Recipe 9.11. Monitoring Registry Activity
ProblemYou want to monitor Registry accesses. This could involve anything from watching what processes are using the Registry to monitoring what a specific user is doing with the Registry. SolutionThere are two ways to monitor Registry activity. You can view real-time access to the Registry with the Sysinternals Registry Monitor (regmon.exe) tool. With it you can view the process name, the PID, and the operation performed (e.g., QueryKey, EnumerateValue, SetValue, etc.) for all the processes that have a key or value open. Figure 9-1 shows this tool. Figure 9-1. Sysinternals Registry Monitor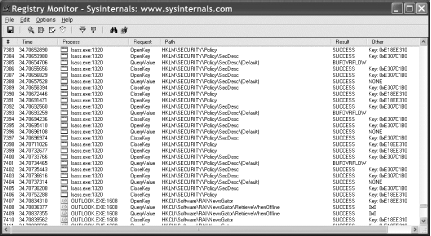 If you want to monitor Registry activity over a long period of time or cannot keep a copy of Registry Monitor open at all times, another option is to enable Registry auditing. With Registry auditing enabled, you can get detailed information in the Security event log about the successful or failed attempts a particular user or group of users make to the Registry. Here is how you set that up:
DiscussionTo enable auditing in the Registry, you have to complete two steps. The first consists of configuring what you want to audit in the Registry, which you can do with the Registry Editor. See Table 9-4 for the complete list of audit options. After you've completed this, auditing isn't turned on yet. To do that, you have to go to the Local Policies snap-in (or Group Policy Object Editor in a domain environment) and enable auditing as described above. At this point, any Registry access to the keys you configured should be logged to the Security event log.
See AlsoMS KB 315416, "HOW TO: Use Group Policy to Audit Registry Keys in Windows 2000" |
EAN: 2147483647
Pages: 408