Activating the FTP Server
FTP (File Transfer Protocol) is the oldest such protocol on the Internet and is still widely used. Virtually all Web browsers are capable of acting as clients with FTP servers, and there are several GUI and command-line clients for FTP (see Chapter 10).
FTP connections are not encrypted, so all data, including user names and passwords, sent over an FTP connection is vulnerable to being intercepted and read. You should never use or allow FTP to be used to transfer unencrypted confidential information, or use user name /password combinations that give access to confidential information elsewhere.

Mac OS X comes with an FTP server that can be activated from the Sharing pane of System Preferences.
To activate the FTP server using the GUI:
| 1. | Open the Sharing pane of System Preferences and choose the Services tab ( Figure 14.4 ). Figure 14.4. System Preferences with the Sharing pane and the Services tab selected.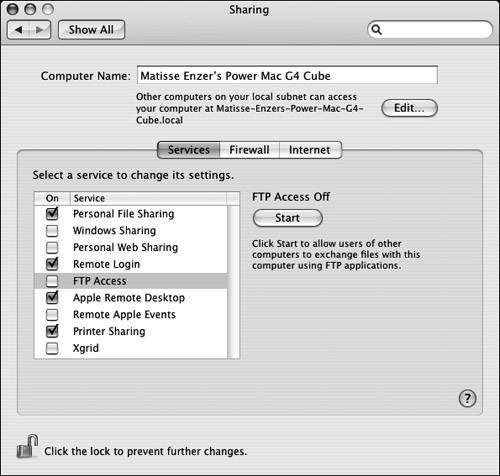 If the lock icon in the lower left is locked, click it and authenticate as an admin user. |
| 2. | Click the FTP Access item. |
| 3. | Either click the Start button or check the box next to FTP Access. The pane shows the FTP server as running, and the Start button changes to Stop ( Figure 14.5 ). (If your button already said Stop, your FTP server was already running.) Figure 14.5. The FTP server is now runningthe Start button has changed to Stop.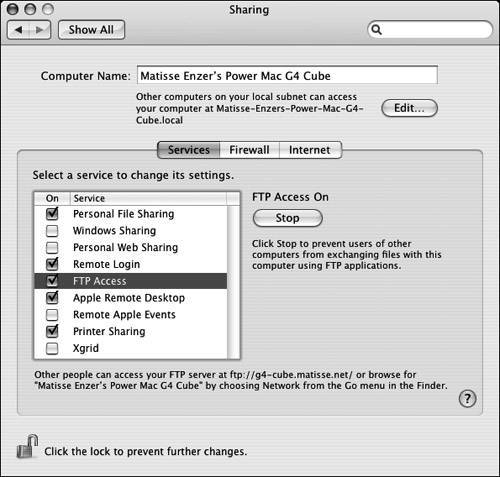 In the Unix layer of Mac OS X, the operating system simply does the following (as root): launchctl load -w System/Library/ which tells launchd to load a daemon labeled com.apple. ftpd . You can see that it is loaded with sudo launchctl list (See the launchd section in Chapter 11.) |
| 4. | Close System Preferences. |
| 5. | Test the server. Do this by logging in via FTP, preferably from another machine, or you can also do it from your own machine. |
 Tips
Tips
-
If you have the firewall running, FTP access to your machine will not work for many users, because the firewall will block "passive FTP" access. See the task "To allow Passive FTP access through the firewall," below.

-
The FTP daemon that Apple uses in Mac OS X 10.4 is tnftpd . See man tnftpd and man ftpd.conf for details on its capabilities.
-
To inactivate the FTP server, just repeat steps 1 and 2 above and click Stop.
Of course, you can also activate the FTP server without ever leaving the command line.
To activate the FTP server from the command line:
- sudo launchctl load -w /System/
 Library/LaunchDaemons/ftp.plist
Library/LaunchDaemons/ftp.plist
If you have the firewall turned on, you must allow access on port 21. See Chapter 12 for more on the firewall tool.
 Tips
Tips
-
Table 14.1 lists various files used by ftpd , the FTP server.
-
You can deactivate the FTP server from the command line with
sudo launchctl unload -w /System/
 Library/LaunchDaemons/ftp.plist
Library/LaunchDaemons/ftp.plist
-
See Chapter 11 for more on launchctl and launchd .
Table 14.1. Files Used by ftpd
| F ILE | U SE |
|---|---|
| /usr/libexec/ftpd | The FTP server itself. See man ftpd . |
| /etc/ftpusers | List of users who may not connect to the FTP server. |
| /etc/ ftpchroot | List of users whose use of FTP is restricted to their home directory. See man chroot . |
| /etc/ftpwelcome | Contents of this file are displayed when a user logs in via FTP. |
| /etc/ nologin | If this file exists, it is displayed to users attempting to log in, and access is refused . |
| /var/log/ftp.log | Log of FTP connections and file transfers. |
| /var/log/ftpd | Log of file FTP connections. |
About Passive vs. Active FTP
The FTP protocol has two modes: Active and Passive.
Many client machines will be unable to use Active mode connections to FTP servers because the firewall on the client machine or local network will block the data connection from the server back to the client. Active mode may also be blocked if the client is using Network Address Translation ( NAT ) to obtain access to the network, and has a non-routable IP address. FTP uses two connections (also called channels ) between the client and servera command connection and a data connection. In both Active and Passive modes the client initiates the command connection to port 21 on the FTP server. (Review "About ports and sockets," in Chapter 12, for more on port numbers .)
In Active mode the server (not the client) initiates the data connection back to the client from port 20 on the server machine. In Passive mode the client, not the server, initiates the data connection to a random port number between 1024 and 65535 on the server. (The server may tell the client to select from a smaller range.)
In Active mode the client machine must be able to accept the data connections that are initiated by the FTP server, and this will often be blocked by firewall software on the client side. In Passive mode the client initiates both connections, so the firewall on the client side will typically allow it.
In Active mode the FTP server must have port 21 open in its firewall configuration (if it is using a firewall). In Passive mode the server must have port 21 and all or some of the ports above 1023 open. That is what we are going to show you how to do in the following task.
To allow Passive FTP access through the firewall:
| 1. | Open a range of ports in the firewall. Figure 14.6 shows an example of opening ports 5000 through 5050. Figure 14.6. Opening ports 50005050 on the Firewall tab of the Sharing pane in System Preferences.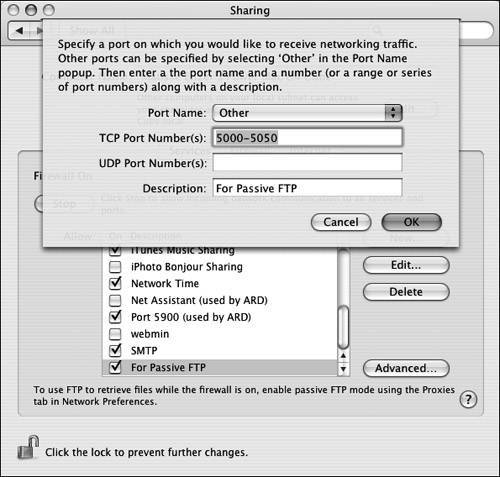 |
| 2. | Add the portrange directive to /etc/ftpd.conf . If that file doesn't exist, create it. You need to add the following line to the file: portrange min max where min is the lower port number you used in step 1, and max is the higher numberfor example: portrange 5000 5050 |
| 3. | Restart the FTP server. You can do this on the Services tab of the Sharing pane in System Preferences, or from the command line with sudo launchctl unload -w /System/ |
Allowing anonymous FTP access
Before there were Web sites, there were anonymous FTP sites.
An anonymous FTP server allows users who do not have an account on your system to download files. You can see how HTTP and Web servers have become the dominant tools for this role. Still, FTP is widely used to allow public downloading (and, less frequently, uploading) of files.
Anonymous FTP involves the user's logging in with a special account called "anonymous" (the user name "ftp" can also be used as a shorter alternative).
Anonymous FTP logins do not need a password. It is traditional to use one's e-mail address as a password.
The FTP server is designed to take special security precautions for anonymous logins to make sure that anonymous users cannot access anything outside the directory established for anonymous FTP use.
To allow anonymous FTP access (no password):
| 1. | sudo -s You will need to perform all the following steps as root, so here you are starting a root shell.
| |
| 2. | dsidentity -a ftp -c "Anonymous FTP User" This creates a new "identity" account on your system, which will have a real user name ("ftp" in this case) but a home directory and login shell of /dev/null , which is perfect for our purposes here. See man dsidentity and the sidebar "Adding a User from the Command Line," in Chapter 11, for some discussion of the intricacies of adding a "normal" user account from the command line. | |
| 3. | mkdir -m 555 /Users/ftp Since the dsidentity command doesn't create a home directory for the new ftp user, you create one here. The directory can be anywhere on your file system. The -m 555 option sets the permissions (mode) on the directory to -r-xr-xr-x , so no one has write permission on the directory (but root can still write to it). We use /Users/ftp as an example here, but you could just as well create /var/ftp or /usr/local/ftp , for example. If you choose a different location than /Users/ftp , make sure to adjust your actions in steps 3, 4, and 5 to use the proper directory.
| |
| 4. | mkdir -m 555 /Users/ftp/pub This is the top-level directory where you will put files for people to download. When users log in to your FTP server, they will be in this directory. Optionally create a .message file in this and/or any subdirectories. The FTP server will display the contents of a .message file that it finds in any directory the user enters. A typical use would be to explain the contents of a particular directory. | |
| 5. | Put some files in /Users/ftp/pub . These are the files you are making publicly available. You can put as many as you like. You can (and should) have subdirectories for different groups of files. As noted in step 4 above, if you put a .message file in a directory, it will be displayed when an FTP user enters that directory. | |
| 6. | Create or edit /etc/ftpd.conf . You want to end up with a file that looks like that in Figure 14.7 . Figure 14.7. Example of /etc/ftpd.conf set up for anonymous FTP access.# /etc/ftpd.conf # This is a comment. I love comments. # Based on the examples/ftpd.conf in the source code. # Full source code available from http://freshmeat.net/projects/tnftpd # See man tnftpd and man ftpd.conf # Set maximum transfer rate to 16384 bytes/second (128 Kbits/sec) rateget all 16384 # Check PORT command for validity; prevents denial of service attempt. checkportcmd all # For anonymous connections, when a directory is entered show the contents # of `.message' if it exists, and notify about any files that start # with `README'. display guest .message notify guest README* # Prevent uploads & modification commands for anonymous connections upload guest off # Limit the number of simultaneous `guest' class connections to 5, # and display /etc/ftptoomany when this limit is reached. limit guest 5 ftptoomany # Disconnect if an invalid username is entered, do not even ask for password denyquick guest chroot guest /Users/ftp homedir guest /pub # Specify a range of port numbers to use for passive connections. # If a firewall is in use these ports must be opened up. portrange all 5000 5050 Mac OS X 10.4 doesn't come with an /etc/ftpd.conf file, relying entirely on the FTP server's default configuration, but a later version of Mac OS might have installed one. If the file already exists, make a backup copy before editing. Note that the chroot directive in /etc/ftpd.conf must point to the directory you created in step 4 above.
| |
| 7. | Edit /etc/ftpusers . Make a backup copy before editing the file. You want to end up with a file like that in Figure 14.8 . You are allowing access to your FTP server only via anonymous FTP.
Figure 14.8. Example of /etc/ftpusers set up to allow only anonymous FTP access.# This is a comment. I love comments. # /etc/ftpusers - access control for tnftpd # Based on the examples/ftpusers file in the source code. # Full source code available from http://freshmeat.net/projects/tnftpd # See man ftpusers and man tnftpd # This configuration is for an anonymous-only FTP server # Permit anonymous ftp connections (both entries are required, # because the username `anonymous' is often used.) # ftp allow anonymous allow # Deny access to all other usernames * deny | |
| 8. | Create the file /etc/ftptoomany . This file will be displayed to users trying to connect if the limit specified by the limit directive in /etc/ftpd.conf is reached. The file might contain "We are too busylimit of 50 users reached. Please try again later." | |
| 9. | Start the FTP server. From the command line: launchctl load -w /System/Library/ or use the Sharing pane in System Preferences. The FTP server logs activity to /var/log/ftp.log , so you can watch it (perhaps in a separate Terminal window) with tail -f /var/log/ftp.log | |
| 10. | exit This terminates the root shell you started in step 1 and gets you back to your regular shell prompt. | |
| 11. | Log in and try anonymous FTP access. You can use any FTP client you like. The /pub directory is where the file will be. The hostname to connect is the FQDN for your machine (see "Setting Your Machine's Hostname," at the beginning of this chapter) or your machine's IP address. Or, if you are connecting from the same machine, you can use the hostname "localhost." Examples include ftp your.hostname.example.com ftp nnn.nnn.nn.nnn ftp localhost When you connect, enter a username of either anonymous or ftp. When asked for a password, you can supply anythingor nothing (just press If you are using an FTP client such as a Web browser, then the URL is ftp:// hostname / Accesses will be logged to the file /var/log/ftp.log . |
Sometimes you want to allow anonymous FTP users to upload files as well as download them.
The proper way to do this involves creating a special directory (typically called incoming ) where FTP users can use the put command to upload files. When properly set up, the incoming directory does not allow users to see the files it contains (although if they can guess a filename, they can download it), and if they upload a file with the same name as an existing file, the new file is renamed by adding a .1 to the filename (or .2 , or .3 , and so on).
The following task assumes that you have already set up anonymous FTP access.
To allow anonymous FTP users to upload files to your server:
| 1. | sudo -s You'll need to be root for this task, so start a root shell. Enter your password if asked. |
| 2. | Create a new directory called incoming in the FTP pub directory. So if your FTP pub directory is /Users/ftp/pub , then the command line is mkdir -m 333 /Users/ftp/pub/incoming The permission mode 333 means that all users may write and execute the directory but may not read it (of course root can read it). This allows anonymous FTP users to cd into the directory and upload files but not to list the directory's contents.
|
| 3. | Make changes to /etc/ftpd.conf . Make a backup copy and then edit /etc/ftpd.conf , removing or commenting-out this line: upload guest off and adding these lines: # Set max size in bytes for uploads. maxfilesize guest 10485760 (10485760 bytes is 10 megabytesyou may change that to anything you like, or -1 for no limit). |
| 4. | exit This terminates the root shell you started in step 1 and returns you to your regular shell prompt. |
| 5. | You're done. Anonymous FTP users can now upload files into the incoming directory. |
 Tip
Tip
-
You may want to create a script that's run from cron to send e-mail to someone whenever files are added to the incoming directory. See the section "Running Regularly Scheduled Commands," in Chapter 11, for instructions on setting up a cron job or a LaunchDaemon. Figure 14.9 is a sample script you could set to run every 15 minutes (or whatever frequency seems convenient ).
If it's run as a cron job, the output from the script is e-mailed (by cron ). On the other hand, a LaunchDaemon can be configured to watch a directory and run a script whenever the directory is not empty.
The script produces output the first time it finds files in the /Users/ftp/pub/incoming directory, and it creates a marker file (just a file whose presence is an indication of something) to avoid sending e-mail every time it runs (you remove the marker file to re-enable the script).
Figure 14.9. Code listing of a sample script to be used as a cron job, to send notification when files are added to the anonymous FTP upload directory.
#!/bin/sh # Script for checking if files have been uploaded via Anonymous FTP # This script could be run as a cron job, perhaps every 15 minutes. # It will produce output the first time it finds files in the # /Users/ftp/pub/incoming directory. # After cleaning out the incoming directory you need to also remove # the marker file so this script will send email again. # Name of file that we use as a marker NOTICE_FILE="incoming_has_files" # cd to the ftp pub directory cd /Users/ftp/pub # Get the contents of the incoming/ directory contents=`/bin/ls incoming/` if [ "$contents" != "" ] ; then if [ ! -e "$NOTICE_FILE" ] ; then echo "Anonymous FTP incoming files:" echo "$contents" # Create the notice file so we don't get email again # until someone clears it out. /bin/date > "$NOTICE_FILE" echo "Remember to remove ~ftp/$NOTICE_FILE" fi fi # Otherwise, remain silent
Reducing the security risks from an FTP server
Because of the security risk from password sniffing, you must assume that any user name and password used to access your FTP server can be obtained by an unauthorized person.
If you are running an FTP server to provide only anonymous access, then this is not an issue, since the account used for anonymous FTP is not one that people can use to log in to your machine.
Secure Alternatives to FTPThe primary secure alternatives to FTP are file transfers that use the SSH protocol. Chapter 10 covers the client side of these methods using the ssh and sftp commands. |
You can reduce the risks that come from running an FTP server by treating all FTP logins in a manner similar to anonymous logins:
-
Set up separate FTP-only accounts that cannot be used to log in on the command line.
-
Configure the FTP server to place access restrictions on the FTP-only accounts so that they cannot access anything outside their home directories.
-
Forbid any user except anonymous-access and the special FTP-only accounts from logging in via FTP.
See Chapter 12 for more Unix security information.
To increase the security restrictions when a user logs in via FTP:
- Add the user name to /etc/ftpchroot .
This prevents the user from accessing any files outside his or her home directory when logging in via FTP ( chroot means "change the root directory the user sees"; see man chroot ).
If the file /etc/ftpchroot doesn't exist, you must create it. You must be root (use sudo ) to create or edit that file. It simply contains one user name per line. Figure 14.10 shows an example.
Figure 14.10. Example of a /etc/ftpchroot file.
# Users who get a chroot'd environment # (See man chroot ) puffball mary johnftp xaos jackftp
One of the best things you can do to reduce the risks created by running an FTP server is to allow only specially restricted FTP-only accounts to access your system via FTP.
To create FTP-only user accounts:
| 1. | Create a new user account. See "To create a new user," in Chapter 11. This account will be configured so that it has access only via FTP. The password for this account should not be the same as the password for another account. |
| 2. | Change the user's shell to /usr/bin/false . See "Changing a user's login shell," in Chapter 11. Having /usr/bin/false as the login shell for an account means that as soon as someone logs in, he or she is instantly logged out. We want to prevent someone who obtains this account's password from logging in at the command line, where that user's opportunity for mischief is much greater than through FTP. Logging in via FTP and logging in to a command-line shell are two different things. When a user logs in at the command line, the operating system executes his or her login shellthat is, the program that accepts command-line input (review Chapter 2). The program /usr/bin/false is a tiny program that quits as soon as it is started and gives a return code meaning "false" to whatever program ran it. The FTP server will allow logins only from accounts whose login shell is listed in the file /etc/ shells , so if this is the first FTP-only account you have created, you must add /usr/bin/false to the list of valid shells in the file /etc/shells . Figure 14.11 shows /etc/shells with the added entry. Figure 14.11. The file /etc/shells , with /usr/bin/false added.# List of acceptable shells for chpass(1). # Ftpd will not allow users to connect who are not using # one of these shells. /bin/bash /bin/csh /bin/ksh /bin/sh /bin/tcsh /bin/zsh /usr/bin/false |
| 3. | Add the new user name to /etc/ftpchroot . If a user name is listed in the file /etc/ftpchroot , then the FTP server applies additional access restrictions to the account, preventing access to any file outside the account's home directory. |
To prevent a particular user from connecting to the FTP server:
- Add a deny entry for the user to /etc/ftpusers .
For example, to deny FTP access to user "quagmire," add the following line to /etc/ftpusers :
quagmire deny
EAN: 2147483647
Pages: 161