Chapter 12: Flood-based Disruption of Service
| | ||
| | ||
| | ||
Tom: "Hey George, how is our new phone system working?"
George: "Well, it was ok, but it went ape this weekend ."
Tom: "What happened ?"
George: "I don't totally understand it yet, but apparently someone let a virus loose over the weekend. The virus woke up at midnight on Friday. It did something called an INVITE flood, which set up thousands and thousands of 1-900 calls over the weekend. All of our outbound trunks were busy all weekend making $1 a minute 1-900 calls."
Tom: "Holy smoke, how much did that cost us?"
George: "We are still not sure, but way more than I make in a year. We are hoping our service provider will pay it, but it doesn't look promising . I dusted off my resume just in case"
VoIP system administrator after an INVITE flood attack
Overview
In the previous chapter, we covered a form of service disruption where we used malformed packets to disrupt various SIP proxies and phones. In this chapter, we cover additional attacks that disrupt SIP proxies and phones by flooding them with various types of VoIP protocol and session-specific messages. These types of attacks partially or totally disrupt service for a SIP proxy or phone while the attack is under way. Some of the attacks actually cause the target to go out of service, requiring a restart. The attacks described in this chapter are simple to execute and, in many cases, lethal.
Flood-based attacks are effective if the target can be tricked into accepting and processing requests . If enough illicit requests are sent, valid requests from other SIP devices, such as SIP phones, may be lost, ignored, or processed very slowly, resulting in some level of service disruption. Figure 12-1 illustrates this sort of attack.
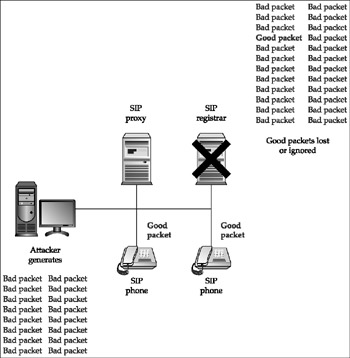
Figure 12-1: Flood-based disruption of service
SIP proxies, SIP phones, and other devices use either UDP or TCP as transport for signaling. UDP is used exclusively for RTP (audio/media). TCP offers more security than does UDP. Unfortunately, UDP is still widely used. Because UDP is a connectionless protocol and lacks sequence numbers or other means of identifying rogue traffic, it is much easier to generate packet floods. Attackers can simply send a flood of packets to a target IP address and port. They may need to spoof the source port, IP address, or MAC address, but this is trivial.
TCP is a connection-oriented protocol where, for example, SIP phones establish persistent connections with their SIP proxies. The packets exchanged as part of a TCP connection use sequence numbers and other means, which make it more difficult to introduce rogue packets. It isn't impossible to do thiswe discussed it in detail in Chapter 6but it is more difficult to generate packet floods effectively.
This chapter describes various flood-based attacks you can perform against SIP proxies, SIP phones, and other devices. We used the same test bed as described for the application-level MITL attacks described in Chapter 6. This test bed included Asterisk and SER SIP proxies, each of which managed several SIP phones. Figure 12-2 illustrates the test bed.
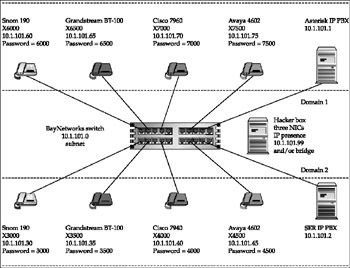
Figure 12-2: SIP test bed
In each attack, we run a rogue application on a PC connected to the SIP network and use it to target various devices. Figure 12-3 illustrates this basic setup.
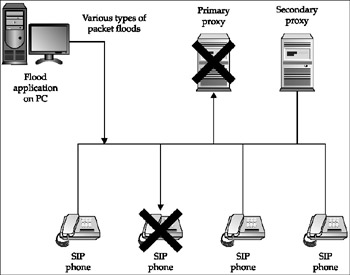
Figure 12-3: Basic setup for fl ood-based attacks
EAN: 2147483647
Pages: 158