4.3 Runtime patterns
|
| < Day Day Up > |
|
4.3 Runtime patterns
The next step is to choose Runtime patterns that most closely match the requirements of the application. A Runtime pattern uses nodes to group functional and operational components. The nodes are interconnected to solve a business problem. Each Application pattern leads to one or more underpinning Runtime patterns.
We can overlay the Application pattern onto the Runtime pattern to identify where business logic is deployed on nodes. The Runtime patterns illustrated give some typical examples of possible solutions, but should not be considered exhaustive.
To understand the Runtime pattern, you will need to review the node definitions provided in 5.1, "Node types" on page 98.
| Note | We cover Runtime patterns for Exposed Direct Connection in this section. Look for details on the Exposed Broker runtime pattern or the Exposed Serial Process runtime pattern in a future redbook. |
4.3.1 Runtime patterns for Exposed Direct Connection
When using the Exposed Direct Connection runtime pattern, shown in Figure 4-9, the source application uses a connector to access the target application.
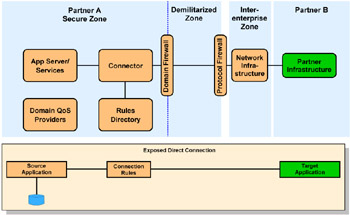
Figure 4-9: Exposed Direct Connection runtime pattern
The connector itself may be explicitly or implicitly modeled. If the connector is explicitly modeled, the modeler can use decomposition and abstraction techniques to expand the connector to the appropriate level of detail.
The term Connector may be qualified by both the connector variation and by the interaction variation. Some examples are:
-
Adapter Connector
-
Path Connector
-
Message Connector
-
Call Connector
-
Call Adapter Connector
The target application relies on services provided by its hosting server. These are modeled using the Application Server/Services component.
The Rules Directory and Domain QoS Providers may or may not exist. If they do exist, it is a modeling decision as to whether they need to be shown in the Runtime pattern. For example, analysis may determine that connection rules are not an important part of the solution, so the Rules Directory may be left off the Runtime pattern.
Figure 4-9 shows a standard pattern of Path Connectors (firewalls and network infrastructure), but other variations do exist with fewer or more firewalls.
The secure zone Connector is primarily concerned with logical connection of the Path Connector to the Application Services, and will therefore often be modeled as an Adapter Connector.
Less secure applications and connectors may be placed within the Demilitarized Zone, depending on local security policies; they are usually placed as shown in Figure 4-9.
This Runtime pattern allows two different organizations to talk to each other with a mutually agreed message format and protocol. Each partner can use their own internal messaging format, using a connector adapter to convert from the internal format to the external format.
You may notice that we don't have separate Runtime patterns for the message and call variations of the Exposed Direct Connection application pattern. It is still important to identify that your business scenario requires a message or call application pattern because you can use this knowledge as a consideration when selecting a Product mapping. In the next section we highlight Product mappings that have a more natural fit to the Application pattern message variation or to the Application pattern call variation.
|
| < Day Day Up > |
|
EAN: N/A
Pages: 139