2. What is Digital Watermarking?
2. What is Digital Watermarking?
The end of the previous millennium has seen the transition from the analog to the digital world. Nowadays, audio CDs, Internet and DVDs are more and more widespread. However film and music content owners are still reluctant to release digital content. This is mainly due to the fact that if digital content is left unprotected, it can be copied rapidly, perfectly, at large scale, without any limitation on the number of copies and distributed easily e.g. via Internet. Protection of digital content has relied for a long time on encryption but it appeared that encryption alone is not sufficient enough to protect digital data all along its lifetime. Sooner or later, digital content has to be decrypted in order to be eventually presented to the human consumer. At this very moment, the protection offered by encryption no longer exists and an indelicate user may duplicate or manipulate it.
Digital watermarking has consequently been introduced as a complementary protection technology. The basic idea consists in hiding information imperceptibly into digital content. This watermarked signal should survive most common signal processings and even malicious ones if possible. The hidden information is inherently tied to digital content and protects it when encryption has disappeared. It is important to understand that digital watermarking does not replace encryption. Those are two complementary techniques. On one hand, encryption prevents an unauthorised user from accessing digital content in the clear during its transport. On the other hand, digital watermarking leaves an underlying invisible piece of evidence in digital data if an indelicate authorised user, who had access to the data in the clear after decryption, starts using digital data illegally (reproduction, alteration).
Depending on what information is available during the extraction process, two separate classes of watermark detectors have been defined. If the detector has access to the original data additionally to the watermarked data, the watermark detector is called non-blind. However this kind of algorithm is less and less represented nowadays. Keeping an original version of each released digital data is indeed a very strong constraint for digital content owners in terms of storage space. As a result, most of the watermark detectors are actually considered as blind: the detector has only access to the watermarked data in order to extract the hidden message.
The Figure 42.1 depicts a simple watermarking scheme with blind detection. The goal is to embed the message m into some original data do. The first step consists in encoding the message to be hidden with a secret key K. Typically the message is over sampled in order to match the dimension of the original data and is XORed with a pseudo-random noise generated thanks to a pseudorandom number generator which takes the secret key K as an input seed. Next, the generated watermark signal Wm is modified e.g. it is scaled by a given watermarking strength. The final step simply adds the obtained watermark Wa to the original data in order to obtain the watermarked data dw. This watermark embedding could be performed in whatever desired domain (spatial, Fast Fourier Transform (FFT), Discrete Cosine Transform (DCT), Fourier-Mellin). Watermarked data is then transmitted and is likely to be submitted to various processings (lossy compression, noise addition, filtering) which can be seen as attacks altering the watermark signal. If at some moment, someone wants to check if a watermark has been embedded with the secret key K in some received digital data dr, the data is simply sent through a detector. The majority of the existing detection algorithms can be seen as the computation of a correlation score between received data dr and the generated watermark Wm. This correlation score is then compared to a threshold in order to assert the presence of the watermark or not.
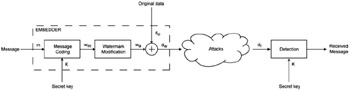
Figure 42.1: Simple watermarking scheme
There exists a complex trade-off in digital watermarking between three parameters: data payload, fidelity and robustness. It is illustrated in Figure 42.2 and further presented below.
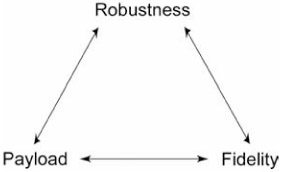
Figure 42.2: Trade-off in digital watermarking
Payload
Data payload can be defined by the number of bits that can be hidden in digital data, which is inherently tied to the number of alternative messages that can be embedded thanks to the watermarking algorithm. It should be noted that, most of the time, data payload depends on the size of the host data. The more host samples are available, the more bits can be hidden. The capacity is consequently often given in terms of bits per sample.
Fidelity
Watermarking digital content can be seen as an insertion of some watermark signal in the original content and this signal is bound to introduce some distortion. As in lossy compression, one of the requirements in digital watermarking is that this distortion should remain imperceptible. In other terms, a human observer should not be able to detect if some digital data has been watermarked or not. The watermarking process should not introduce suspicious perceptible artefacts. The fidelity can also be seen as the perceptual similarity between watermarked and unwatermarked data.
Robustness
The robustness of a watermarking scheme can be defined as the ability of the detector to extract the hidden watermark from some altered watermarked data. The alteration can be malicious or not i.e. the alteration can result from a common processing (filtering, lossy compression, noise addition) or from an attack attempting to remove the watermark (Stirmark [40], dewatermarking attack [44]). As a result, the robustness is evaluated via the survival of the watermark after attacks.
It is quite easy to see that those three parameters are conflicting. One may want to increase the watermarking strength in order to increase the robustness but this results in a more perceptible watermark on the other hand. Similarly, one can increase the data payload by decreasing the number of samples allocated to each hidden bit but this is counterbalanced by a loss of robustness.
As a result, a trade-off has to be found and it is often tied to the targeted application. It is useless to design a high capacity algorithm if there are only a few different messages to be hidden in practice. This is typically the case in a copy control application where two bits are enough to encode the three messages copy-always, copy-once and copy-never. Most of the time, the watermark signal should have a low energy so that the induced distortion remains imperceptible. However in a high degrading environment (e.g. television broadcasting), it is sometimes necessary to embed a strong watermark in order to survive the transmission. Finally some applications do not require the watermark to be robust. In fact the weakness of a fragile watermark can even be exploited in order to ensure the integrity of digital data [43]. If no watermark is found, digital data is not considered legitimate and is discarded. There is not consequently one optimal watermarking algorithm. Each watermarking scheme is based on a different trade-off and one has to be cautious when benchmarking various algorithms. It should be ensured that the methods under investigation are evaluated under quite similar conditions [29]. In other terms, in order to perform a fair performance comparison in terms of robustness, the evaluated watermarking algorithm should have roughly the same capacity and introduce approximately the same visual distortion.
The last few years have seen the emergence of a new trend in the watermarking community. The watermarking process is now seen as the transmission of a signal through a noisy channel. Original data is then seen as interfering noise which reduces significantly the amount of reliably communicable watermark information. In this new perspective, Chen and Wornell noticed a precious paper written by Costa [8]. He showed that, if a message is sent through a channel corrupted by two successive additive white Gaussian noise sources and if the transmitter knows the first noise source, interference from the first noise source can be entirely cancelled. From a watermarking point of view, the message can be seen as the watermark, the first known noise source as the original data and the second unknown noise source as the attacks. Even if Costa's model is substantially different from a real watermarking system, it means that side information at the embedder enables to reduce interference from the original data. This implication has received further support from subsequent theoretical work.
In Figure 42.1, the embedder can be seen as blind. Information contained in the original data is not exploited during the message coding and watermark modification steps. Costa's work encourages designing new algorithm based on Figure 42.3 where side information is taken into account during those two steps. Informed watermarking can be done during message coding (informed coding) and/or watermark modification (informed embedding). With informed coding, for a given message, a pool of different alternative watermarks is available and the embedder chooses the one for which the interference introduced by the original data will be minimised. With informed embedding, the goal is to optimally modify the watermark so that the detector extracts the expected message. A typical example is to perceptually shape the watermark accordingly to the original data so that fidelity is increased while robustness is maintained.
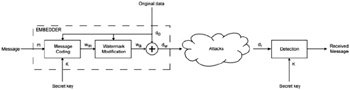
Figure 42.3: Informed watermarking scheme
Since presenting the whole theory behind digital watermarking is far beyond the scope of this chapter, the interested reader is invited to read the various books devoted to the subject. An introducing overview of digital watermarking can be found in [26]. Further details are developed in [9] where the authors even provide samples of source code. Finally an in depth discussion on informed watermarking is conducted in [19].
EAN: 2147483647
Pages: 393