Banner Grabbing with Netcat
| | ||
| | ||
| | ||
Banner Grabbing with Netcat
The first step in enumerating a VoIP network involves a technique called banner grabbing or banner scraping . Banner grabbing is simply a method of connecting to a port on a remote target to identify more information about the associated service running on that port. Banner grabbing is one of the easiest and highest yield attack methods that hackers employ to inventory your VoIP applications and hardware. By connecting to most standard services and applications, they can glean the specific service type (for example, Apache HTTPd, Microsoft IIS, and so on), the service version (for example, Apache HTTPd 1.3.37, Microsoft IIS 6.0, and so on), and tons of other useful information about the target.
Banner Grabbing
| Popularity: | 7 |
| Simplicity: | 7 |
| Impact: | 4 |
| Risk Rating: | 6 |
Most manual banner grabbing can be easily accomplished using the command-line tool, Netcat (http://netcat. sourceforge .net/). For instance, building off of the Nmap results from the previous chapter, let's try to identify the web server running on 192.168.1.103:
[root@attacker] nc 192.168.1.103 80 GET / HTTP/1.1 HTTP/1.1 400 Bad Request Date: Sun, 05 Mar 2006 22:15:40 GMT Server: Apache/2.0.46 (CentOS) Content-Length: 309 Connection: close Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>400 Bad Request</title> </head><body> <h1>Bad Request</h1> <p>Your browser sent a request that this server could not understand.<br /> </p> <hr /> <address>Apache/2.0.46 (CentOS) Server at 192.168.1.103 Port 80</address> </body></html>
By examining the error response, we can clearly see that the web server type is Apache HTTPd version 2.0.46 running on the operating system CentOS.
Looking again at the Nmap results from the previous chapter, we see that both UDP and TCP port 5060 is active on host 192.168.1.104. Using the same technique with Netcat, we can manually identify information about the (likely SIP) service attached to that port by sending an OPTIONS method with the following four lines (remember that 192.168.1.120 is the attacking IP address):
[root@attacker]# nc 192.168.1.104 5060 OPTIONS sip:test@192.168.1.104 SIP/2.0 Via: SIP/2.0/TCP 192.168.1.120;branch=4ivBcVj5ZnPYgb To: alice <sip:test@192.168.1.104> Content-Length: 0
SIP/2.0 404 Not Found Via: SIP/2.0/TCP 192.168.1.120;branch=4ivBcVj5ZnPYgb;received=192.168.1.103 To: alice <sip:test@192.168.1.104>;tag=b27e1a1d33761e85846fc98f5f3a7e58.0503 Server: Sip EXpress router (0.9.6 (i386/linux)) Content-Length: 0 Warning: 392 192.168.1.104:5060 "Noisy feedback tells: pid=29801 req_src_ ip=192.168.1.120 req_src_port=32773 in_uri=sip:test@192.168.1.104 out_ uri=sip:test@192.168.1.104 via_cnt==1"
As you can see, we can easily determine the exact SIP application and version by looking at the error response message (SIP EXpress Router 0.9.6 running on Linux).
Why is it important to identify the versions of these particular services? Outdated versions of applications are often vulnerable to exploits that have been published and archived for anyone to view. For instance, looking at http://secunia.com/advisories/8119/ , we read:
Description: IPTel has confirmed vulnerabilities in the SIP (Session Initiation Protocol) implementation in all versions of SIP Express Router up to 0.8.9. The vulnerabilities have been identified in the INVITE message used by two SIP-endpoints during the initial call setup. The impact of successful ex ploitation of the vulnerabilities has not been disclosed but could poten tially result in a compromise of a vulnerable device. Solution: Upgrade to version 0.8.10 and apply patch:
Fortunately ( unfortunately for the attacker) our version of SER is the latest and greatest at version 0.9.6. Similarly, there are many other vulnerabilities published for Apache, Cisco, and most other services and devices we'll be looking at in this chapter. You can find many of them through simple searches on online vulnerability databases:
-
Symantec's SecurityFocus (http://www.securityfocus.com/bid)
-
Secunia (http://www.secunia.com)
-
Open Source Vulnerability Data Base (http://www.osvdb.org)
-
National Vulnerability Database (http://nvd.nist.gov)
Attack Automated Banner Grabbing
Using the previous SIP banner-grabbing example, the tool SiVuS (http://www.vopsecurity.org) can automate this process with a nice graphical interface (see Figure 3-1).
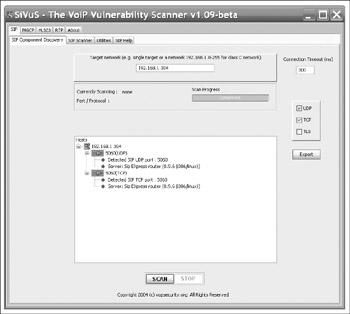
Figure 3-1: SiVuS helps us find the same information we found manually with the click of a button.
Another SIP scanning/fingerprinting tool called smap by Hendrick Scholz (http://www.wormulon.net/files/pub/smap-blackhat.tar.gz) actually analyzes SIP message responses to determine the type of device it's probing. For example,
$ ./smap -o 89.53.17.208/29 smap 0.4.0-cvs <hscholz@raisdorf.net> http://www.wormulon.net/ Host 89.53.17.208:5060: (ICMP OK) SIP timeout Host 89.53.17.209:5060: (ICMP OK) SIP enabled AVM FRITZ!Box Fon Series firmware: 14.03.(8990) (Oct 28 2005) Host 89.53.17.210:5060: (ICMP timeout) SIP timeout Host 89.53.17.211:5060: (ICMP OK) SIP enabled AVM FRITZ!Box Fon Series firmware: 14.03.(8990) (Oct 28 2005) Host 89.53.17.212:5060: (ICMP OK) SIP enabled AVM FRITZ!Box Fon Series firmware: 14.03.(8990) (Oct 28 2005) Host 89.53.17.213:5060: (ICMP timeout) SIP enabled Siemens SX541 (firmware 1.67) Host 89.53.17.214:5060: (ICMP OK) SIP enabled AVM FRITZ!Box Fon Series firmware: 14.03.(8990) (Oct 28 2005) Host 89.53.17.215:5060: (ICMP OK) SIP enabled AVM FRITZ!Box Fon ata 11.03.45 8 hosts scanned, 6 ICMP reachable, 6 SIP enabled $
Many of today's other open-source and commercial vulnerability scanners automate this banner-grabbing functionality along with port scanning, OS identification, service enumeration, and known vulnerability mapping. Just to name a few:
-
Nessus (http://www.nessus.org)
-
Retina (http://www.eeye.com)
-
Saint (http://www.saintcorporation.com/ saint /)
Figures 3-2, 3-3, and 3-4 show a few of these tools being run on our target deployment's Polycom Soundpoint phone (192.168.1.27).
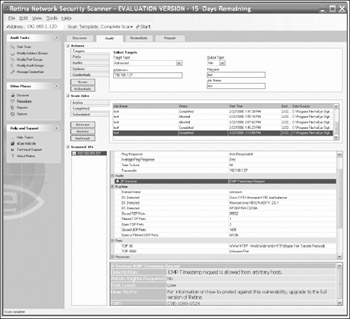
Figure 3-2: The Retina scanner against the Polycom phone
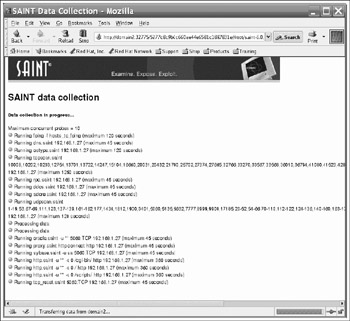
Figure 3-3: The Saint scanner in action against the Polycom phone
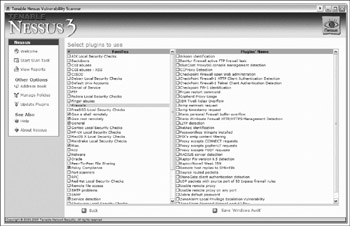
Figure 3-4: Selecting the specific Nessus scanning modules to run against the phone
There is also a commercial VoIP-specific vulnerability scanning tool called VoIPaudit, developed by VoIPshield SYSTEMS (http://www.voipshield.com/). We did not get a chance to run this tool against our test deployment; however, the developers shared with us a screenshot of the tool for your viewing pleasure (see Figure 3-5).
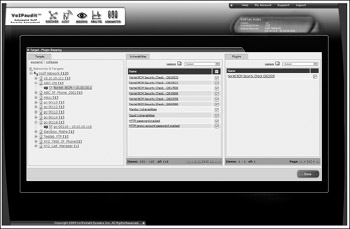
Figure 3-5: Selecting the VoIP exploit plugins to launch
Countermeasurs Banner Grabbing Countermeasures
There's really not much you can do to prevent simple banner grabbing and service identification. Because of the open-source nature of some applications, such as Asterisk or SER or Apache, you can take an extreme approach and hack the source code to change the advertised banners. This is not a long- lasting resolution, however, and will rarely stop a determined hacker who has other techniques at her disposal.
The best solution is to constantly upgrade your applications and services with the latest updates available. Also, you should make sure to disable those services that are not needed in your VoIP environment; for instance, there's probably no good reason to leave telnet services running on your VoIP phone or PBX.
If and whenever possible, restrict access to the remaining administrative services to specific IP addresses. For example, if an administrative web interface to your Asterisk server listens on TCP port 8111, then apply the appropriate firewall or network switch rules to ensure outsiders cannot arbitrarily connect to that port with their browser.
EAN: 2147483647
Pages: 158
- ERP Systems Impact on Organizations
- Context Management of ERP Processes in Virtual Communities
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Healthcare Information: From Administrative to Practice Databases
- A Hybrid Clustering Technique to Improve Patient Data Quality