The Components of IS Strategies, Policies, Standards, and Procedures
| As an IS auditor, you can learn a significant amount about an organization by reviewing the strategic plan and organizational and lower-level policies. These documents can provide background on the business objectives and mission, as well as the line or operational policies supporting that mission. If you review strategy and policies before doing observation and conducting interviews, you might identify areas in which potential gaps exist, help define whether the organization has a clear process for policy development, and determine whether the organization is using a top-down or bottom-up approach to policy development. Policy DevelopmentOrganizations follow different approaches in policy development. The top-down approach aligns organization-wide policies with the business strategy; department- and office-level policy then is created in accordance with strategy and organizational policy. The top-down approach works to ensure that all policies are aligned with the organizational strategy, but it generally requires more time to develop and implement and might not address immediate operation priorities of the organization. Other organizations create policy using the bottom-up approach. They identify immediate areas of concern, compliance, or risk, and develop policy for those areas by performing a risk assessment. Although this approach is more time- and cost-effective, it creates the risk that policies might not align with organizational policies and strategy.
A bottom-up approach to the development of organizational policies is often driven by a risk assessment. A variety of policy types exist, and it is important that the organization and the auditor understand the distinction between policy types and their enforcement:
In addition to different policy types, different subsets of the organization need to develop and comply with lower-level policies. Human resources policies at the policy level are those that most of us are familiar with; these policies pertain to training, travel, hiring, promotion, and termination. These policies are implemented organization-wide, regardless of function or authority level, and they guide the actions of employees. The policies should have a process for review as well as communication within the organization, and should address both the long- and short-term objectives of the organization. There are a variety of methods for communicating policy; these might take the form of awareness training, employee manuals, company newsletters, or legal banners. It is important that clear responsibilities are defined and programs are put in place to ensure that employees are aware of and understand the organization's policies. IT PolicyAlthough senior managers are responsible for the development, review, and communication of policy, a significant portion of policies pertains to information systems acquisition (hardware/software), compliance, security, network and operations, continuity of operations, and financial/accounting policies. Table 2.1 lists some definitions of policy types that are used by organizations and that pertain to IT functions.
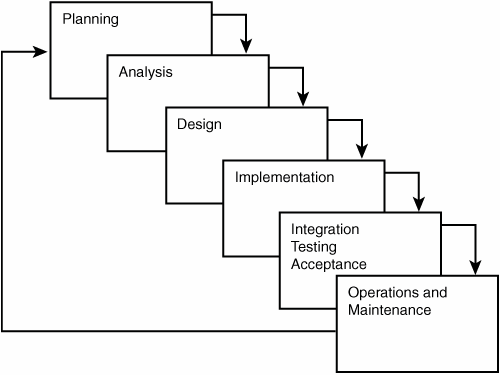
Policies are high-level documents that align with the business strategy (both long and short term) and represent the corporate philosophy. The organization's management is responsible for the formulation, documentation, communication, and control of policies. The development of these policies and their implementation show an organization's commitment (due care and diligence) to the use, operation, and security of information systems. IS auditors should look for both policies and procedures that apply to all phases of the system development life cycle (SDLC) and ensure that they align with the organization's strategy. The SDLC encompasses the planning, analysis, design, implementation, integration/testing, acceptance, maintenance, and security of information systems. The SDLC is a formal model that represents the phased implementation of information systems. The definition of detailed tasks might change by organization, but Figure 2.1 outlines the high-level tasks of an SDLC. Figure 2.1. SDLC diagram. ProceduresProcedures are detailed documents that incorporate the intent of the parent policy and that document administrative and operational processes. In some cases, procedures provide step-by-step details for performing a function and writing in a clear and concise manner to allow easy understanding and implementation. The procedures outline how to perform various business processes within the IT environment and the controls associated with them. The change in business process should drive policy and procedure changes, but this is not always the case. In today's fast-moving business environment, it is not uncommon for business processes to frequently change because of procedures, compliance, or the influence of new technologies in the organization. An IS auditor must pay particular attention to the process for review and implementation of procedures because they are the most fluid documents in the organization. In addition, the auditor might find through direct observation or interviews that the defined procedures are not being followed. This is an indication that there is no defined process for review and update of the procedures, or that the people working in the operational environments are not properly trained on the procedures associated with their function. The lack of procedures or adherence to procedures could be indicators of a larger issue: Necessary controls in the environment are being bypassed by ad-hoc procedures. In this case, the procedure, or lack thereof, makes it difficult for the auditor to identify controls and ensure that the process is efficient and secure.
When determining the effectiveness of IS policies communication, an auditor typically reviews interviews with user and IS personnel, information-processing facilities operations and procedures manuals, and user department systems and procedures manuals. |