Authenticating Users
IIS offers several approaches for authenticating users, and ASP.NET works with all of them. The choices that we will discuss are anonymous, certificate, and Windows Authentication. These comprise the top-level choices in IIS for securing resources. First we’ll discuss what these options are and examine how they are configured, and then we’ll look at how ASP.NET fits in.
IIS Authentication
ASP.NET requests are first handled by the Web server, which usually means IIS. The dialog box in which IIS security settings can be set and viewed is accessed from the Computer Management application for managing local and remote computers by following these steps:
-
Expand the Services And Applications area of the Computer Management, part of the Microsoft Management Console.
-
Click on Internet Information Services.
-
Right-click the Web site (such as Web Sites or Default Web Site) or application root, and select the Properties option.
-
Click the Directory Security tab.
-
Click the Edit button for Anonymous Access And Authentication Control. Figure 8-2 shows the Authentication Methods dialog box.
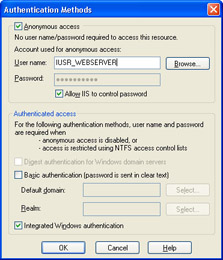
Figure 8-2: Authentication Methods dialog boxTip To launch the Computer Management application from the command prompt, enter start compmgmt.msc. You can also launch the Internet Information Services Management snap-in directly by entering start inetmgr.
Anonymous Access
The default mode in IIS is anonymous access, meaning that all users are allowed access to the site and are assigned the IUSR_WebServer identity, where WebServer is the machine name of the Web server. The IUSER_WebServer identity is a real user account on the Web server machine, but it has very limited permissions; although we’ve assigned the user’s identity, we haven’t authenticated who he is.
Client Certificates
Another option for authentication is the use of client certificates, in which the Windows accounts are mapped to certificates as part of user management and application configuration. Then, during authentication, the certificate is presented by the browser and validated by the Web server. The client does not need to present user credentials (the user name and password) because the certificate exchange happens automatically. (You can find more information on mapping certificates at http://www.microsoft.com/technet. Search for the topic “Mapping Certificates.”)
Windows Authentication
The other main option for authentication in IIS is referred to as Integrated Windows Authentication. Windows Authentication also has several other suboptions: basic and digest. Both authenticate credentials presented by the user or the user’s browser are verified against a Windows account on the server. Basic Authentication allows the user name and password to be sent without encryption and must be used on a user account that is defined explicitly on the Web server machine. Someone capturing network traffic would be able to see the user name and password.
| Important | Never use Basic Authentication without requiring Secure Sockets Layer (SSL) so that user credentials are sent in an encrypted form. Using basic authentication without encrypting communications is referred to as sending credentials “in the clear” and is a very bad practice. |
Digest Authentication looks like Basic Authentication to the user but requires that the user account be a domain account. The user is presented with a dialog box that enables her to enter her user name and password. Digest Authentication encrypts the credentials before transmitting them to the Web server so that they are not sent in the clear, that is, their transmission requires an SSL connection.
Integrated Authentication utilizes the credentials the user obtained when she logged on to the machine. The user is not presented with another dialog box, and the password is not sent to the Web server. Depending on the environment, integrated authentication will use either Kerberos or NTLM to establish the domain identity of the user.
Before a request is handed over to ASP.NET, it is authenticated using one of these Windows authentication options by IIS. When ASP.NET receives the request, IIS always passes the identity of the Windows user along with it. This identity might be the anonymous user account (IUSER_WebServer), a local machine account, or a domain account.
| Tip | A Windows user account is always associated with an executing request. A good way to review the security of a Web application is to walk through what identity is being used by Windows when executing any part of the request. |
ASP.NET Authentication
Once the request is handed over to ASP.NET along with the user credentials provided by IIS, the additional authentication options of ASP.NET come into play. These options are driven primarily by scenarios in which having a Windows account for each user of the Web application is not feasible. The ASP.NET authentication options are set in the authentication element of the web.config file. Settings in the web.config file will override the default settings in the machine.config file. An example of using the authentication element is seen in Code Listing 8-2. There are four possible values for the mode attribute of the configuration element: Windows, Forms, Passport, and None.
The default ASP.NET authentication mode is Windows, meaning that File Authorization and URL Authorization are carried out using the Windows user account provided by IIS. (See the section in this chapter titled “Authorizing Users” for more information). Access to backend resources, such as databases and registry entries, is performed using the identity of the worker process. (See the section titled “Using Impersonation” later in this chapter.)
When the authentication mode is Passport, the user is denied access to the directory until he has been authenticated by the Microsoft Passport Authentication service. This service essentially wraps the calls with the Passport SDK for you, automating the process of logging the user into Passport. (For more details on the .NET Passport authentication service, go to http://www.microsoft.com/net/services/.)
The Forms Authentication mode of ASP.NET is the most popular for enabling authentication that doesn’t require a Passport login or a separate Windows account to be maintained on the server. We’ll discuss it in more detail in the “Using Forms Authentication” section later in this chapter.
EAN: 2147483647
Pages: 144
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XVII Internet Markets and E-Loyalty