Questions and Answers
Lesson 1 Review
Page 5-15
| 1. | A user reports that he has changed his text size to Largest, but when he visits sites, sometimes the text on the sites is large and sometimes it is not. He reports this happens occasionally with colors and font styles, too. What does the user need to do to make sure these settings are always used, no matter what website he visits?
| |
| 2. | A small business owner wants to personalize the Internet Explorer title bar on the computer that visitors access when they come into her store. She also wants to configure a default home page that users cannot change. Which of the following commands is used on the Run line to open the appropriate application for configuring these computerwide settings?
| |
| 3. | A home user wants you to configure his computer running Windows XP so that his 12-year-old son cannot access websites that contain offensive language, nudity, sexual references, or violence that involves fighting or killing. He would like to be able to override those settings if ever necessary by using an administrator password. The user wants to spend the least amount of money possible. What should you tell the user to do?
| |
Answers
| 1. | A is the correct answer. B and C are not valid choices (because they do not exist) and are therefore not correct. D is a valid choice but will not override Web settings using the text size, fonts, and colors selected by the user. |
| 2. | D is correct because gpedit.msc opens the Group Policy console, and this console can be used to apply group policies computerwide. A is incorrect because this command opens the System Configuration utility. B is incorrect because sigverif.exe opens the File Signature Verification utility. C is incorrect because cmd.exe opens a command prompt. |
| 3. | B is the correct answer. Content Advisor, included with Windows XP, is an inexpensive way to control what sites and content are accessed on the Internet. A and C are incorrect because third-party software generally costs money and is not necessary in this situation. D is incorrect because digital certificates verify identity on the Internet; they are not used to judge or rate content. E is incorrect because the Profile Assistant is used only for identification purposes. |
Lesson 2 Review
Page 5-29
| 1. | Which of the following are indications of a full Temporary Internet Files folder? (Choose all that apply.)
| | ||||||||||
| 2. | Match the type of cookie on the left with its description on the right.
| | ||||||||||
| 3. | Company policy requires that all cookies saved to a user’s computer must have a compact privacy policy that conforms to P3P standards. No cookies shall be saved if they do not conform. Which of the following default privacy settings can be used? (Select all that apply.)
| |
Answers
| 1. | A, B, and C are correct. D is incorrect because a full Temporary Internet Files folder would imply that frequently accessed Web pages are cached. |
| 2. | 1. e. 2. c. 3. a. 4. b. 5. d. |
| 3. | E is the correct answer. The other settings do not require cookies to conform to P3P requirements. |
Lesson 3 Review
Page 5-45
| 1. | A company has placed a computer in a break room so that users can access it on their lunch and coffee breaks. How should the computer be configured? Choose all that apply.
| |
| 2. | You need to configure a security setting for the Internet zone for users who access websites from a computer located in the company’s lunchroom. Network administrators have configured Group Policy, physically secured the computer, and performed similar tasks and have asked you to configure a security level for the Internet zone that will apply the following rules by default:
Which security level offers these default settings for the Internet zone? | |
Answers
| 1. | A, B, and E are correct. Disabling AutoComplete and clearing AutoComplete settings protect users from others obtaining their user names and passwords. Disabling the installation of desktop icons keeps the desktop clean. C is incorrect because the way in which the Favorites list appears is not a security issue; D is incorrect because blocking all cookies will make many websites nonfunctional. |
| 2. | The High security level offers the desired settings. On the Security tab of the Internet Options dialog box, select the Internet zone, click Default Levels, and set the slider to High. |
Case Scenario Exercises: Scenario 5.1
Page 5-46
| 1. | All computers in your office have recently been upgraded from Microsoft Windows 98 to Windows XP. A clean installation was performed on each computer, and all service packs were installed. The installation went smoothly. However, the stockbrokers in your office are complaining that they are not getting up-to-date quotes when they visit their favorite, frequently viewed websites. They have been accessing these sites for two years without incident. What is most likely wrong, and how can this problem be resolved?
| |
Answers
| 1. | C is the correct answer. By default, temporary files are configured to look for newer versions of pages automatically, which is not as often as the stockbrokers need. A is incorrect because incompatible software would have been reported by Windows XP during the upgrade. The scenario states that the upgrade went smoothly. B is incorrect because, although a full Temporary Internet Files folder could cause problems, it would not cause problems on multiple computers at the same time. D is incorrect because the Temporary Files folder is accessible after a clean installation. |
Case Scenario Exercises: Scenario 5.2
Page 5-47
| 1. | A user reports that each time she accesses a particular website, she is inundated with content that she does not want to see, and she thinks this might have to do with ActiveX, Java applets, or scripts running on the site. The user reports that the site takes a long time to load, too. She wants to visit this site and read only the data; she has no interest in the other items on the site. You need to make this site available without making any changes to the default settings for the Internet zone. What should you do?
| |
Answers
| 1. | C is the correct answer. Adding sites to the Restricted Sites zone disables features such as ActiveX controls and Java. A and B are incorrect because these zones do not restrict websites but instead do just the opposite. |
Troubleshooting Lab
Page 5-47
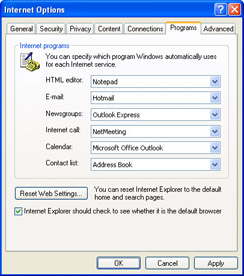
| 1. | You are working for a company that provides computer support for several small businesses. You get a call from a user who complains that she tries to send an e-mail message from within Internet Explorer; it creates a new message using Outlook Express. However, she uses Outlook as her e-mail software. She would like you to configure Internet Explorer so that she can create a message using Outlook. After talking with her for a few more minutes, you also find that she would like the following programs to be configured to work within Internet Explorer:
How would you configure these programs within Internet Explorer? | |
Answers
| 1. | You should configure these programs on the Programs tab of the Internet Options dialog box, shown in Figure 5-13. |
EAN: N/A
Pages: 237