SCSI Command Basics
| SCSI has a rich command language that is used to move data between systems and storage quickly and accurately. Unlike commands used with systems and networking equipment, SCSI commands are rarely, if ever, entered from a command line or graphical user interface (GUI) by an administrator. Instead, SCSI commands are implemented programmatically and are embedded in software products, such as file systems and backup software. The sections that follow give a very abbreviated view of this deep and rich subject, including the following topics:
Command Descriptor BlocksProtocols provide a defined format for communications, allowing sending and receiving nodes to agree completely on what is being communicated. The format of the information that is exchanged is called a protocol data unit (PDU). The PDU for SCSI commands is called a command descriptor block (CDB). Initiators create CDBs, and the device server running in the logical unit interprets them. When the logical unit has finished processing the command, it responds by returning a status code for the command, along with any accompanying data, to the initiator. Unlike most networking protocols, which have regularly-sized packet or frame sizes, SCSI CDBs do not have a prescribed, consistent length. Some commands are short, while others can be long. Implementations of SCSI-3 such as the Fibre Channel FCP protocol, define the way SCSI CDBs are mapped into their corresponding fixed-size network PDUs. SCSI status codes have meanings that do not necessarily coincide with human intuition. A response signaling that a task has completed simply means that the task has finished processing; it does not necessarily mean that the intent of the command completed successfully. Only experienced storage and systems administrators who know what the status codes mean should attempt to use them when troubleshooting system I/O problems. Types of SCSI CommandsThere are several different types of commands in SCSI, reflecting the diversity of systems and devices it supports. In fact, multiple subcommittees in the T10 organization work on different subsets of the total specification. Some of the various types of commands in SCSI are as follows:
Basic SCSI CommandsThe SCSI commands used most often for storage I/O transmissions are the READ and WRITE commands. READ commands request data to be sent by a logical unit in a storage target to the initiator, where it is then sent to a requesting application. WRITE commands request that data that is sent from the initiator to the logical unit be written to storage media. The intent of these commands is not just to transfer data between initiators and targets but to ensure that it reaches its eventual destination. There are several variations of both READ and WRITE commands. Three other commonly used SCSI commands are MODE SENSE, MODE SELECT, and REPORT LUNS. The MODE SENSE and MODE SELECT commands are used together by applications to determine what operating capabilities (modes) a storage device or logical device has and to choose to use one of those modes. For instance, a MODE SENSE command could be used to discover the ways a tape drive can handle end-of-tape conditions. MODE SELECT could then be used by a backup application to work in the optimal fashion with the software's logic. The REPORT LUNS command is used by an initiator when it attempts to discover what LUNs are available through a specific device port. After receiving the REPORT LUNS command, a target responds with an inventory of all the available LUNs exported through the port the command was received on. The REPORT LUNS command is at the core of how LUN masking works in SAN storage subsystems, as discussed in Chapter 5, "Storage Subsystems." By not including certain LUNs in the inventory that is returned to the initiator, the initiator will not discover them and try to use them. While there is a lot of flexibility in how storage devices are designed, all SCSI targets are required to support four commands: INQUIRY, READ CAPACITY, REQUEST SENSE, and TEST UNIT READY. The SCSI INQUIRY command is used to discover what the configuration is for a target and logical unit, including such things as manufacturers and product identification, version numbers, and information about its command support. READ CAPACITY is used by a system to discover the block size and the number of blocks used in a storage address space. The REQUEST SENSE command is used to query about command status, and the TEST UNIT READY command is a way to determine if a device and its media are available to commence operations. SCSI ReservationCertain SCSI commands reserve storage devices for the use of specific applications servers. This feature is particularly useful for backup applications where it is desired to reserve the use of tape drives and tapes for the highest-priority servers. This mechanism also includes a way to remove reservations. The SCSI reservation mechanism was not used much prior to the advent of SANs. However, with the potential for many servers to back up data over a SAN to centralized backup storage, it became obvious that the SCSI reservation mechanism could be useful. This topic is discussed more in Chapter 13, "Network Backup: The Foundation of Storage Management." Extended Copy and Third-Party CopyA relatively new SCSI command that is primarily applicable to SAN environments is the EXTENDED COPY command. EXTENDED COPY allows dual-mode SCSI controllers to act as "proxy" initiators that copy data on behalf of another initiator. A controller supporting this function receives an EXTENDED COPY command from an initiator and then issues READ and WRITE commands to specified logical units for a specific block range of data. The terms third-party copy, x-copy, and e-copy are all used to refer to the function provided by the EXTENDED COPY command. Figure 6-7 illustrates the mechanism used for EXTENDED COPY. Figure 6-7. SCSI EXTENDED COPY Processing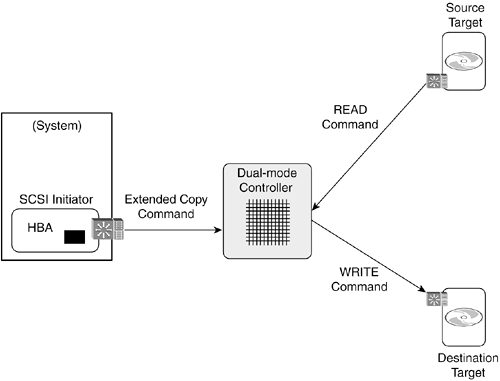 In Figure 6-7, an initiator in a system sends an EXTENDED COPY command to a dual-mode storage controller. Acting as a SCSI target, this controller receives and interprets the EXTENDED COPY command and then proceeds to execute its initiator role by reading data from the source target and writing it to a destination target. The network ports on the dual-mode controller are not shown. There could be a single port or multiple ports. The actual port configuration does not impact the SCSI function, which is independent of the connecting technology. The EXTENDED COPY command was designed to enable the transfer of data between different types of storage devices, such as disk, tape, and optical devices/subsystems. But it can also be used to transfer data between different virtual storage resources within the same subsystem. Intuitively, EXTENDED COPY would seem to make a lot of sense for performing backups in a SAN. Using EXTENDED COPY allows systems to be bypassed while transferring large amounts of backup data. However, the concept is far simpler than the implementation due to the necessity of synchronizing host system software operations to ensure data integrity. The topic of third-party copy backup is discussed in more detail in Chapter 13. |
EAN: 2147483647
Pages: 184