Project Tasks in the Transition Phase
| As the project heads into the Transition phase, a number of development tasks remain. These include deploying the IOC, online help, installation scripts, final change requests, and data migration. Other tasks, such as training and acceptance testing, remain as well. I will discuss each of these separately. Deploying the IOCWhen the IOC milestone is reached and the Transition phase begins, the goal is to make the deployment of the new system as painless and smooth as possible. A major risk-reduction activity during the Transition phase is an early deployment of the IOC. This is often called a beta release. The following summarizes the goals and purposes of deploying a beta release:
Although these are clearly important advantages, early deployment as a beta release does present some risks. If you plan an early deployment, be careful to monitor and plan to mitigate the following risks:
Despite the challenges, early deployment testing is an important risk-reduction activity that should be performed. Online HelpThe first step in producing online help is to examine your system's requirements. Do the requirements specifically ask for online help? If so, what do they state? Even if you have no requirements for online help, the reality is that most users expect some form of online help to guide them in their usage of the system. Hopefully, the analysts on the project have uncovered and documented these requirements. Accordingly, the creation of online help would then be scheduled for an iteration in the Transition phase. The Iteration phase is not the appropriate place to discover for the first time the requirements for online help. Although "online help" sounds simple enough, it can range from simply making an online copy of a user manual available from the product's user interface, to a fully functional tutorial involving sample exercises and canned demonstrations illustrating how the user interacts with and uses the product. Creating online help can, therefore, be a major task and should be planned in an iteration just like other major portions of functionality. Remember that online help is likely to be heavily used initially, until the end users become comfortable using the product. As discussed previously, this feature is highly visible to end users and will shape their experience with the product. Installation ScriptsInstallation scripts are another example of a task that is conceptually simple yet can be extremely complex to implement. Here are some considerations for determining how to structure the installation procedures:
Change RequestsUp until the Transition phase, the team has focused primarily on high-priority change requests. This means that lower-priority change requests, such as typographical errors and minor formatting changes on the user interface, have been accumulating. The Transition phase is the time to complete as many of these lower-priority requests as possible. These change requests are often items very visible to end users. An investment of time to correct these change requests will pay dividends in increased customer satisfaction. Exercise caution in expending resources on change requests involving requirements that significantly alter the system's behavior or its business rules. Chances are when the system is fielded for the first time, there may be high-priority change requests, which are much higher in importance. The focus in Transition should be to make the system rollout as successful as possible, which means that a stable, bug-free release is the goal. Data MigrationData migration is another example of a task that is conceptually simple but that in practice is complex and tedious. Simply stated, the purpose of data migration is to move data that currently resides in legacy systems into a new system. In some cases, more than one legacy system may exist, such as when a newly developed system replaces multiple legacy systems. In most cases, this data represents core business knowledge or information that must be preserved. Often, this data represents an asset that has been built and accumulated over many years. As a consequence, the organization places a very high value on this data, and its integrity must be preserved when it is migrated to the new system. Overview of the Steps in Migrating DataData migration involves a series of steps. These are summarized next and in Figure 12-1, followed by a detailed discussion of each step. Figure 12-1. Overview of data migration steps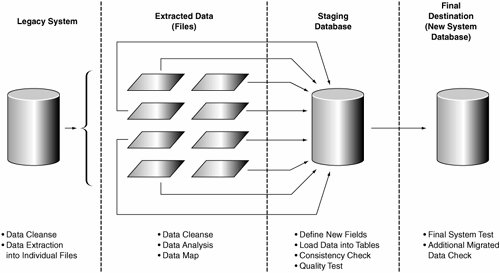
Details of Data Migration StepsAs just mentioned, data migration is a tedious process. The key to success in a data migration effort is careful planning and starting long before the "official" migration begins. Because of the importance of this activity, I will discuss each step in detail. Planning a Successful Data Migration EffortData migration by itself is a significant project. Like any other project, it requires resources, careful planning, and the setting of client expectations. It also involves significant risks that must be mitigated. The following are important points to consider when planning a data migration effort:
Shutting Down Legacy Systems to Extract DataDuring off-hours, or during maintenance, a recent snapshot of the data is sufficient in most cases for trial runs. Of course, for the final migration, the legacy system needs to remain down so that changes will not be made to the data during the switchover to the new system. Depending on the use of the system, this may require months of advance notice, especially for a mission-critical system. It may also be necessary to conduct the final migration over a holiday weekend. Prepare the staff conducting the data migration accordingly. If several trial runs using recent snapshots of the legacy system have been conducted, and the system has been tested with this data, there is an excellent chance that the migration effort will proceed successfully. However, be prepared to place the legacy system back into production if the migration effort fails. The goal, of course, is to place the new system into production; however, preserve the option of returning the legacy system into production as a fallback position. As mentioned previously, trial runs of the data migration are mandatory. Another reason for conducting trial runs is that it helps produce a reliable estimate of the total amount of time the final migration effort will take. This is key, because neither the legacy system nor the new system will be available during the final migration effort. Because this is not a trivial situation for most organizations, it is vital to know ahead of time how much time needs to be allocated for the final migration. Extracting the Legacy DataDepending on the type of system in which the legacy data resides, methods for extracting the data will vary. If possible, automated scripts should be developed for this purpose, because extraction of the data will probably occur multiple times. The data should be stored in files that can be viewed and examined. Note that depending on the customer and the application, significant security concerns might be involved. Be sure to discuss any concerns about security and access to the data during the migration process with the customer ahead of time. Addressing these concerns beforehand minimizes disruptions during the process. Depending on the amount and types of data stored in the legacy database, it may be necessary to extract the data in phases. Data CleansingData cleansing involves a thorough check of the data extracted from the legacy system. The data is modified when data meeting certain attributes is located. Examples include eliminating duplicate data, deleting obsolete or unused data, and even repairing corrupted data records. Most of this effort is done from the perspective of the legacy system. In other words, no consideration is given to the ultimate destination of the final migrated data. It is simply a "cleanup" effort that yields a "purified" set of data that still works perfectly in the legacy system. You must perform this step in close collaboration with users who are familiar with the data. Sometimes, depending on circumstances, it may make sense to perform the cleansing step before you extract the data from the legacy system. The point is to examine all data records and purge any that are unnecessary. Analyzing the Cleansed DataAnalyzing the cleansed data is perhaps the most painstaking step of the data migration effort. Each field of data must be traced to a corresponding field in the destination database. If a data model has been created, it will become very useful in this step. During this step, the data is also analyzed for consistency. One example of inconsistent data is illustrated in the following example, which occurred on an actual project. A Web-based system was developed that was to contain a centralized database with a Web interface that could be accessed over the organization's internal network, which reached nationwide. The system was replacing a former client/server system in which the user community was divided into separate regions. Each region contained its own database. The format and layout of the database were the same for each database across all the regions. These databases were to be consolidated into a single database for the new system. The issue happened over the disposition of a field indicating which region the data belonged to. It turned out that two different regions were using the same value to indicate the region they belonged to. Previously, this had not caused any problems, because each region had its own separate database. But when consolidating the databases, it was definitely a problem. There was no way to distinguish between the two regions after the data was consolidated. This is a good example of data consistency. In this example, the data in both databases is perfectly valid. But during the analysis, the problem is discovered. In this situation, the solution, of course, was to change the value for one of the regions so that each region was using a unique value. Another scenario that requires extra diligence frequently occurs when you replace a legacy system that has been running for many years. In one case, analyzing the cleansed data revealed inconsistencies in the format of the data records prior to a certain date. It turned out that the legacy system being replaced had previously replaced yet another legacy system. This occurred before most of the users joined the organization, so no one recalled this event. The lesson learned was to be sure to investigate each instance of the data that does not conform to the expected parameters. Yet another example encountered on a project involved replacing a mainframe-based legacy system. In this system, the database contained a customer name. The mainframe database defined a single string to contain the customer's entire name. The new system defined separate fields for each component in the customer name. The data migration effort involved writing scripts to parse the string from the legacy system to place it in separate fields in the new database. These are typical examples of issues that can arise. Of course, each migration effort is different. Be prepared to discover these sorts of scenarios. Transferring the Legacy DataFor simple systems, cleansed, analyzed data can be imported directly into the final destination database. For most systems, the data's complexity may not permit this. In addition, consider the original system managing the legacy data. If the legacy system uses an earlier release of Oracle, and the new system also uses Oracle (albeit a newer release), you are less likely to run into data representation problems. On the other hand, if the legacy system is a database management system from a different vendor running on a completely different type of system, you should consider setting up an intermediate database to "stage" the data. For example, suppose the legacy system runs on a mainframe system running MVS and the new database system runs on UNIX. In this example, you are much more likely to run into data representation problems than in the Oracle example. Two significant variables are involved: the change in platform and the change in database vendors. Figure 12-1 showed a staging database being used to assemble the data after it is cleansed. Each extracted table can be individually imported into the staging database, which is created on the same platform and using the same database vendor and version as the final production system. After it is loaded into the database, the data is examined to ensure that it is consistent and that the new system will interpret it correctly. Automated scripts and utilities are recommended to load the data into the destination databases. This allows multiple runs for importing the data, which is necessary to ensure a smooth migration effort when the final migration to production occurs. Testing the Migrated DataAt each step, the data should be examined for consistency and to ensure that it has no corrupted records or missing data. The scripts that perform the data transfer must also be tested, like any other developed code. When the data is transferred to the final database, the database engineer should meet with a user or group of users who are familiar with the data. Together, they should spot-check several meaningful scenarios to gain confidence in the migration's success and to ensure readiness for production. Points to Remember for the Data Migration EffortYou should now appreciate the complexity of most data migration efforts. Remember the following key points to mitigate risks during data migration:
Following and heeding the steps described here should ensure that your data migration effort is successful. TrainingMost projects that produce a completely new system also require training to be developed. Training development and delivery warrants its own book, so it isn't discussed here. You should refer to the many excellent books on this topic. However, you should consider some ideas specifically in the context of delivering a new software system:
Acceptance TestingMost outsourced projects have some kind of official event where a representative of the outsourcing organization's management reviews the new system's functionality and officially signs off, indicating that the contractor has fulfilled each of the new system's requirements. This is usually called acceptance testing. Like many joint events between customer and contractor, expectations need to be set carefully ahead of time. Several considerations exist, from both the contractor and the customer's perspectives. Contractor's Checklist for the Acceptance TestThe contractor should make the following preparations for the acceptance test:
Preparation is the key to a successful acceptance test. The end of the acceptance test should result in one of three situations: acceptance of the system, acceptance with conditions (usually conditional on any bugs discovered being corrected), or rejection of the system. Hopefully, your system will achieve one of the first two. Outsourcing Organization's Checklist for the Acceptance TestThe customer should make the following preparations for the acceptance test:
Most contractors are happy to work with their customers to achieve final system sign-off. Be prepared to sign off on items that have been demonstrated successfully so that the contractor can focus on correcting any final items. |
EAN: 2147483647
Pages: 166