Designing Security for Remote Access Users
| Today's networks don't stop at the walls of buildings. Many users work outside the office from home or other locations. Users might need access to resources in their intranet from anywhere in the world. A modern network would not be complete without a way to provide this access. Providing Remote Access creates new challenges for administrators in regard to the design and maintenance of a network. Challenges include security, connectivity, and availability. An effective Remote Access network design must include a method of access that's transparent to the user but secure for the organization's needs. Microsoft server operating systems prior to Windows 2000 offered very little security for Remote Access. Windows 2000 increased Remote Access security tremendously over that of Windows NT. Windows Server 2003 has new features that make it the most flexible and secure system for Remote Access to date:
We now move on to examine these systems in light of the security that they provide to a Remote Access network design. Remote Access PolicesRemote Access policies are made up of flexible rules and settings that define when, where, and how a user is able to gain remote access to a network. These policies give an administrator granular control over a user's access while keeping the administrator totally transparent to the user. Remote Access policies are actually made up of three components. A well-designed network uses a combination of these three components to determine who can gain remote access to a network, when they can get in, and what authentication and encryption protocols they have to use. These components are the following:
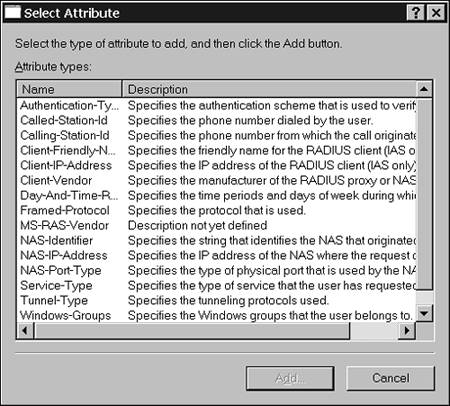
Each of these components plays a key role in Remote Access policies. They are processed in the order listed: conditions, permissions, and profile. Let's take a closer look at each of these components and their relation to a secure design of a Windows Server 2003 Remote Access server. ConditionsConditions are parameters that must be met for a user to gain access to a network. Conditions are looked at only at the time of initial access to the network. These could include the requirement that a user is a member of a security group, that the user is using a certain type of connection, or that it is a certain time of day. These are only a few examples of conditions that can be applied to a Remote Access policy. Figure 5.9 illustrates the many types of conditions that can be applied to a Remote Access policy. Figure 5.9. You can configure Remote Access policy conditions.
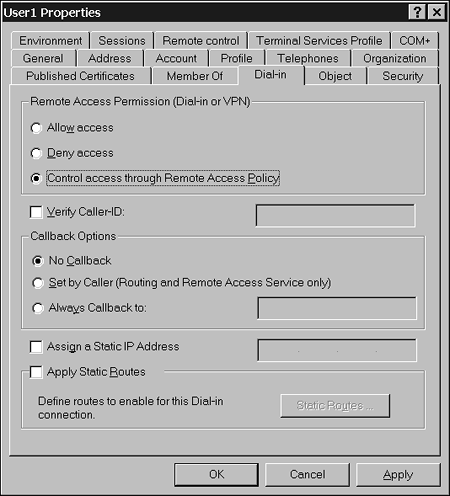
PermissionsPermissions are set on the user's account properties on the Dial-In tab. The default Dial-In permissions for users varies depending on whether the domain is in mixed mode or native mode. In mixed mode, the default dial-in permissions for all users is Deny. This keeps the Remote Access server secure until the administrator changes the permissions. In native mode, the default permissions is Control Access Through Remote Access Policy, but the only default policy is a deny for everyone at all times. This has the same effect as the Deny permissions in mixed mode; the users cannot use the Remote Access server until the administrator changes the permissions. If this policy is deleted and no other policies are added, all attempts will be denied. Figure 5.10 illustrates the options of permissions in native mode. The third option, Control Access Through Remote Access Policy, would be grayed out in mixed mode. Figure 5.10. You can configure Remote Access permission settings for an account.
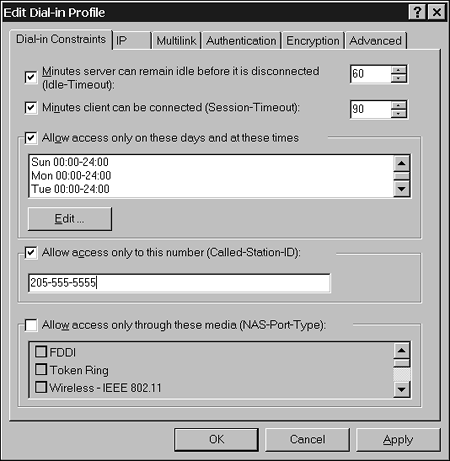
ProfileA profile is a set of rules that must be met to maintain a connection with a Remote Access server. Whereas the user's conditions are checked only once, the user's profile is continually checked by the system when he tries to gain access to a network. Elements of a profile could include a requirement that a specific encryption protocol or authentication protocol must be used. Other settings include Idle Time Out and Session Time Out. Profiles give Windows Server 2003 administrators very granular control over Remote Access services. Figure 5.11 illustrates the settings available for profiles in Remote Access policies. Figure 5.11. You can configure Remote Access policy profile settings.
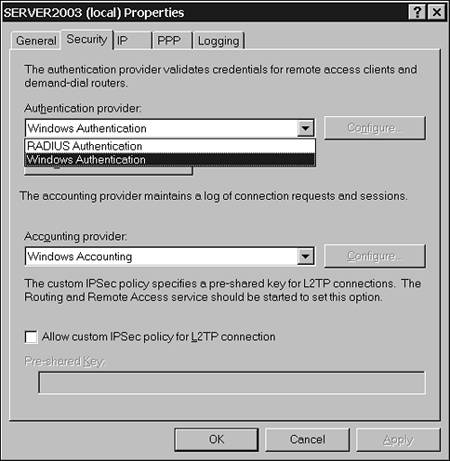
Internet Authentication ServicesIn large networks containing multiple Remote Access servers, Remote Access policies can become very complex. Different servers might contain completely different policies, which could result in confusion for users as well as administrators. Internet Authentication Services is a system that takes charge of the Remote Access policies and centralizes them on one server. In addition, use of the servers can be centrally logged so that a large company can track bandwidth usage for different departments or organizations within the company. The server that contains Internet Authentication Services is called the RADIUS (remote authentication dial-in user service) server. RADIUS clients are therefore RAS (Remote Access Service) servers. You can set a RAS server to provide its own authentication and logging or give these over to a RADIUS server. A RADIUS server can be configured to accept the clients (RAS servers) and provide a central store for all Remote Access policies and logged information. Figure 5.12 illustrates these settings on a RAS server. Figure 5.12. You can configure RAS server authentication and logging settings.
|
EAN: 2147483647
Pages: 152