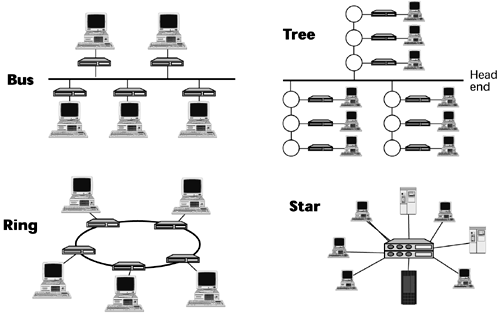
Tree Topology
In the tree topology, the root of the tree is the headend, or the central retransmission facility. The trunk cable is attached to this root. Various branch cables are attached to the trunk cable. From there, user devices can be connected. Although most broadband networks use a single cable, some use a dual-cable system one cable for each direction to and from the headend. All transmissions must pass through the headend because each device transmits on one frequency and receives on another. The headend is responsible for translating the device's transmit frequency to the receive frequency of another device, and this frequency translation is called remodulation.
Bus Topology
The bus topology, which is the oldest topology, functions like a multipoint circuit. All stations are attached via cable taps or connections to a single length of cable a wire with two open ends. The single cable is referred to as a trunk, backbone, or segment.
Each station can detect and place signals on the bus according to the access method. Only one computer at a time can send data on a bus network. Signals travel in both directions along the bus, from the point of insertion. Any other station on the network can receive a transmission from the station. Because the data is sent to the entire network, it travels from one end of the cable to the other. If the signal were to be allowed to continue uninterrupted, it would keep bouncing back and forth along the cable, preventing other computers from sending signals. Therefore, the signal must be stopped after it's had a chance to reach the proper destination address. A component called a terminator is placed at each end of the cable to absorb free signals and to clear the cable so that other computers can send data.
The bus topology is a passive topology. Computers only listen for data being sent on the network; they are not responsible for moving data from one computer to the next. An advantage of the bus topology is that it uses short cable lengths, and therefore it uses cable economically. Because the transmission media are inexpensive and easy to work with, the network is easy to extend. A disadvantage of the bus topology is that problems are difficult to isolate. A cable break can affect many users, and the network can become slow when traffic is heavy.
Ring Topology
In the ring topology, the nodes are connected by point-to-point links that are arranged to form an unbroken loop configuration. At each station the signal is received, regenerated, and transmitted to the next station on the ring, and data is transmitted in one direction around the ring. The ring is an active topology. That is, each computer acts like a repeater to boost the signal and send it on to the next computer. Because the signal passes through each computer, the failure of one computer can affect the entire network but in practice this rarely occurs, because the ring interfaces contain passive electrical shunts that allow the ring to remain intact in case a station is down or malfunctioning.
An advantage of the ring topology is that it can spread over long distances because each station regenerates the signal. Another advantage is ease of implementing distributed control and checking facilities; all computers have equal access, and the performance is even, despite the fact that there are many users. A potential disadvantage is sensitivity to station failures (that is, one failed station might break the ring). Also, problems in a ring network are difficult to isolate, and network reconfiguration disrupts the operation of the entire network.
Star Topology
In the star topology, all stations are connected by cable segments to a centralized component called a hub. Devices can communicate with each other only through the hub. The star topology offers centralized resources and management. The advantages of the star topology include ease of fault isolation, ease of bypassing and repairing faulty stations, and high cost-efficiencies. Also, it's much easier to modify or add new computers in a star network than to do so in other topologies. Disadvantages include the need for a lot of cable to interconnect all the stations and the potential for total network disruption if the central hub facility fails.
There are a number of variations on star networks. The star bus, for instance, is a combination of the bus and star topologies. It involves several star networks linked together with linear bus trunks. The star ring, sometimes referred to as the star-wired ring, looks similar to a star bus, except that the hubs in the star ring are connected in a star pattern and the main hub contains the actual ring.
EAN: 2147483647
Pages: 84