Chapter 16: Mobile Ad Hoc Networks: Principles and Practices
Sridhar Radhakrishnan, Gopal Racherla, and David Furuno
16.1 Introduction
An ad hoc network [1], [2] is characterized by a collection of hosts that form a network "on-the-fly." These hosts typically communicate with each other using wireless channels; they will communicate with each other also using other hosts as intermediate hops in the communication path, if necessary. Thus, an ad hoc network is a multihop wireless network wherein each host acts also as a router. A true ad hoc network does not have an existing infrastructure to begin with; however, most real-life ad hoc networks only contain subnetworks that may be truly ad hoc. Mobile ad hoc networks (MANETs) [3], [4], [5], [6] are ad hoc networks wherein the wireless hosts have the ability to move. Mobility of hosts in MANETs has a profound impact on the topology of the network and its performance. An ad hoc network can be modeled as a graph whose nodes represent the hosts, and an edge exists between a pair of nodes if the corresponding hosts are in communication range of each other. Such a graph represents the topology of the ad hoc network, and in the case of a MANET the topology will constant change due to the mobility of the nodes. The complexity of maintaining communication increases with the increase in the rate of change of the network topology. The protocols that allow communication on the Internet tolerate very small and slow changes in the network topology as routers and hosts are added and removed. However, if applied to MANETs, these protocols would fail as the rate of change of topology is much higher. The aim of researchers working in the area of MANETs has been to develop network protocols that adapt to the fast and unpredictable changes in the network topology. In the rest of the chapter, we use the terms ad hoc network, wireless ad hoc network, and MANET synonymously; also the terms node and host in a MANET are used interchangeably.
MANETs are characterized by: [7]
-
Dynamic network topology: As the nodes move arbitrarily, the network topology changes randomly and suddenly. This can result in broken and isolated subnetworks. MANETs need to be resilient and self-healing.
-
Bandwidth-constrained, variable capacity, possibly asymmetric links: Wireless links are error-prone and have significantly lower capacity than wired links, and hence network congestion is more pronounced. Guaranteed quality of service (QoS) is difficult to accomplish and maintain in MANETs.
-
Power-constrained operation: Some or all nodes rely on batteries for energy.
-
Wireless vulnerabilities and limited physical security: MANETs are generally more prone to information and physical security threats than wired networks.
A MANET can be formed using a wireless radio network between a collection of hosts such as individuals assembled in a lecture hall, pedestrians on a street, soldiers in a battlefield, relief workers in a disaster area, or a fleet of ships and aircraft. The collection of hosts in a MANET need not be homogeneous; for example, the collection in a battlefield environment might include tanks, all-terrain vehicles, transport vehicles, infantry, and aircraft. A MANET need not be isolated or self-contained; one or more nodes in the collection of hosts could be connected to a wide area network (WAN), such as the Internet. The nodes that communicate directly with the nonmobile nodes of the WAN move traffic in and out of the MANET.
The rate of change of topology of a MANET is dependent on the characteristics of its nodes, as well as the environment in which it is used. [8], [9] For example, in the case of a group of business delegates gathering in a conference room, the topology is fairy stable after an initial setup of multiple new connections to the MANET. When the delegates leave the conference room, the MANET experiences a large number of disconnections. In a battlefield environment, where soldiers are constantly moving in different formations, the topology changes are characterized by increased numbers of link additions and deletions. Thus the rate of change of topology of the MANET is a function of the number of hosts that join and leave the network (node addition/deletion), as well as the number of connections that are added and removed (edge addition/deletion) as the nodes move in and out of the network.
In Figure 16.1, the possible stages of MANET applications, as a function of the rate of connections and disconnections, are illustrated. Applications' stages (or phases) can be static (low rate of disconnections, low rate of connections), high connection (low rate of disconnections, high rate of connections), high disconnection (high rate of disconnections, low rate of connections), and chaotic (high rate of disconnections, high rate of connections). A single application can be categorized under any of these schemes, depending on the phase in the life cycle of the application. For example, consider a battlefield environment wherein initially the soldiers (each carrying a wireless PDA for communication) are briefed at the field headquarters, the connectivity between users is high as they are in close physical proximity, and the rate of disconnections is low as the soldiers remain there until the briefing is over. This phase of the activity is classified as a high connection phase. When the same set of soldiers move in small groups on the battlefield, the rate of connection is small as they are not in radio range with all the other soldiers, and the rate of disconnection is low because the soldiers are moving together as a group. This phase of the activity can be classified as static. When the military exercise is over and the soldiers leave the network, the application is in a high disconnection phase. When reinforcements arrive to relieve a group of soldiers, the network is in a chaotic phase as the rate of disconnections and connections is high.
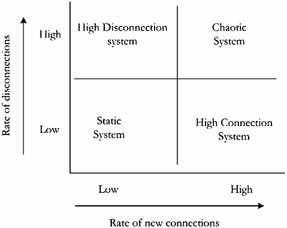
Figure 16.1: Stages of MANET applications based on rate of connections and disconnections.
For a MANET to function well, every node in the network must perform its routing duties efficiently. In addition, there must be a high level of cooperation among nodes that form the ad hoc network. As mentioned earlier, the nodes of the network can be heterogeneous in terms of their communication and computation capacities. MANET protocols must be designed and implemented with all of the MANET characteristics and issues discussed here taken into account. Network protocol issues that are important for successful deployment of an efficient MANET are discussed in this chapter. In order to better understand, we present a real-life application that requires the use of a MANET. Section 16.2 describes a MANET application involving mobile robots. Section 16.3 highlights issues that must be taken into consideration by the application, transport, network, data link, and physical layers of the protocol stack. When discussing the issues related to each of the layers, we summarize the state-of-art solutions proposed in the literature. Section 16.4 discusses the various technologies and standards that contribute to real-life implementation of MANETs. Section 16.5 summarizes the chapter and presents our conclusions.
[1]IETF MANET Charter, available at www.ietf.org/html.charters/manet-charter.html, August 2002.
[2]Perkins, C.E., Ed., Ad hoc Networking, Addison Wesley, Reading, MA, 2001.
[3]IETF MANET Charter, available at www.ietf.org/html.charters/manet-charter.html, August 2002.
[4]Perkins, C.E., Ed., Ad hoc Networking, Addison Wesley, Reading, MA, 2001.
[5]MANET Paper Collection, available at www.ee.surrey.ac.uk/Personal/G.Aggelou/MANET_PUBLICATIONS.html, August 2002.
[6]MANET Resources, available at students.cs.tamu.edu/youngbae/mcrelated.html, August 2002.
[7]IETF MANET Charter, available at www.ietf.org/html.charters/manet-charter.html, August 2002.
[8]Radhakrishnan, S. et al., DST - A routing protocol for ad hoc networks using distributed spanning trees, Proc. IEEE International Conference on Wireless Communications and Networking (WCNC '98), 1998.
[9]Racherla, G., Algorithms for routing and rerouting in mobile wireless and ad hoc networks, Ph.D. diss., University of Oklahoma, Norman, 1999.
EAN: 2147483647
Pages: 239