TACACS+ in Detail This section provides information about the architecture of TACACS+. TACACS+ performs reliable communication between the AAA server and AAA client. This communication, as well as the TACACS+ format, is reviewed in the following sections. In addition to this reliable format, TACACS+ performs encryption and authentication of the entire message between the AAA server and AAA client. Finally, we wrap up with the actual operation of the protocol. TACACS+ Communication TACACS+ communication between the network access server (NAS) and AAA client is based on the TCP protocol and provides a reliable delivery mechanism to the AAA messaging. TACACS+ uses TCP port 49 and creates a session to facilitate the messaging in an AAA exchange. Many benefits in using TCP for session control in TACACS+ exist. Among these benefits is the fact that TACACS+ uses TCP to provide an acknowledgment of requests that are made by a NAS or an AAA client. In addition to the acknowledgments provided within TCP, TACACS+ also has the ability, through inherent functionality of the TCP protocol, to adapt to congestion and bandwidth. An example of this functionality is the utilization of TCP windowing. TACACS+ also has the ability to immediately determine when an AAA server is not available by using TCP resets to alert the AAA client of server communication issues. This functionality cannot be provided with the RADIUS protocol because the RADIUS protocol uses UDP for segment delivery. TACACS+ Format and Header Values The TACACS+ ID defines a 12-byte header that appears in all TACACS+ packets. This header is always sent in clear text format. The following defines the TACACS+ ID fields, which are also shown in Figure 2-1: Major_version This is the major version number of TACACS+. The value appears in the header as TAC_PLUS_MAJOR_VER=0xc. Minor_version This field provides revision number for the TACACS+ protocol. It also provides for backward compatibility of the protocol. A default value, as well as a version one, is defined for some commands. These values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. Should an AAA server running the TACACS+ daemon receive a TACACS+ packet defining a minor version other than one of the ones just listed, it sends an error status back and sets the minor_version to the closest version that is supported. Type This distinguishes the packet type. Only certain types are legal. The legal packet types are as follows: - TAC_PLUS_AUTHEN=0x01This is the packet type that signifies authentication. - TAC_PLUS_AUTHOR-0x02This is the packet type that signifies authorization. - TAC_PLUS_ACCT=0x03This is the packet type that signifies accounting.
NOTE The significance of these possible message types is that TACACS+ has the ability to perform authentication, authorization, and accounting as separate functions. RADIUS does not have this capability.
Seq_no This determines the sequence number for the current session. TACACS+ has the ability to perform multiple TACACS+ sessions or to use one TACACS+ session per AAA client. The beginning packet of a session is identified by the sequence number 1. All subsequent packets are an increment from that initial number. Because the AAA client sends the first packet to the AAA server running the TACACS+ daemon, it is always the number 1, and all subsequent packets from the AAA client are identified with odd sequence numbers. In addition to this sequencing scheme, the highest sequence number that can be reached is 28-1. After this value is reached, the session that is established between the AAA client and the AAA server is reset, and a new session is started. When the session restarts, it begins, once again, with a sequence number of 1. Flags In this section, the field can contain various flags. These flags can be TAC_PLUS_UNENCRYPTED_FLAG and TAC_PLUS_SINGLE_CONNECT_FLAG. The TAC_PLUS_UNENCRYPTED_FLAG flag specifies if encryption is being performed on the body of the TACACS+ packet. If this flag is set, meaning that the value is set to 1, encryption is not being performed and likewise, if the value of this flag is set to 0, the packet is, in fact, being encrypted. The ability to disable TACACS+ encryption should be used primarily for debugging purposes. This functionality is nice when you need to see all the information in the body of the packet. Keep in mind that the header is always sent clear text. The TAC_PLUS_SINGLE_CONNECT_FLAG determines whether or not multiplexing multiple TACACS+ sessions over one TCP session is supported. This is determined in the first two TACACS+ messages of a session. When determined, this does not change. Session_id This is a random value that designates the current session between the AAA client and the AAA server running the TACACS+ daemon. This value remains the same for the duration of a session. Length This field states the total length of the TACACS+ packet, not to include the 12-byte header.
Figure 2-1. TACACS+ Header Format 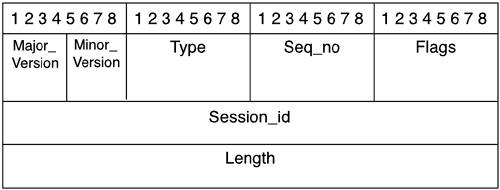
Encrypting TACACS+ One feature that provides more security under TACACS+, as opposed to its alternative RADIUS, is the encryption of the entire packet. This encryption is sent between the AAA client and the AAA server running the TACACS+ daemon. This is not to be confused with encryption of user data. This is not an encryption such as 3DES-IPSec or RSA encryption, but is rather a combination of a hashing algorithm and an XOR function. TACACS+ uses MD5 to hash using a secret key provided on both ends. The process of TACACS+ encryption is as follows: Step 1. | Information is taken from the packet header, and the preshared key calculates a series of hashes. The first is a hash that is calculated on a concatenation of the session_id, the version, the seq_no, and the pre-shared key value. Each hash that is created has the previous hash in it as well. This is done a number of times that is dependent on the particular implementation of TACACS+.
| Step 2. | The calculated hash is concatenated and then truncated to the length of the data that is being encrypted. Each hash has the previous hash concatenated to its input values. The result is called the pseudo_pad.
| Step 3. | The cipher text is produced by doing a bytewise XOR on the pseudo_pad with the data that is being encrypted.
| Step 4. | The receiving device uses its pre-shared key to calculate the pseudo_pad, and then an XOR of the newly created pseudo_pad results in the original data in clear text.
|
TACACS+ Operation Three possible activities can be performed during TACACS+ operation. The first operation performed is authentication. This is done to clearly identify the user. The second operation is authorization and is possible only once a user has been identified. Therefore, you must authenticate prior to authorizing. The third operation is accounting. The accounting process keeps track of actions performed. The three processes are each independent of the other. TACACS+ and Authentication When authentication is performed in TACACS+, three distinct packet exchanges take place. The three types of packets are START This packet is used initially when the user attempts to connect. REPLY Sent by the AAA server during the authentication process. CONTINUE Used by the AAA client to return username and password to the AAA server.
In Figure 2-2, a user initiates a connection to an AAA client. The following is the process that occurs during this time: Step 1. | The AAA client receives the connection request from the user.
| Step 2. | The first packet type, START, is sent to the AAA server that is running the TACACS+ daemon.
This START message contains information about the type of authentication.
| Step 3. | The TACACS+ server then sends the REPLY packet back to the AAA client. At this point, the server requests the username.
| Step 4. | The AAA client sends a CONTINUE packet to the TACACS+ server with the username provided by the user.
| Step 5. | The TACACS+ server then sends the REPLY packet back to the AAA client to ask the client to get the password.
| Step 6. | The AAA client sends a CONTINUE packet to the TACACS+ server with the password provided by the user.
| Step 7. | The TACACS+ server then sends the REPLY packet back to the AAA client to indicate a pass/fail of authentication. The possible returned values can be
- - ACCEPT The user is authenticated and service can begin. If the NAS is configured to require authorization, authorization begins at this time.
- - REJECT The user has failed to authenticate. The user can be denied further access or is prompted to retry the login sequence depending on the TACACS+ daemon.
- - ERROR An error occurred at some time during authentication. This can be either at the daemon or in the network connection between the daemon and the NAS. If an ERROR response is received, the NAS typically tries to use an alternative method for authenticating the user.
- - CONTINUE The user is prompted for additional authentication information.
|
Figure 2-2. TACACS+ Messaging 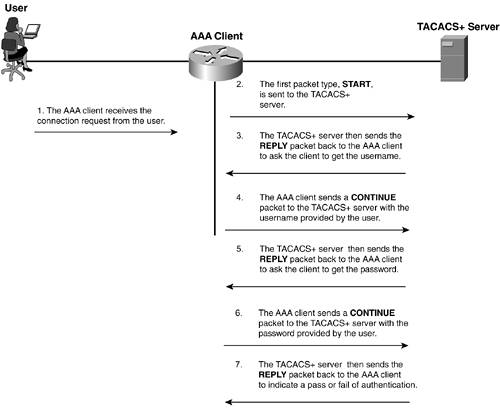
NOTE START and CONTINUE packets are always sent by the AAA client, and REPLY packets are always sent by the TACACS+ server.
TACACS+ and Authorization In the previous section, you saw the authentication process in TACACS+. This section discusses the authorization process. To facilitate authorization in TACACS+, two message types are used. The first message is an authorization REQUEST, and the second is the authorization RESPONSE. The REQUEST sources from the AAA client, and the RESPONSE sources from the AAA server. Figure 2-3 shows a basic authorization attempt. Figure 2-3. Simple TACACS+ Authorization 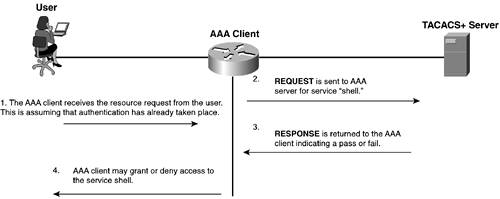
The RESPONSE message (in Step 3 in Figure 2-3) contains one of the following replies: A FAIL response from the server indicates that the services requested for authorization are not granted. If the server responds with a PASS_ADD, the request is authorized, and the information returned in the RESPONSE is used in addition to the requested information. If no additional arguments are returned by the AAA server in the RESPONSE, the request is authorized. In some cases, a PASS_REPL might be returned to the AAA client. In this case, the server is choosing to ignore the REQUEST and is replacing it with the information returned in the RESPONSE. If the status is set to FOLLOW, this indicates that the AAA server that is sending the RESPONSE wants to have the authorization take place on another server, and this server information is listed in the RESPONSE packet. The AAA client has the option of using this server or simply can treat it as a FAIL. If the status returned is ERROR, this indicates an error on the AAA server. This is commonly a preshared key mismatch; however, it can be a number of issues and further troubleshooting needs to take place.
In authorization, Attribute-Value (AV) determine authorized services. Table 2-1 provides the AV pairs that are currently supported on Cisco IOS up to version 12.2 for authentication and authorization. Table 2-1. Cisco IOS Supported AV Pairs for Accounting and Authorization[1]Attribute | Description | 11.0 | 11.1 | 11.2 | 11.3 | 12.0 | 12.1 | 12.2 |
|---|
acl=x | ASCII number representing a connection access list. Used only when service=shell. | yes | yes | yes | yes | yes | yes | yes | addr=x | A network address. Used with service=slip, service=ppp, and protocol=ip. Contains the IP address that the remote host should use when connecting via Serial Line Internet Protocol (SLIP) or PPP/IP. For example, addr=10.2.3.4. | yes | yes | yes | yes | yes | yes | yes | addr-pool=x | Specifies the name of a local pool from which to get the address of the remote host. Used with service=ppp and protocol=ip. Note that addr-pool works in conjunction with local pooling. It specifies the name of a local pool (which must be preconfigured on the network access server). Use the ip-local pool command to declare local pools. For example: ip address-pool local ip local pool boo 10.0.0.1 10.0.0.10 ip local pool moo 10.0.0.1 10.0.0.20 You can then use TACACS+ to return addr-pool=boo or addr-pool=moo to indicate the address pool from which you want to get this remote node's address. | yes | yes | yes | yes | yes | yes | yes | autocmd=x | Specifies an autocommand to be executed at EXEC startup (for example, autocmd=telnet example.com). Used only with service=shell. | yes | yes | yes | yes | yes | yes | yes | callback-dialstring | Sets the telephone number for a callback (for example, callback-dialstring=408-555-1212). Value is NULL or a dial-string. A NULL value indicates that the service might choose to get the dial string through other means. Used with service=arap, service=slip, service=ppp, service=shell. Not valid for ISDN. | no | yes | yes | yes | yes | yes | yes | callback-line | The number of a TTY line to use for callback (for example, callback-line=4). Used with service=arap, service=slip, service=ppp, service=shell. Not valid for ISDN. | no | yes | yes | yes | yes | yes | yes | callback-rotary | The number of a rotary group (between 0 and 100 inclusive) to use for callback (for example, callback-rotary=34). Used with service=arap, service=slip, service=ppp, service=shell. Not valid for ISDN. | no | yes | yes | yes | yes | yes | yes | cmd-arg=x | An argument to a shell (EXEC) command. This indicates an argument for the shell command that is to be run. Multiple cmd-arg attributes can be specified, and they are order dependent. Note: This TACACS+ AV pair cannot be used with RADIUS attribute 26. | yes | yes | yes | yes | yes | yes | yes | cmd=x | A shell (EXEC) command. This indicates the command name for a shell command that is to be run. This attribute must be specified if service equals "shell." A NULL value indicates that the shell itself is being referred to. Note: This TACACS+ AV pair cannot be used with RADIUS attribute 26. | yes | yes | yes | yes | yes | yes | yes | data-service | Used with the service=outbound and protocol=ip. | no | no | no | no | no | yes | yes | dial-number | Defines the number to dial. Used with the service=outbound and protocol=ip. | no | no | no | no | no | yes | yes | dns-servers= | Identifies a DNS server (primary or secondary) that can be requested by Microsoft Point-to-Point Protocol (PPP) clients from the network access server during IP Control Protocol (IPCP) negotiation. To be used with service=ppp and protocol=ip. The IP address identifying each DNS server is entered in dotted decimal format. | no | no | no | yes | yes | yes | yes | force-56 | Determines whether the network access server uses only the 56 K portion of a channel, even when all 64 K appears to be available. To turn on this attribute, use the "true" value (force-56=true). Any other value is treated as false. Used with the service=outbound and protocol=ip. | no | no | no | no | no | yes | yes | gw-password | Specifies the password for the home gateway during the Layer 2 Forwarding (L2F) tunnel authentication. Used with service=ppp and protocol=vpdn. | no | no | yes | yes | yes | yes | yes | idletime=x | Sets a value, in minutes, after which an idle session is terminated. A value of zero indicates no timeout. | no | yes | yes | yes | yes | yes | yes | inacl#<n> | ASCII access list identifier for an input access list to be installed and applied to an interface for the duration of the current connection. Used with service=ppp and protocol=ip, and service=ppp and protocol =ipx. Per-user access lists do not currently work with ISDN interfaces. | no | no | no | yes | yes | yes | yes | inacl=x | ASCII identifier for an interface input access list. Used with service=ppp and protocol=ip. Per-user access lists do not currently work with ISDN interfaces. | yes | yes | yes | yes | yes | yes | yes | interface-config#<n> | Specifies user-specific AAA interface configuration information with Virtual Profiles. The information that follows the equal sign (=) can be any Cisco IOS interface configuration command. Multiple instances of the attributes are allowed, but each instance must have a unique number. Used with service=ppp and protocol=lcp. Note: This attribute replaces the "interface-config=" attribute. | no | no | no | yes | yes | yes | yes | ip-addresses | Space-separated list of possible IP addresses that can be used for the endpoint of a tunnel. Used with service=ppp and protocol=vpdn. | no | no | yes | yes | yes | yes | yes | l2tp-busy-disconnect | If a vpdn-group on an L2TP network server (LNS) uses a virtual template that is configured to be precloned, this attribute controls the disposition of a new L2TP session that finds no pre-cloned interface to which to connect. If the attribute is true (the default), the session is disconnected by the LNS. Otherwise, a new interface is cloned from the virtual template. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-cm-local-window-size | Specifies the maximum receive window size for L2TP control messages. This value is advertised to the peer during tunnel establishment. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-drop-out-of-order | Respects sequence numbers on data packets by dropping those that are received out of order. This does not ensure that sequence numbers are sent on data packets, just how to handle them if they are received. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-hello-interval | Specifies the number of seconds for the hello keepalive interval. Hello packets are sent when no data has been sent on a tunnel for the number of seconds configured here. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-hidden-avp | When enabled, sensitive Attribute Value Pairs (AVPs) in L2TP control messages are scrambled or hidden. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-nosession-timeout | Specifies the number of seconds that a tunnel stays active with no sessions before timing out and shutting down. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-tos-reflect | Copies the IP type of service (ToS) field from the IP header of each payload packet to the IP header of the tunnel packet for packets entering the tunnel at the LNS. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-tunnel-authen | If this attribute is set, it performs L2TP tunnel authentication. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-tunnel-password | Shared secret used for L2TP tunnel authentication and AVP hiding. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | l2tp-udp-checksum | This is an authorization attribute and defines whether L2TP should perform UDP checksums for data packets. Valid values are "yes" and "no." The default is no. Used with service=ppp and protocol=vpdn. | no | no | no | no | no | yes | yes | link-compression= | Defines whether to turn on or turn off "stac" compression over a PPP link. Used with service=ppp. Link compression is defined as a numeric value as follows: 0: None 1: Stac 2: Stac-Draft-9 3: MS-Stac | no | no | no | yes | yes | yes | yes | load-threshold=<n> | Sets the load threshold for the caller at which additional links are either added to or deleted from the multilink bundle. If the load goes above the specified value, additional links are added. If the load goes below the specified value, links are deleted. Used with service=ppp and protocol=multilink. The range for <n> is from 1 to 255. | no | no | no | yes | yes | yes | yes | map-class | Allows the user profile to reference information configured in a map class of the same name on the network access server that dials out. Used with the service=outbound and protocol=ip. | no | no | no | no | no | yes | yes | max-links=<n> | Restricts the number of links that a user can have in a multilink bundle. Used with service=ppp and protocol=multilink. The range for <n> is from 1 to 255. | no | no | no | yes | yes | yes | yes | min-links | Sets the minimum number of links for Multilink PPP (MLP). Used with service=ppp, protocol=multilink, and protocol=vpdn. | no | no | no | no | no | yes | yes | nas-password | Specifies the password for the NAS during the L2F tunnel authentication. Used with service=ppp and protocol=vpdn. | no | no | yes | yes | yes | yes | yes | nocallback-verify | Indicates that no callback verification is required. The only valid value for this parameter is 1 (for example, nocallback-verify=1). Used with service=arap, service=slip, service=ppp, service=shell. There is no authentication on callback. Not valid for ISDN. | no | yes | yes | yes | yes | yes | yes | noescape=x | Prevents user from using an escape character. Used with service=shell. Can be either true or false (for example, noescape=true). | yes | yes | yes | yes | yes | yes | yes | nohangup=x | Used with service=shell. Specifies the nohangup option, which means that after an EXEC shell is terminated, the user is presented with another login (username) prompt. Can be either true or false (for example, nohangup=false). | yes | yes | yes | yes | yes | yes | yes | old-prompts | Allows providers to make the prompts in TACACS+ appear identical to those of earlier systems (TACACS and extended TACACS). This allows administrators to upgrade from TACACS or XTACACS to TACACS+ transparently to users. | yes | yes | yes | yes | yes | yes | yes | outacl#<n> | ASCII access list identifier for an interface output access list to be installed and applied to an interface for the duration of the current condition. Used with service=ppp, protocol=ip, service service=ppp, and protocol=ipx. Per-user access lists do not currently work with ISDN interfaces. | no | no | no | yes | yes | yes | yes | outacl=x | ASCII identifier for an interface output access list. Used with service=ppp, protocol=ip, service service=ppp, and protocol=ipx. Contains an IP output access list for SLIP or PPP/IP (for example, outacl=4). The access list itself must be preconfigured on the router. Per-user access lists do not currently work with ISDN interfaces. | yes (PPP/IP only) | yes | yes | yes | yes | yes | yes | pool-def#<n> | Defines IP address pools on the NAS. Used with service=ppp and protocol=ip. | no | no | no | yes | yes | yes | yes | pool-timeout= | Defines (in conjunction with pool-def) IP address pools on the NAS. During IPCP address negotiation, if an IP pool name is specified for a user (see the addr-pool attribute), a check is made to see if the named pool is defined on the NAS. If it is, the pool is consulted for an IP address. Used with service=ppp and protocol=ip. | no | no | yes | yes | yes | yes | yes | port-type | Indicates the type of physical port the NAS is using to authenticate the user. Physical ports are indicated by a numeric value as follows: 0: Asynchronous 1: Synchronous 2: ISDN-Synchronous 3: ISDN-Asynchronous (V.120) 4: ISDN-Asynchronous (V.110) 5: Virtual Used with service=any and protocol=aaa. | no | no | no | no | no | yes | yes | ppp-vj-slot-compression | Instructs the Cisco router not to use slot compression when sending VJ-compressed packets over a PPP link. | no | no | no | yes | yes | yes | yes | priv-lvl=x | Privilege level to be assigned for the EXEC. Used with service=shell. Privilege levels range from 0 to 15, with 15 being the highest. | yes | yes | yes | yes | yes | yes | yes | protocol=x | A protocol that is a subset of a service. An example would be any PPP Network Control Protocol (NCP.) Currently known values are lcp, ip, ipx, atalk, vines, lat, xremote, tn3270, telnet, rlogin, pad, vpdn, osicp, deccp, ccp, cdp, bridging, xns, nbf, bap, multilink, and unknown. | yes | yes | yes | yes | yes | yes | yes | proxyacl#<n> | Allows users to configure the downloadable user profiles (dynamic access control lists [ACLs]) by using the authentication proxy feature so that users can have the configured authorization to permit traffic going through the configured interfaces. Used with service=shell and protocol=exec. | no | no | no | no | no | yes | yes | route | Specifies a route to be applied to an interface. Used with service=slip, service=ppp, and protocol=ip. During network authorization, the route attribute can be used to specify a per-user static route, to be installed by TACACS+ as follows: route="dst_address mask [gateway]" This indicates a temporary static route that is to be applied. The dst_address, mask, and gateway are expected to be in the usual dotted decimal notation, with the same meanings as in the familiar ip route configuration command on a NAS. If gateway is omitted, the peer's address is the gateway. The route is expunged when the connection terminates. | no | yes | yes | yes | yes | yes | yes | route#<n> | Like the route AV pair, this specifies a route to be applied to an interface, but these routes are numbered, allowing multiple routes to be applied. Used with service=ppp, protocol=ip, service=ppp, and protocol=ipx. | no | no | no | yes | yes | yes | yes | routing=x | Specifies whether routing information is to be propagated to and accepted from this interface. Used with service=slip, service=ppp, and protocol=ip. Equivalent in function to the /routing flag in SLIP and PPP commands. Can either be true or false (for example, routing=true). | yes | yes | yes | yes | yes | yes | yes | rte-fltr-in#<n> | Specifies an input access list definition to be installed and applied to routing updates on the current interface for the duration of the current connection. Used with service=ppp, protocol=ip, service=ppp, and protocol=ipx. | no | no | no | yes | yes | yes | yes | rte-fltr-out#<n> | Specifies an output access list definition to be installed and applied to routing updates on the current interface for the duration of the current connection. Used with service=ppp, protocol=ip, service=ppp, and protocol=ipx. | no | no | no | yes | yes | yes | yes | sap#<n> | Specifies static Service Advertising Protocol (SAP) entries to be installed for the duration of a connection. Used with service=ppp and protocol=ipx. | no | no | no | yes | yes | yes | yes | sap-fltr-in#<n> | Specifies an input SAP filter access list definition to be installed and applied on the current interface for the duration of the current connection. Used with service=ppp and protocol=ipx. | no | no | no | yes | yes | yes | yes | sap-fltr-out#<n> | Specifies an output SAP filter access list definition to be installed and applied on the current interface for the duration of the current connection. Used with service=ppp and protocol=ipx. | no | no | no | yes | yes | yes | yes | send-auth | Defines the protocol to use (Password Authentication Protocol [PAP] or Challenge Handshake Authentication Protocol [CHAP]) for username-password authentication following Caller Line Identification (CLID) authentication. Used with service=any and protocol=aaa. | no | no | no | no | no | yes | yes | send-secret | Specifies the password that the NAS needs to respond to a CHAP/PAP request from the remote end of a connection on an outgoing call. Used with service=ppp and protocol=ip. | no | no | no | no | no | yes | yes | service=x | The primary service. Specifying a service attribute indicates that this is a request for authorization or accounting of that service. Current values are slip, ppp, arap, shell, tty-daemon, connection, and system. This attribute must always be included. | yes | yes | yes | yes | yes | yes | yes | source-ip=x | Used as the source IP address of all Virtual Private Dial-Up Networking (VPDN) packets generated as part of a VPDN tunnel. This is equivalent to the Cisco vpdn outgoing global configuration command. | no | no | yes | yes | yes | yes | yes | spi | Carries the authentication information needed by the home agent to authenticate a mobile node during registration. The information is in the same syntax as the ip mobile secure host <addr> configuration command. Basically, it contains the rest of the configuration command that follows that string, verbatim. It provides the security parameter index (SPI), key, authentication algorithm, authentication mode, and replay protection timestamp range. Used with service=mobileip and protocol=ip. | no | no | no | no | no | yes | yes | timeout=x | The number of minutes before an EXEC or AppleTalk Remote Access (ARA) session disconnects (for example, timeout=60). A value of zero indicates no timeout. Used with service=arap. | yes | yes | yes | yes | yes | yes | yes | tunnel-id | Specifies the username that authenticates the tunnel over which the individual user message identifier (MID) is projected. This is analogous to the remote name in the vpdn outgoing command. Used with service=ppp and protocol=vpdn. | no | no | yes | yes | yes | yes | yes | wins-servers= | Identifies a Windows NT server that can be requested by Microsoft PPP clients from the network access server during IP Control Protocol (IPCP) negotiation. To be used with service=ppp and protocol=ip. The IP address identifying each Windows NT server is entered in dotted decimal format. | no | no | no | yes | yes | yes | yes | zonelist=x | A numeric zonelist value. Used with service=arap. Specifies an AppleTalk zonelist for ARA (for example, zonelist=5). | yes | yes | yes | yes | yes | yes | yes |
TACACS+ Accounting The functionality of accounting in TACACS+ is similar to that of authorization. Accounting takes place by sending a record to the AAA server. Each of these records includes an AV pair for accounting. Three types of records can be sent to the AAA server. They are as follows: The Start record indicates when a service begins and contains the information that was included in the authorization process, as well as specific information to the account. A Stop record indicates when a service is about to stop or is terminated and also includes information that was included in the authorization process, as well as specific information to the account. A Continue record is also called a Watchdog. This is sent when a service is still in progress and allows the AAA client to provide updated information to the AAA server. As seen in the previous records, this also includes information that was included in the authorization process, as well as specific information to the account.
NOTE A record can be sent as both a Start record and a Continue record. This indicates that the Continue record is a duplicate of the Start record.
Accounting also uses the two message types that authorization uses, a REQUEST and a RESPONSE. The AAA server has the capability to send the following in a RESPONSE: SUCCESS indicates that the server received the record that was sent by the AAA client. An ERROR indicates that the server failed to commit the record to its database. A FOLLOW is similar to that of a FOLLOW in authorization. This indicates that the server wishes the AAA client to send the record to another AAA server, and the AAA server information is included in the RESPONSE.
Figure 2-4 shows a basic example of the accounting process between the AAA client and the AAA server. Figure 2-4. Basic Accounting 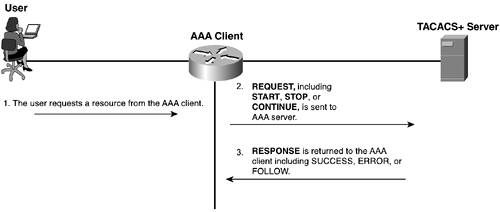
In Table 2-2, the TACAS+ accounting AV pairs that are supported in IOS versions up to 12.2 are shown. Table 2-2. TACACS+ Accounting AV Pairs[2]Attribute | Description | 11.0 | 11.1 | 11.2 | 11.3 | 12.0 | 12.1 | 12.2 |
|---|
Abort-Cause | If the fax session aborts, it indicates the system component that signaled the abort. Examples of system components that could trigger an abort are Fax Application Process (FAP), TIFF (the TIFF reader or the TIFF writer), fax-mail client, fax-mail server, Enhanced Simple Mail Transport (ESMTP) client, or ESMTP server. | no | no | no | no | no | yes | yes | bytes_in | The number of input bytes transferred during this connection. | yes | yes | yes | yes | yes | yes | yes | bytes_out | The number of output bytes transferred during this connection. | yes | yes | yes | yes | yes | yes | yes | Call-Type | Describes the type of fax activity: fax receive or fax send. | no | no | no | no | no | yes | yes | cmd | The command the user executed. | yes | yes | yes | yes | yes | yes | yes | data-rate | This AV pair has been renamed. See nas-rx-speed. | | | | | | | | disc-cause | Specifies the reason a connection was taken off line. The disc-cause attribute is sent in accounting-stop records. This attribute also causes Stop records to be generated without first generating Start records if disconnection occurs before authentication is performed for a list of disc-cause values and their meanings. | no | no | no | yes | yes | yes | yes | disc-cause-ext | Extends the disc-cause attribute to support vendor-specific reasons why a connection was taken off line. | no | no | no | yes | yes | yes | yes | elapsed_time | The elapsed time in seconds for the action. Useful when the device does not keep real time. | yes | yes | yes | yes | yes | yes | yes | Email-Server-Address | Indicates the IP address of the e-mail server handling the on-ramp fax-mail message. | no | no | no | no | no | yes | yes | Email-Server-Ack-Flag | Indicates that the on-ramp gateway has received a positive acknowledgment from the e-mail server accepting the fax-mail message. | no | no | no | no | no | yes | yes | event | Information included in the accounting packet that describes a state change in the router. Events described are accounting starting and accounting stopping. | yes | yes | yes | yes | yes | yes | yes | Fax-Account-Id-Origin | Indicates the account ID origin as defined by the system administrator for the mmoip aaa receive-id or the mmoip aaa send-id command. | no | no | no | no | no | yes | yes | Fax-Auth-Status | Indicates whether or not authentication for this fax session was successful. Possible values for this field are success, failed, bypassed, or unknown. | no | no | no | no | no | yes | yes | Fax-Connect-Speed | Indicates the modem speed at which this fax-mail was initially transmitted or received. Possible values are 1200, 4800, 9600, and 14,400. | no | no | no | no | no | yes | yes | Fax-Coverpage-Flag | Indicates whether or not a cover page was generated by the off-ramp gateway for this fax session. True indicates that a cover page was generated; false means that a cover page was not generated. | no | no | no | no | no | yes | yes | Fax-Dsn-Address | Indicates the address to which delivery status notifications (DSNs) are to be sent. | no | no | no | no | no | yes | yes | Fax-Dsn-Flag | Indicates whether or not DSN has been enabled. True indicates that DSN has been enabled; false means that DSN has not been enabled. | no | no | no | no | no | yes | yes | Fax-Mdn-Address | Indicates the address to which MDNs are to be sent. | no | no | no | no | no | yes | yes | Fax-Mdn-Flag | Indicates whether or not message delivery notification (MDN) has been enabled. True indicates that MDN has been enabled; false means that MDN has not been enabled. | no | no | no | no | no | yes | yes | Fax-Modem-Time | Indicates the amount of time in seconds the modem sent fax data (x) and the amount of time in seconds of the total fax session (y), which includes both fax-mail and Public Switched Telephone Network (PSTN) time, in the form x/y. For example, 10/15 means that the transfer time took 10 seconds, and the total fax session took 15 seconds. | no | no | no | no | no | yes | yes | Fax-Msg-Id= | Indicates a unique fax message identification number assigned by store and forward fax. | no | no | no | no | no | yes | yes | Fax-Pages | Indicates the number of pages transmitted or received during this fax session. This page count includes cover pages. | no | no | no | no | no | yes | yes | Fax-Process-Abort-Flag | Indicates that the fax session was aborted or successful. True means that the session was aborted; false means that the session was successful. | no | no | no | no | no | yes | yes | Fax-Recipient-Count | Indicates the number of recipients for this fax transmission. Until e-mail servers support Session mode, the number should be 1. | no | no | no | no | no | yes | yes | Gateway-Id | Indicates the name of the gateway that processed the fax session. The name appears in the following format: hostname.domain-name. | no | no | no | no | no | yes | yes | mlp-links-max | Gives the count of links that are known to have been in a given multilink session at the time the accounting record is generated. | no | no | no | yes | yes | yes | yes | mlp-sess-id | Reports the identification number of the multilink bundle when the session closes. This attribute applies to sessions that are part of a multilink bundle. This attribute is sent in authentication-response packets. | no | no | no | yes | yes | yes | yes | nas-rx-speed | Specifies the average number of bits per second over the course of the connection's lifetime. This attribute is sent in accounting-stop records. | no | no | no | yes | yes | yes | yes | nas-tx-speed | Reports the transmit speed negotiated by the two modems. | no | no | no | yes | yes | yes | yes | paks_in | The number of input packets transferred during this connection. | yes | yes | yes | yes | yes | yes | yes | paks_out | The number of output packets transferred during this connection. | yes | yes | yes | yes | yes | yes | yes | port | The port the user was logged in to. | yes | yes | yes | yes | yes | yes | yes | Port-Used | Indicates the slot/port number of the Cisco AS5300 used to either transmit or receive this fax-mail. | no | no | no | no | no | yes | yes | pre-bytes-in | Records the number of input bytes before authentication. This attribute is sent in accounting-stop records. | no | no | no | yes | yes | yes | yes | pre-bytes-out | Records the number of output bytes before authentication. This attribute is sent in accounting-stop records. | no | no | no | yes | yes | yes | yes | pre-paks-in | Records the number of input packets before authentication. This attribute is sent in accounting-stop records. | no | no | no | yes | yes | yes | yes | pre-paks-out | Records the number of output packets before authentication. The pre-paks-out attribute is sent in accounting-stop records. | no | no | no | yes | yes | yes | yes | pre-session-time | Specifies the length of time, in seconds, from when a call first connects to when it completes authentication. | no | no | no | yes | yes | yes | yes | priv_level | The privilege level associated with the action. | yes | yes | yes | yes | yes | yes | yes | protocol | The protocol associated with the action. | yes | yes | yes | yes | yes | yes | yes | reason | Information included in the accounting packet that describes the event that caused a system change. Events described are system reload, system shutdown, or accounting reconfiguration (being turned on or off). | yes | yes | yes | yes | yes | yes | yes | service | The service the user used. | yes | yes | yes | yes | yes | yes | yes | start_time | The time the action started (in seconds since the epoch, 12:00 a.m. January 1, 1970). The clock must be configured to receive this information. | yes | yes | yes | yes | yes | yes | yes | stop_time | The time the action stopped (in seconds since the epoch). The clock must be configured to receive this information. | yes | yes | yes | yes | yes | yes | yes | task_id | Start and Stop records for the same event must have matching (unique) task_id numbers. | yes | yes | yes | yes | yes | yes | Yes | timezone | The time zone abbreviation for all timestamps included in this packet. | yes | yes | yes | yes | yes | yes | Yes | xmit-rate | This AV pair has been renamed. See nas-tx-speed. | | | | | | | |
|



