Implementing a Message Hygiene System
|
|
An important component of your overall Exchange design is properly implementing a message hygiene system. Message hygiene is an all-encompassing term that covers antivirus and anti-spam technology. The anti-spam components of Exchange 2007 are discussed in Chapter 18, "Delivering E-mail"; in this chapter we want to cover some of the best practices associated with the anti-spam components.
Choosing an Antivirus System
There are at least 10 antivirus software packages available on the market that work with Exchange 2007 or that are in development to work with Exchange 2007:
-
Symantec Mail Security for Microsoft Exchange (www.symantec.com)
-
Trend ScanMail for Microsoft Exchange (www.trendmicro.com)
-
GFI Mail Security for Exchange (www.gfi.com)
-
eTrust InnoculateIT for Exchange (www.ca.com)
-
F-Secure Antivirus for Exchange (www.f-secure.com)
-
Proland Protector Plus Antivirus for Exchange (www.pspl.com)
-
Kaspersky Security for Exchange Server (www.kapersky.com)
-
McAfee GroupShield for Exchange (www.mcafee.com)
-
Sophos PureMessage for Exchange (www.sophos.com)
-
Microsoft Forefront Security for Exchange (www.microsoft.com)
If you have purchased Exchange Server Enterprise client access licenses and you have a Microsoft Software Assurance agreement, this includes licenses to use Microsoft Forefront Security for Exchange Server, so the decision as to which software package to use may have already been made for you. However, if you are in the process of evaluating Exchange-aware antivirus software, here are points to consider:
-
The software should use the Exchange antivirus API's (AVAPI) when scanning the information store as well as scanning the messages in the message transport system.
-
The software should use a different scanning engine technology and virus signature definitions than the client software on your perimeter network or client workstations uses.
-
Consider software that uses more than one scanning engine technology and signature database.
-
The software should be able to have updates scheduled at least once every hour. The updates should be applied automatically.
-
In organizations with more than one Exchange server, look for software that can be centrally configured and managed.
-
Consider software that can be configured with features such as file attachment blocking, customizable notification messages, and reporting features.
-
The software should offer automatic mail database scanning, scheduled scanning, and manual scanning, as well as the ability to turn off automatic scanning altogether.
Blocking File Attachments
If you talk to any administrator that has ever survived a serious virus outbreak, you will hear several common causes of the virus or worm outbreak:
-
E-mail was not being scanned for viruses.
-
Viruses were downloaded to a user's desktop via an external mail system such as Yahoo! or Hotmail.
-
Virus signatures were out-of-date or not yet available.
-
Virus payload came into the network via a file attachment type that was not being blocked.
Hopefully you are planning to remedy the first bullet point by ensuring that all e-mail content is scanned as it enters your organization. The second bullet point can best be remedied by ensuring that all clients on your network have adequate virus protection installed. Virus signatures being out-of-date or not yet available as well as viruses arriving via attachments that were allowed (when they should not have been) are something you can do something about on the e-mail server. In this section, we want to review some potentially dangerous attachment types that you should consider blocking.
Table 20.2 shows a list of commonly suspected attachment types that many administrators block using their antivirus software.
| Attachment Types | Attachment Description |
|---|---|
| BAT | DOS/Windows batch file |
| CMD | Windows command file |
| COM | DOS command file |
| EXE | Executable program |
| JS | JavaScript file |
| MSI | Windows installer file |
| PIF | Program information file for 16-bit application |
| SCR | Screensaver executable |
| SHS | Shell scrap objects |
| VB | VBScript file |
| VBS | VBScript file |
| WSC | Windows script component file |
Everyone knows about script files and executables, but there are a lot of other ways that hostile content can make its way onto your network. A long time ago, Microsoft published a list of attachments called Level-1 attachments that could conceivably transport a program or a script that could then be executed by a user or, even worse, executed automatically when a user opened a message. Outlook 2000 Service Pack 3 and later as well as Outlook Web Access won't even allow a user to open or save these file types, but remember that not all users use these applications. Many administrators still block Level-1 attachments so that they are stripped off of a message completely. The complete list of Microsoft Level-1 attachments is shown in Table 20.3.
| Attachment Types | Attachment Description |
|---|---|
| ADE | Microsoft Access project extension |
| ADP | Microsoft Access project |
| APP | Microsoft Visual FoxPro application |
| ASP | Active server page |
| ASX | Windows media audio or video shortcut |
| BAS | Visual Basic class module or a BASIC program |
| BAT | DOS/Windows batch file |
| CER | Security certificate |
| CHM | Compiled HTML help file |
| CMD | Windows command files |
| COM | DOS command file |
| CPL | Control Panel extension |
| CRT | Security certificate |
| CSH | KornShell script file |
| EXE | Executable programs |
| FXP | Microsoft Visual FoxPro compiled program |
| HLP | Windows help file |
| HTA | HTML program |
| INF | Windows setup information file |
| INS | Internet naming service |
| ISP | Internet communication settings |
| JS | JavaScript |
| JS | JScript script file |
| JSE | JScript encoded script file |
| KSH | KornShell script file |
| LNK | Link or shortcut file |
| MDA | Microsoft Access add-in program |
| MDB | Microsoft Access program |
| MDE | Microsoft Access MDE database |
| MDT | Microsoft Access workgroup |
| MDW | Microsoft Access workgroup |
| MDZ | Microsoft Access wizard program |
| MSC | Windows console definition |
| MSI | Windows installer files |
| MSI | Windows installer package |
| MSP | Windows installer patch |
| MST | Windows installer transform file |
| OPS | Office preferences file |
| PCD | Photo CD image |
| PIF | Program information file for 16-bit application |
| PIF | Shortcut to MS-DOS program |
| PRF | Microsoft Outlook profile setting |
| PRG | Microsoft Visual FoxPro program |
| PST | Microsoft Outlook Personal Folders file |
| REG | Registration entries |
| SCF | Windows Explorer command |
| SCR | Screensaver executables |
| SCT | Windows Script Component |
| SHB | Shell scrap object |
| SHS | Shell scrap object |
| TMP | Temporary file |
| URL | Internet shortcut |
| VB | VBScript file |
| VBE | VBScript encoded script file |
| VBS | VBScript file |
| VBS | Visual Basic Script file |
| VSMACROS | Visual Studio .NET macro project file |
| VSS | Visio shapes and Visio stencils file |
| VST | Visio template file |
| VSW | Visio workspace |
| WS | Windows script file |
| WSC | Windows script component |
| WSC | Windows script Component |
| WSF | Windows script file |
| WSH | Windows script host settings file |
Implementing Multiple Layers of Protection
A particular virus may sneak into your e-mail system because a signature has not yet been released for it. You can help mitigate this risk by checking for updates signatures hourly, but the time from which an antivirus software vendor learns about a new threat and when it actually releases signatures can be anywhere from a few hours to a few days.
The likelihood that you catch all viruses with a single scanning engine is pretty good, but additional scanning engines and additional layers of scanning can be even more effective. Multiple layers of protection are always a good precaution. Let's look at a couple of different approaches for doing this. In our definition of multiple layers of e-mail protection, there are certain things that should always be implemented:
-
E-mail should be scanned in at least two different places.
-
Multiple scanning engines, signature databases, or scanning technologies should be implemented. Don't be afraid to use more than one vendor.
-
Clients should always have antivirus software installed.
Figure 20.8 shows a network with three layers of protection. Inbound e-mail is directed to an SMTP-based antivirus system located in the organization's perimeter network. The organization's MX record directs inbound SMTP mail to the SMTP message hygiene system in the perimeter. The system in the perimeter network could be an Exchange 2007 Edge Transport server or it could be a third-party software package or mail security appliance. In the perimeter, the messages are inspected for viruses (and possibly also spam) and then directed to the Hub Transport server.
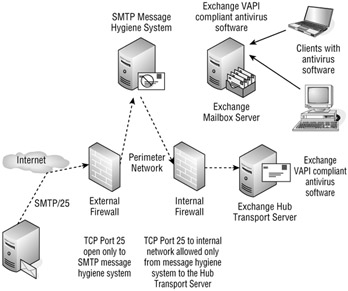
Figure 20.8: An example of a multilayer message hygiene system
The Hub Transport server inspects the message "in transit" and then passes it on to the Exchange 2007 Mailbox server. The Mailbox server may optionally also have antivirus software that inspects the message for viruses, though both store level and message transport level scanning is probably not necessary in the case of Exchange 2007. This is because all messages are sent through the Hub Transport server.
Clients can then download and view the message, where it may be inspected once again for a virus. In an ideal world, each step of the way a different scanning engine would be used. So the system in the perimeter network would use the vendor's scanning engine, the Hub Transport (and/or the Mailbox) server would use a different solution, and the clients would use a third vendor's solution. Some SMTP scanning systems and Exchange-aware solutions (such as Forefront Security for Exchange) already incorporate multiple scanning engines).
This approach may seem like overkill to some organizations, but it offers a few advantages:
-
Hostile content can be blocked in the perimeter.
-
There is an increased probability of detecting hostile content with multiple scanning engines.
-
Corporate or security policies can be enforced at the perimeter by blocking undesirable file types (including multimedia files and compressed files).
-
Internet IP addresses do not have direct access via SMTP to the Exchange Hub Transport system. The only SMTP system that can deliver e-mail to Exchange is the system in the perimeter network
Of course, you have to weigh these advantages with the added complexity and possibly managing more than one antivirus product. Another possible approach with many of the same advantages is to use a third-party managed provider to handle the initial message hygiene inspection.
Figure 20.9 shows how this might work. The organization's DNS MX records are configured to point to the managed provider's SMTP servers, not its own. The managed provider handles the initial message hygiene functions and then forwards the mail to the public IP address of the organization's Hub Transport servers. Then the internal virus scanning software can provide an additional layer of protection.
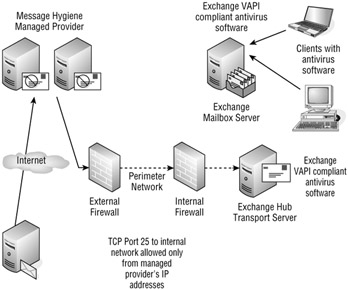
Figure 20.9: Using a third-party message hygiene solution
There are a few additional advantages to using a managed provider to provide this initial layer of protection besides just replacing software that you would have to manage:
-
Managed providers are usually staffed 24 by 7 by 365 and can react very quickly to emerging threats.
-
Managed providers usually use multiple scanning engines for both virus protection and spam detection.
-
Both malware and spam can be blocked before it ever even reaches your network connection, thus eliminating a burden on your own Internet links.
-
Your firewall can be configured to accept inbound SMTP only from the managed provider's IP addresses and thus provide better protection for your Hub Transport servers.
If you purchased Exchange 2007 Enterprise client access licenses and you have a Software Assurance agreement with Microsoft, this includes the ability to use Microsoft's Hosted Exchange Filtering service at no additional cost.
|
|
EAN: 2147483647
Pages: 198