Chapter 19: Additional Repurposing Attacks
In the ActiveX example in Chapter 18, ActiveX Repurposing Attacks, an attacker calls into the ActiveX control by coercing the target to load an HTML document that contains data specified by the attacker. The attacker uses the Active X control for a purpose other than the control s developer intended. This same concept applies to other technologies. The repurposing attacks apply to many technologies some are discussed in this chapter. In this chapter, we discuss how document formats and Web applications can be repurposed to perform malicious actions. You ll also learn the basic concept behind a related issue with the Microsoft Windows messaging system.
Understanding Document Formats That Request External Data
A useful feature in some document formats is the ability to request data from another source. You might recall that document formats accessing external data must be protected against Web beacons , as discussed in Chapter 7, Information Disclosure, but sometimes more dangerous bugs threaten when accessing external data.
Sometimes a data request can allow an elevation of privilege. Suppose an SQL statement, which an attacker might not have access to make, is the request for external data. If an attacker can find a document format that supports making SQL requests and can coerce a target (who has access to make SQL requests ) to open the document, the attacker s SQL statement will be successfully executed by the target, and the attacker s privileges would be elevated. The fact that any SQL query is run when the document is opened means an attacker can make any modifications to the database that the target can make.
Spreadsheets are a common example of a document format that often supports requesting external data. Spreadsheets are used to query the external data and create reports on that data. Not all spreadsheets request external data, however, and it is difficult to know when one is requesting such data. A user usually must open the spreadsheet to determine whether the spreadsheet requests external data, and sometimes even then it is difficult to tell. In some instances, simply requesting external data is dangerous. In addition to SQL statements, some other examples of dangerous external data requests include Lightweight Directory Access Protocol (LDAP), Simple Object Access Protocol (SOAP) requests (discussed later in this chapter), and Dynamic Data Exchange (DDE).
Sometimes file formats that request external data store this data at a location specified in the file. This enables additional attacks. Some external data requests might not seem harmful ”for example, a request to retrieve a URL or file. However, if the attacker has the ability to specify a location to store the response, danger is almost certainly ahead. For example, Microsoft Office Word and Excel contain features that allow users to insert the contents of one document into another file. This functionality can be specified by the document creator. The file containing the contents of the other file is updated with current contents of the containing file when the user opens the file. If an attacker is able to insert data into the file in this example, the data is stored in the original document and then must be sent back to the attacker. In other scenarios, an attacker might store the data in a location on the Internet from which it is easier to retrieve the data without coercing a victim into manually sending the document to the attacker. The problem in Word and Excel was mitigated in October 2002 when Microsoft released update MS02-059 ( http://www.microsoft.com/technet/security/bulletin/MS02-059.mspx ).
| Important | The repurposing attacks discussed in this chapter for document formats and Web pages that request external data leverage the target person as a human proxy who is unaware that the attacker s requests are being made under the target s account. |
Common Mitigation for Document Formats Requesting External Data
The ability to request external data is often very useful. Removing this functionality could hinder productivity, so this isn t always the best solution for customers. Many programs, such as the Office applications, mitigate the danger of requesting external data by requiring user interaction before making the request (no automatic external requests are allowed) and notifying the user before a request is made. For example, Excel displays the dialog box shown in Figure 19-1 when a refresh of the data requires requesting external data.
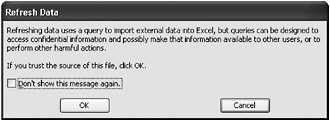
Figure 19-1: Microsoft Excel warns about requests for external data.
Testing Document Formats That Request External Data
The ability to request and/or store external data in ways that can be abused as described is usually documented as a feature. Remember that there are two issues when requesting external data ”requests that are harmful by themselves and the ability to store responses. As a tester, you need to look for bugs in both areas.
The ability to request external data is often a feature. Having knowledge of the security concerns along with a good understanding of the product s features can help you find these bugs. If possible, talk with a developer to gain a better understanding of the product and to determine whether a feature that requests external data exists. If the product has already been written and documentation is available, try looking for clues such as the use of external data, data links, SOAP, SQL, and LDAP. Verify that the user requesting the external data (the user opening the document) is aware of any potentially harmful external data requests and storage of the responses.
| Tip | Features that allow data to bind to a control or field in a document often allow accessing of external data. Be on the lookout for features like this so that you can verify whether they can be repurposed to request and/or store external data. |
Another effective way to find features that request external data is to exercise the application s functionality while using monitoring tools like FileMon (for local files) and Ethereal (for network traffic). More information about these tools is available in Chapters 3 and 4. The downside to this approach is that these tools will only help you determine if the application you are testing made an external request for the exact scenario you tested in the application. If the application was used differently to include additional features or if it used the previously tested functionality in a different manner, external requests might be made. For this reason, it is often useful to gather information about the product s functionality in combination with exercising its functionality while using monitoring tools like FileMon and Ethereal.
| Important | We talked with one product team about the threat of harmful requests for external data. They wanted to support automatic data updates through SQL statements and thought that they would examine the SQL statement to verify that it didn t modify data. If the statement only requested data, they thought, this would be a harmless action because their application would not allow the results of the request to be stored. After meeting with the SQL team, it became obvious that determining whether a SQL statement would modify data is not an easy task. Enter a bug if your application is attempting to filter the contents of requests that are known to be harmful. The approach to filter bad content as opposed to allowing only good content will almost always miss cases and result in security bugs. |
EAN: 2147483647
Pages: 156
- Article 225 Outside Branch Circuits and Feeders
- Article 332 Mineral-Insulated, Metal-Sheathed Cable Type MI
- Article 360 Flexible Metallic Tubing Type FMT
- Article 502 Class II Locations
- Example No. D2(a) Optional Calculation for One-Family Dwelling Heating Larger than Air Conditioning [See Section 220.82]