Sharing Remotely: Secure FTP (SFTP)
| User Level: | admin |
| Affects: | computer |
| Terminal: | no |
As I mentioned in the previous section, FTP is convenient but extremely unsecure. I just don't recommend it unless you have no other choice for sharing files, and even then I recommend creating a single, non-admin user account for sharing files via FTP. If you'd like to gain the cross-platform advantages of FTP without the security issues, you should instead consider Secure FTP (SFTP).
Like FTP, SFTP is actually a command-line method for connecting to servers and working with files. However, whereas FTP uses a clear-text connection, SFTP uses the secure shell (SSH) protocol to connect, meaning all communication between the client and server, including passwords and data, are encrypted to prevent anyone who might intercept the data from being able to use it.
The downside to using SFTP is that it requires you to enable Remote Login (SSH) on your Mac. I'll talk more about Remote Login in the next chapter, but for now you simply need to understand that it provides remote users with a console connection, and basically allows them to do anything they could do using Terminal while seated at your Mac. For non-admin users this isn't too much of a concern, but an admin-level user could wreak havoc (for example, by enabling the root account and then logging in as root, where they would have unfettered access to your system). I'll show you a way around this risk under "How Do I Configure It?"
What Does It Share?
SFTP provides the same level of access to the same directories as the default configuration of FTP Access. However, note that if you've edited the various FTP configuration files to provide more or less access over FTP, SFTP does not honor those changes.
Who Can Access Files?
Just like FTP, anyone with an account on your computer can connect via SFTP when it is enabled. They will be able to access files from any platform (Windows, Mac, or Unix).
How Do I Configure It?
Contrary to what you might think, to enable SFTP you do not have to enable FTP Access. Rather, you enable Remote Login in the Services tab of Sharing preferences. However, as I mentioned above, this also enables SSH, which allows any user on your computer to issue Terminal commands remotely. Here's how you prevent this for certain users.
Disabling SSH Access (While Still Allowing SFTP)
I'll talk more about Remote Login in the next chapter, and about default shells in Chapter 15, but for now suffice it to say that when a user logs in remotely using SSH (secure shell), their default shell is loaded. The shell is how they work with the Terminal's command line, and using it they can access almost any command-line application (including the sftp utility). In addition, each user has a configuration file that determines what their default shell is (there are several different popular shells that can be used). Using these two facts, we can edit a user's account settings so that instead of a shell, only the SFTP application itself is loaded—thus allowing them to use SFTP remotely, but disallowing any other remote activity. Here's how:
-
If Remote Login is enabled, disable it in Sharing preferences.
-
Open NetInfo Manager and authenticate by clicking the padlock icon.
-
Using the directory browser, navigate to /users/username, where username is the user for whom you want to restrict access to just SFTP. Select that username.
-
In the Property/Value(s) window, scroll down to the "shell" property. Double-click on the corresponding entry in the Value(s) column (which will most likely be /bin/tcsh) to make it editable.
-
Delete the existing value, and type /usr/libexec/sftp-server in its place (Figure 10.5).
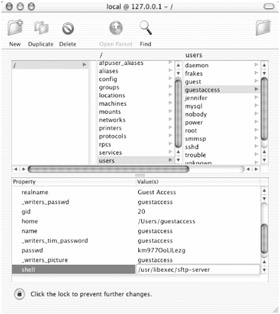
Figure 10.5: Using NetInfo Manager to limit a user's Remote Login capability to SFTP -
Choose Domain ➣ Save Changes to save your changes, and then quit NetInfo Manager.
-
Re-enable Remote Login in Sharing preferences.
What you just did was tell OS X that when the user logs in, the default shell it should load is sftp-server, which isn't really a shell. Since the sftp-server application is the command-line utility used to access files via SFTP, the user will still be able to access files (either using the command-line or a graphical SFTP client, as described in "How Do Others Access Files?"), but they won't be able to do anything else.
| Note | The downside to this procedure is that as long as the user's default shell is set to sftp-server, they won't be able to use Terminal or perform any type of command-line activity, even if they're sitting at your computer. However, you can easily edit their account in Net-Info Manager to restore their default shell when needed. This tip is useful mainly for remote users who have no use for full shell access. |
How Do Others Access Files?
Just as with FTP, users will be able to access files via SFTP using any SFTP client. (In fact, many FTP clients also support SFTP; however, you need to specifically tell them to use SFTP instead of FTP when connecting.) In their SFTP client, they should enter your IP address or domain name as the server address, and use their username and password on your computer as their login name and password.
Alternatively, since SFTP uses the command-line application sftp, just like FTP uses ftp, users can connect through a terminal or console application by using the command sftp youripaddress, at which time they'll be prompted for their username and password. Once they're logged in, they can use sftp commands to access files.
|
|