Lesson 2: Supporting NTFS Permissions
As an administrator, you must give users appropriate access to files and folders while still protecting the computer as much as possible. You do this through the proper assignment of NTFS permissions. As the name suggests, NTFS permissions are available only on volumes that are formatted with NTFS. NTFS permissions allow you to control which user accounts and groups can access files and folders and specifically which actions the users can perform. NTFS permissions are in effect when users log on locally to the computer and when they connect to a resource across the network. As a DST, you must understand how NTFS permissions work and how to properly assign them to user accounts and groups.
After this lesson, you will be able to
-
Identify basic file and folder permissions.
-
Identify the default permissions on an NTFS volume.
-
Configure advanced file and folder permissions.
-
Calculate effective NTFS permissions.
-
Control NTFS permission inheritance.
-
Explain the effect on NTFS permissions when you move or copy files.
-
Explain the concept of file ownership.
-
Troubleshoot NTFS permissions.
Estimated lesson time: 40 minutes
Basic File and Folder Permissions
Every file and folder on an NTFS volume has a discretionary access control list (DACL) associated with it. The DACL contains the user accounts and groups that have been granted permissions to a resource and the specific permissions that have been granted. Each entry in the DACL is called an access control entry (ACE). A user account or a group that the user account is a member of must be listed as an ACE in the DACL for the user account to gain access to a resource. Otherwise, access is denied.
You will generally control file security by using basic folder permissions. Basic permissions allow users to perform the tasks that are most commonly required. Table 5-3 lists the six basic NTFS folder permissions.
| Permission | Tasks Allowed |
|---|---|
| List Folder Contents | User can view the names of files and subfolders in the folder, but this permission does not allow any access to the files and folders |
| Read
| User can see the files and subfolders of the folder and view the properties of the folder, including permissions, ownership, and folder attributes |
| Write | User can create new files and subfolders within the folder, change folder attributes, and view permissions and folder ownership |
| Read & Execute
| User can perform all actions that are allowed by the Read and List Folder Contents permissions and traverse folders (move through the folder to reach other files and folders that are further down in the hierarchy) |
| Modify | User can perform all actions that are allowed by the Write and Read & Execute permissions and delete the folder |
| Full Control | User can perform all actions that are allowed by the other basic permissions, assign permissions to other users, take ownership of the folder, and delete subfolders and files |
By default, a file’s DACL inherits the same entries as that of the parent folder. However, you can control permissions on individual files if necessary. Although file and folder permissions are similar to each other, there are some small differences. Table 5-4 lists the five basic NTFS file permissions.
| Permission | Tasks Allowed |
|---|---|
| Read | User can read the contents of the file and view the properties of the file, including permissions, ownership, and file attributes |
| Write | User can overwrite the file entirely (but not modify its contents), change file attributes, and view permissions and file ownership |
| Read & Execute | User can perform all actions that are allowed by the Read permission and run application programs |
| Modify | User can perform all actions that are allowed by the Write, Read & Execute permissions, and modify the contents of the file and delete the file |
| Full Control | User can perform all actions that are allowed by the other basic permissions, assign permissions to other users, and take ownership of the file |
Viewing NTFS Permission Assignments
You can view NTFS permissions on the Security tab of the Properties dialog box of any file or folder on an NTFS volume. If the Security tab is not visible, first verify that you are working on an NTFS volume. If the volume is formatted with NTFS and you still do not see the Security tab, the computer most likely has Simple File Sharing enabled (you will learn more about Simple File Sharing in Lesson 4, “Supporting Simple File Sharing”). You must disable Simple File Sharing to access the Security tab.
To view the NTFS permissions assignments of any file or folder, follow these steps:
-
In My Computer, locate the file or folder for which you want to view the NTFS permissions.
-
Right-click the file or folder and select Properties from the action menu.
-
Select the Security tab. Figure 5-6 shows the Security tab on the Properties dialog box of a folder named Data.
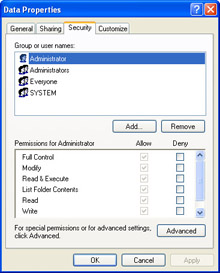
Figure 5-6: Use the Security tab of a folder’s Properties dialog box to assign NTFS permissions.
Objects gain permissions in one of two ways: a user specifically assigns permissions or the object inherits permissions from the parent folder.
| Note | When you are viewing permission assignments, Windows usually identifies a user account or group by name. However, if Windows cannot resolve the name, it displays the Security Identifier (SID) for the object instead. Windows can display the SID when the security principal is a domain account and the computer is disconnected from the network. |
Understanding Default Permissions On an NTFS Volume
When an NTFS volume is created, there are a series of default permission assignments. These assignments are listed in Table 5-5.
| Group or User Name | Permission Assigned |
|---|---|
| Administrators | Full Control to the root, subfolders, and files |
| CREATOR OWNER | Full Control to subfolders and files only |
| Everyone | Read & Execute to the root only |
| SYSTEM | Full Control to the root, subfolders, and files |
| Users | Read & Execute to the root, subfolders, and files Create Folders/Append Data to the root and subfolders Create Files/Write Data to subfolders only |
| Note | The default NTFS permission assignment in previous versions of Windows was to assign the Full Control permission to the group Everyone. This permission allows a significant level of access to all users. Windows XP Professional takes a more protective approach and assigns a much more limited set of permissions. |
You can add, edit, and remove NTFS permission assignments from the Security tab in the Properties dialog box of the file or folder.
To add basic file and folder permission assignments, follow these steps:
-
On the Security tab of the file or folder’s Properties dialog box, click Add.
-
In the Select Users Or Groups dialog box, enter the name of the object to be selected, as shown in Figure 5-7, and click OK. If you are unsure of the name of the object, click Advanced, select the object type and location, and click Find Now.
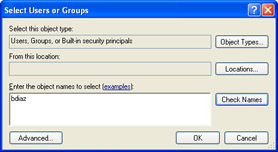
Figure 5-7: Add user accounts or groups by using the Select Users Or Groups dialog box. -
The default permissions assignments are Read & Execute and List Folder Contents (Folders Only). Modify the permissions as necessary by selecting or clearing the individual permission boxes and click OK or Apply.
When you assign permissions, the generally recommended rule is that you grant the user the lowest level of permission that is required to access the resource in the appropriate fashion. Granting Everyone the Full Control permission will always provide access and allow users to perform any task that they need to. However, granting the Everyone group Full Control can potentially give some users too much power, and a user can accidentally (or purposefully) change or delete files and folders, and even modify permission assignments. These actions can result in application program failures and data loss.
| Exam Tip | When you grant permissions, grant users the minimum permissions that they need to get their job done. |
Understanding Allow and Deny Permission Assignments
For each permission, you can choose one of two states: allow or deny. In most cases, you will allow specific permissions, which provide the user with the ability to perform the specified function. If a user is not allowed a particular permission, the user cannot perform that function. If a user is not allowed any permissions at all, the user cannot access the resource.
Deny permissions, which prevent a user from performing the specified function, are used in only special circumstances. An example of deny permission usage is as follows: if a user is a member of one or more groups that has been granted permission to access a resource, but you do not want that particular user to access the resource, you can assign deny permissions to that user. The deny permission overrides the allow permission that is assigned to the group, and the user is prevented from accessing the resource. Combining different types of permissions is discussed in more detail in the section titled “Calculating Effective NTFS Permissions” later in this chapter.
Basic Permission Relationships
When selecting basic permissions, additional permissions are automatically selected in some cases. This situation occurs when the selected permission includes the actions of another permission. Table 5-6 describes these permission relationships.
| Selecting This Permission | Automatically Includes These Permissions |
|---|---|
| Read & Execute | List Folder Contents (Folders Only) and Read |
| Modify | Read & Execute, List Folder Contents (Folders Only), Read, and Write |
| Full Control | Modify, Read & Execute, List Folder Contents (Folders Only), Read, and Write |
Advanced File and Folder Permissions
Although you can manage most permissions assignments by using basic file and folder permissions, sometimes you need to work with advanced permissions. Advanced permissions allow you to assign specific and potentially unusual levels of permission. An example of an advanced permission assignment is granting a user the ability to read the attributes (properties) of a file without being able to open the actual file.
To add advanced permission assignments, follow these steps:
-
In the Security tab of the file or folder’s Properties dialog box, click Advanced. The Advanced Security Settings dialog box appears, as shown in Figure 5-8.
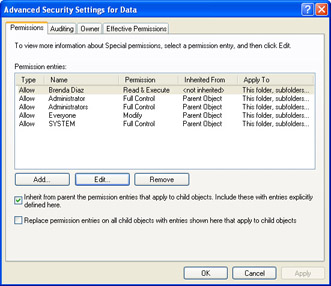
Figure 5-8: Use the Advanced Security Settings dialog box to configure advanced permissions. -
Click Add. Select the appropriate users and groups, and then click OK to continue.
-
The Permission Entry dialog box appears next. Notice that there is no default permissions assignment.
-
Modify the permissions as necessary and click OK. You will return to the Advanced Security Settings dialog box.
-
Click OK again to return to the Security tab.
Note If you highlight users or groups in the Security tab and they have no basic permissions assigned to them, they have an advanced permissions assignment.
Calculating Effective NTFS Permissions
A user can receive NTFS permissions from multiple sources. You can assign permissions directly to a user, permissions can be inherited from a parent folder, or a user might receive permissions based on group membership. Effective NTFS permissions are the permission levels that a user actually has after combining the permissions from all sources.
The rules for calculating effective permissions are as follows:
-
Allow permissions from all sources are combined, and the user receives the highest possible level of permission.
-
Deny permissions override allow permissions.
-
If a user has not been assigned any permission from any sources, access is denied.
The following sections provide several examples of effective permission calculations. In all cases, we are looking at permissions for the user JSmith, who is a member of the Managers, IT, and Everyone groups.
Calculating Allow Permissions
When calculating effective permissions, allow permissions from all sources are combined, and the user receives the highest possible level of permission. However, if the user has not been assigned permissions from any sources, access is denied. Table 5-7 illustrates several examples of combining allow permissions and the resulting effective permissions.
| Example Number | User or Group | Allow Permissions Assigned to User or Group | JSmith’s Effective Permission |
|---|---|---|---|
| 1 | JSmith (user) Managers (group) IT (group) Everyone (group) | (None assigned) Modify Write Read | Modify |
| 2 | JSmith (user) Managers (group) IT (group) Everyone (group) | Read Full Control (None assigned) Write | Full Control |
| 3 | JSmith (user) Managers (group) IT (group) Everyone (group) | (None assigned) (None assigned) (None assigned) (None assigned) | Access Denied |
The effective permission calculations in Table 5-7 are as follows:
-
Example 1 Modify is the highest level of permission assigned to the user or any group the user is a member of, and is therefore the effective permission.
-
Example 2 Full Control is the highest level of permission assigned to the user or any group the user is a member of, and is therefore the effective permission.
-
Example 3 No permissions have been assigned to the user or any group the user is a member of. The user cannot access the resource.
These types of calculations are fairly simple and are most likely the types of calculations that you will need to perform.
Determining the Effect of Deny Permissions
Deny permissions override allow permissions. If a deny permission has been assigned to the user or to any group that the user is a member of, that permission is denied. When the permission is denied, any related permission will also be denied (refer to Table 5-6 for permission relationships). Table 5-8 provides two examples of the way effective permissions are calculated when deny permissions are involved.
| Example Number | User or Group | Allow Permissions Assigned to User or Group | JSmith’s Effective Permission |
|---|---|---|---|
| 1 | JSmith (user) Managers (group) IT (group) Everyone (group) | Write–Allow Read–Deny (None assigned) Full Control–Allow | Write |
| 2 | JSmith (user) Managers (group) IT (group) Everyone (group) | Full Control–Deny Write–Allow (None assigned) Read–Allow | Access Denied |
The following points demonstrate effective permission calculations for the scenario outlined in Table 5-8:
-
Example 1 The group Managers is denied the Read permission. The Full Control permission assigned to the group Everyone is also denied because Read is related to Full Control. The Write permission allowed to JSmith is allowed because it is not related to the Read permission. The effective permission is therefore Write.
-
Example 2 JSmith is denied Full Control. The Write permission assigned to Managers and the Read permission assigned to Everyone is also denied because they are related to Full Control. Access is denied because no permissions have been allowed.
Calculation of effective permissions when deny permissions have been applied is difficult. Because it is easy to make a permissions assignment error when deny permissions are involved, it is recommended that you do not assign deny permissions except when you have no alternative.
Viewing Effective Permissions
Windows XP contains an Effective Permissions tab in Advanced Security Settings. This is a new feature that was not available in earlier versions of Windows.
To view the effective permissions for a user or group, follow these steps:
-
In the Security tab of the file or folder’s Properties dialog box, click Advanced.
-
In the Advanced Security Settings dialog box, select the Effective Permissions tab.
-
Click Select, choose the user or group for whom you want to view effective permissions, and then click OK. The effective permissions are displayed, as illustrated in Figure 5-9.
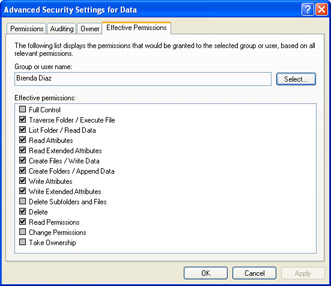
Figure 5-9: Windows XP can display the effective permissions for a user or group.
Controlling NTFS Permission Inheritance
By default, when you assign to a parent folder, all files and folders in the parent folder inherit those permissions automatically. However, you can control inheritance at either the parent or child level.
To control permission inheritance on a per-user basis at the parent folder, follow these steps:
-
On the Security tab of the parent folder’s Properties dialog box, click Advanced.
-
In the Advanced Security Settings dialog box for the parent folder, on the Permissions tab, select the user account or group for whom you want to control permissions inheritance, and then click Edit.
-
In the Permission Entry dialog box for the user account or group, shown in Figure 5-10, use the Apply Onto drop-down list to select one of the options listed in Table 5-9 and then click OK.
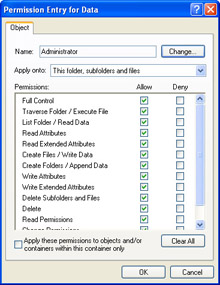
Figure 5-10: Control permissions inheritance at the level of the parent folder.Table 5-9: Controlling Inheritance from the Parent Folder Permission
Tasks Allowed
This Folder Only
Grants permissions for the folder but none of the files or subfolders within it.
This Folder, Subfolders And Files
Grants permissions for the folder and allows those permissions to inherit to all files and subfolders within the folder. This is the default inheritance setting.
This Folder And Subfolders
Grants permissions for the folder and allows those permissions to inherit to subfolders only. Files do not inherit the permissions.
This Folder And Files
Grants permissions for the folder and allows those permissions to inherit to files only. Subfolders do not inherit the permissions.
Subfolders And Files Only
Does not grant permissions for the folder, but allows the permissions to be inherited by files and subfolders within the folder.
Subfolders Only
Does not grant permissions for the folder, but allows the permissions to inherit to subfolders within the folder only.
Files Only
Does not grant permissions for the folder, but allows the permissions to inherit to files within the subfolder only.
-
In the Advanced Security Settings dialog box, click OK.
-
In the Properties dialog box for the folder, click OK.
To block inheritance from a parent folder at the level of a child file or folder, follow these steps:
-
On the Security tab of the child file or folder’s Properties dialog box, click Advanced.
-
Clear the Inherit From Parent The Permission Entries That Apply To Child Objects check box.
-
In the Security dialog box that opens, choose one of the following options:
-
Copy The permissions that the child object is inheriting are retained, but future inheritance from the parent folder is not allowed.
-
Remove The permissions that the child object is inheriting are removed, and future inheritance from the parent folder is not allowed.
-
Cancel Cancels the action without affecting any inherited permissions or affecting future inheritance.
-
-
In the Advanced Security Settings dialog box, click OK.
-
In the Properties dialog box for the child object, click OK
Moving and Copying Files
When you move or copy files and folders on NTFS volumes, permissions can be affected. The following basic rules apply:
-
When you copy files or folders to a new location, the objects do not retain permission assignments. The file or folder inherits permissions from the new parent folder.
-
When you move files or folders within an NTFS volume, the objects retain permission assignments. However, inherited permissions are left behind. Permissions will be inherited from the new parent.
-
When you move files or folders between NTFS volumes, the objects do not retain permission assignments. The file or folder inherits permissions from the new parent folder.
-
When you move or copy files or folders to a FAT or FAT32 partition, all NTFS permission information is lost.
Exam Tip When you move files or folders within an NTFS volume, permissions that have been directly assigned to the file or folder carry over to the new location. In all other cases, existing permissions are lost, and the object will inherit permissions from the new parent.
Understanding Ownership
By default, the owner of a file, folder, or printer is the user who created it. The owner of a resource has the ability to grant permissions and share the resource, thereby controlling access. Ownership guarantees the ability to perform these functions whether or not the owner has been granted any other level of permission.
Administrators are granted the user right to take ownership of any resource, which ensures that the administrators can always control access to all resources on the computer. Most likely, an administrator takes ownership in situations in which the current owner has left the organization and the administrator needs to gain control of the resource to manage it.
Users who are not administrators can take ownership if they have been granted the Take Ownership special permission, which is included with the Full Control file or folder permission and the Manage Printers printer permission. To view ownership and to take ownership of a file, folder, or printer, complete the following steps:
-
On the Security tab of a file or folder’s Properties dialog box, access the Owner tab. You can view the current owner, as shown in Figure 5-11.
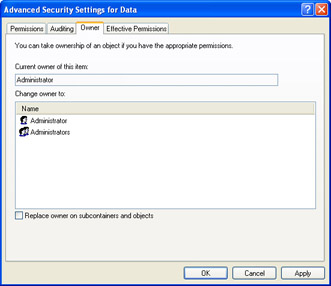
Figure 5-11: Use the Owner tab in the Advanced Security Settings dialog box to view and take ownership. -
The Change Owner To section displays user accounts that have permission to take ownership of the object. If you are a member of the Administrators group, you have the option to change ownership to either your user account or the Administrators group.
-
Click OK.
Troubleshooting NTFS Permissions
You are working at your company’s help desk supporting users who call in with problems. You have just finished resolving a logon problem call from a user who could not log on by using her user name and password. You determined that she needed to log on by using her domain credentials instead of her local user account credentials. The user has now called back and the call is forwarded to you for resolution. She tells you that she can log on without a problem; however, she cannot access some files on her local computer that she created while working from home. These files are necessary for a presentation that she is giving in one hour, and she has no time to create the information again. What can you do to help this user?
One of the biggest challenges that users encounter with permissions is knowing what the current permissions are. Whenever you work with permissions, you must take the following items into account:
-
Permissions are inherited from above in the folder hierarchy.
-
Permissions are cumulative, except for the deny permission.
-
Permissions are assigned to users and groups.
-
Windows XP computers that are members of a domain have two lists of users and groups: the local user accounts and the domain user accounts.
-
The user who creates a new file or folder becomes the CREATOR OWNER who has Full Control of that object.
To resolve the caller’s problem, you must determine the assigned permissions that are on the files, usually by examining the Security tab in the file’s Properties dialog box. After you determine the permissions, you need to assign the appropriate permissions based on the user’s needs.
Based on this caller’s symptoms, you should suspect that when the user logged on to the local computer, she accessed those files using a local user account. Now that she is logging on to a domain, her domain user account does not have the necessary permissions to access the files. She should log on to the computer locally (or have an administrator do so) and grant her domain user account the permissions necessary to access the files.
Practice: Configuring NTFS Permissions
In this practice, you will identify the NTFS permissions assigned to a folder, assign NTFS permissions to a user, and view the effective permissions for a user.
| Note | These practices require that you have a computer running Windows XP Professional and that you have a volume formatted using NTFS. You must also have disabled Simple File Sharing. |
Exercise 1: Identify the NTFS Permissions That Are Assigned to a Folder
-
Log on to Windows XP using an account with administrator privileges.
-
From the Start menu, right-click My Documents and select Properties.
-
In the My Documents Properties dialog box, select the Security tab.
-
List the user accounts and groups that are assigned permissions to the My Documents folder, and list the specific basic permissions assigned to each account.
Exercise 2: Assign NTFS Permissions to a User Account
-
Log on to Windows XP using an account with administrator privileges.
-
From the Start menu, right-click My Documents and select Properties.
-
In the My Documents Properties dialog box, on the Security tab, click Add.
-
In the Select Users Or Groups dialog box, in the Enter The Object Names To Select window, type Guest and click OK.
-
In the My Documents Properties dialog box, on the Security tab, in the Group Or User Names window, select the Guest account.
-
In the Permissions For Guest window, clear the Allow check boxes for all except the Read permission.
-
Click Apply. The Guest account now has Read permissions on the My Documents folder. Do not yet close the My Documents Properties dialog box.
Exercise 3: View the Effective Permissions for a User
-
In the My Documents Properties dialog box, click Advanced.
-
In the Advanced Security Settings For My Documents dialog box, on the Effective Permissions tab, click Select.
-
In the Select User Or Group dialog box, in the Enter The Object Name To Select window, type Guest and click OK.
-
In the Advanced Security Settings for My Documents dialog box, in the Effective Permissions window, note the effective permissions for the Guest account. Click OK.
-
In the My Documents Properties dialog box, in the Group Or User Names window, select the Guest account and click Remove. Click OK.
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and try the question again. You can find answers to the questions in the “Questions and Answers” section at the end of this chapter.
-
List the basic folder and file permissions.
-
A user wants to configure NTFS permissions on a folder that contains personal information. Following your instructions, the user opens the Properties dialog box for the folder in Windows XP, but does not see a Security tab. What might this situation indicate?
-
You are moving a folder named Old to a folder named New on the same volume. The volume is formatted using NTFS. Which of the following is true?
-
The permissions on the folder named Old remain intact.
-
The folder named Old inherits the permissions of the folder named New.
-
All permissions on the folder named Old are lost.
-
The permissions on the folder named Old revert to the default permissions for a new folder.
-
Lesson Summary
-
Every file and folder on an NTFS volume has a discretionary access control list (DACL) associated with it. The DACL contains the user accounts and groups that have been assigned permissions to a resource and the permissions that have been granted. Each entry in the DACL is called an access control entry (ACE). A user account or a group that the user account is a member of must be listed as an ACE in the DACL for the user account to gain access to a resource.
-
Basic file and folder permissions include: List Folder Contents, Read, Write, Read & Execute, Modify, and Full Control.
-
When assigning permissions, you should grant the user the lowest level of permission required to access the resources in the appropriate fashion.
-
For each permission, you can choose one of two states: allow or deny. In most cases, you will allow specific permissions, which will provide the user with the ability to perform the specified function. When you deny a permission, that denial overrides any allowances of the same permission that may come from other sources.
-
When you calculate effective NTFS permissions, you should combine all allowed permissions. A denied permission always overrides an allowed permission.
EAN: N/A
Pages: 195
- Integration Strategies and Tactics for Information Technology Governance
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Managing IT Functions