The OSI Reference Model and Protocols
The OSI Reference Model and Protocols
Before two computers or network devices can exchange information, they must establish communication, and this is where protocols come in. A network protocol enables two devices to communicate by using one set of rules. The OSI model and protocol standards help to ensure that networking devices are capable of working together over a network.
The OSI Reference Model
In the early 1970s, a problem was brewing. There were many different computer manufacturers, and there were many incompatibilities among them. Furthermore, each manufacturer created different product lines, and even within one company there were often incompatibilities between their product lines. So the International Standards Organization got involved and created the Open Systems Interconnection (OSI) reference model, which is a reference blueprint for device manufacturers and software developers to use when creating products.
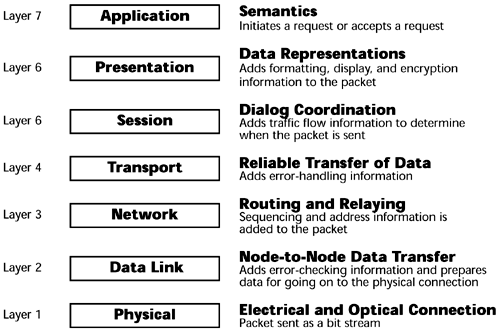
The OSI model, shown in Figure 6.8, has seven layers that describe the tasks that must be performed to transfer information on a network. When data is being transferred over a network, it must pass through each layer of the OSI model. As the data passes through each layer, information is added to that data. At the destination, the additional information is removed. Layers 4 through 7 occur at the end node, and Layers 1 through 3 are the most important to telecommunications networks.
Figure 6.8. The OSI reference model
It's important to understand that this model is exactly that a model. It's a conceptual framework that is useful for describing the necessary functions required of a network device or member. No actual networking product implements the model precisely as described.
Layer 7, the application layer, is responsible for exchanging information between the programs that are running on a computer and other services on a network. This layer supports application and end-user processes. It acts as a window for applications to access network services. It handles general network access, flow control, error recovery, and file transfer. Examples of application layer protocols include File Transfer Protocol (FTP), Telnet, Simple Mail Transfer Protocol (SMTP), and Hypertext Transfer Protocol (HTTP).
Layer 6, the presentation layer, formats information so that a software application can read it. It performs transformations on the data to provide a standardized application interface and common communication services. It offers services such as encryption, compression, and reformatting. The presentation layer adds a field in each packet that tells how the information within the packet is encoded. It indicates whether any compression has been performed and, if it has, it indicates what type of compression, so that the receiver can decompress it properly. It also indicates whether there has been any encryption, and if there has, it indicates what type, so that the receiver can properly decrypt it. The presentation layer ensures that the transmitter and receiver are seeing the information in the same format.
Layer 5, the session layer, supports connections between sessions and handles administrative tasks and security. It establishes and monitors connections between computers, and it provides the control structure for communication between applications. Examples of session layer protocols include NetBIOS, DSN, and Lightweight Directory Access Protocol (LDAP).
Layer 4, the transport layer, corrects transmission errors and ensures that the information is delivered reliably. It provides an end-to-end error recovery and flow control capability. It deals with packet handling, repackaging of messages, division of messages into smaller packets, and error handling. Examples of transport layer protocols include Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Sequenced Packet Exchange (SPX).
Layer 3, the networking layer, identifies computers on a network and determines how to direct information transfer over that network. In other words, it is a routing and relaying layer. It defines how to move information between networks as well as between devices. The key responsibility of this layer is to add the addressing information and the control functions needed to move the data through the network and its intermediate nodes. It is involved in establishing, maintaining, and terminating connections, including packet switching, routing, data congestion, reassembly of data, and translation of logical addresses to physical addresses. Examples of networking layer protocols are X.25, Internet Protocol (IP), Internetwork Packet Exchange (IPX), and Message Transform Program 3 (MTP3).
Layer 2, the data-link layer, groups data into containers to prepare that data for transfer over a network. It puts the ones and zeros into a container that allows the movement of information between two devices on this same network. The protocols at this layer specify the rules that must be followed in transmitting a single frame between one device and another over a single data link. Bits are packaged into frames of data, and they include the necessary synchronization, error control, and flow control information. Examples of data link layer protocols in a LAN environment include Ethernet, Token Ring, and Fiber Distributed Data Interface (FDDI). Examples of data-link layer protocols in a WAN environment include Frame Relay and ATM. Examples of data-link layer protocols within the PSTN are Signaling System 7 and MTP2.
Layer 1, the physical layer, defines how a transmission medium connects to a computer, as well as how electrical or optical information is transferred on the transmission medium. The physical layer defines the types of cables or wireless interfaces that are allowed, the voltage levels used to represent the bits or the optical levels, the types of connectors that are allowed, and the types of transmission rates that can be supported. Every network service and every network device has definitions at the physical layer in terms of what it can physically interface with. For example, the physical layer deals with unshielded twisted-pair (UTP) and shielded twisted-pair (STP), coax, 10BaseT (an Ethernet standard that allows the use of twisted-pair to support 10Mbps to the desktop), multimode fiber and single-mode fiber, xDSL, ISDN, and the various capacities in the PDH (for example, DS-1/DS-3, E-1/E-3) and SDH/SONET (for example, OC-1 through OC-192) networks.
Protocols and Protocol Stacks
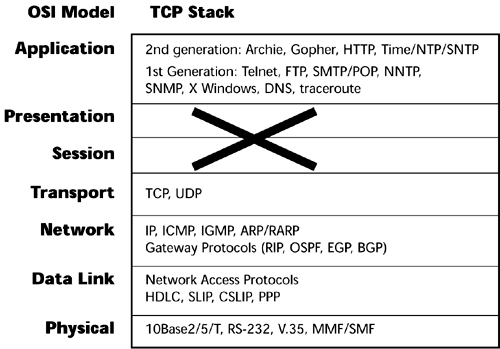
Protocols are the hardware or software components that carry out the OSI model guidelines for transferring information on a network. A protocol may be one component or a collection of components that carry out a task. A protocol stack, or protocol suite, is made up of multiple protocols that are used to exchange information between computers. One protocol in the stack might be used to specify how network interface cards (NICs) communicate, and another might specify how a computer reads information from the NIC. Figure 6.9 shows the TCP protocol stack and how it relates to the OSI model.
Figure 6.9. The OSI model versus the TCP/IP stack
For More Protocol InformationThe Web site www.protocols.com provides easy-to-understand information about protocols. |
A layer is a section of a protocol stack that is responsible for performing one particular aspect of information transfer. Because some protocols are capable of performing one function, one layer in a protocol stack may not necessarily correspond to one layer in the OSI model. Tunneling describes the process of using a protocol to transfer information through a network, using a different type of protocol.
| For more learning resources, quizzes, and discussion forums on concepts related to this chapter, see www.telecomessentials.com/learningcenter. |
EAN: 2147483647
Pages: 84