Protecting a Deployed Network
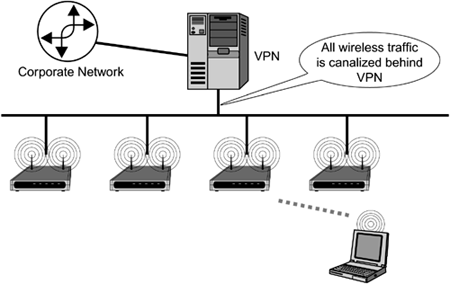
| If you already have a wireless local area network deployed in your organization, you need to take several steps (if you haven't already) to ensure that it is protected. First, apply the design principles discussed in the previous section: Isolate and canalize the traffic. Second, upgrade your equipment's firmware to WPA. Let's look at each of these in turn. Isolate and CanalizeIsolating the traffic from access points may be the most difficult aspect of trying to improve the security of your network, unless you already have your access points on the same LAN segment. Assuming that you haven't already isolated the traffic, you essentially have two choices. The first is to run new cables to your access points, placing them on the same LAN segment without additional enterprise traffic. The second is to use your current switches to create a VLAN (IEEE 802.10) to isolate your wireless equipment. The first choice is not optimal in terms of time and cost, as it requires a great deal of work and expense. The second approach is relatively painless if your equipment already supports VLANs. If it doesn't, you must balance the purchase of new switches with the cost of running new cable (remember our discussion on tradeoffs). A VLAN provides a moderate degree of isolation. However, the isolation is not complete when the switches are attacked via ARP spoofing and other means; see http://ettercap.sourceforge.net. But the protection provided by a VLAN is better than allowing the traffic from access points to co-mingle with traffic from the rest of the organization. Once your traffic is isolated, it is easy to canalize it (see Figure 17.1). And depending on your threat model, you can use a network address translation box, a router, or a firewall on one or multiple entry points into the organization's network. Figure 17.1. Network Architecture with Traffic Canalized
Upgrade Equipment's Firmware to WPAHopefully, your installed base of access points and client cards can all be upgraded to WPA by simply reflashing the firmware on each device and by making some small configuration changes. If that's the case, you should perform that upgrade as soon as possible to support WPA. Once you've upgraded to WPA, you can use WPA in one of two modes: preshared key (PSK) and server-based infrastructure. In PSK mode, you enter a password at each client and each access point and you're done, though you must also update client software from your vendor. While this approach is simple, it doesn't scale well beyond the home or small office. In those cases, you need to deploy an authentication server. Later in this chapter, we discuss what you'll need to do to deploy the infrastructure for supporting both WPA and RSN. Of course, you must check with your equipment vendor for details on upgrading the firmware and client software. What to Do If You Can't Do AnythingThe steps we've outlined involve a great deal of work and probably require you to spend money to improve things. What do you do if you can't make any of these suggested changes? The first and most important question you must answer is, "What is the utility of using wireless versus not using it?" Does it add value to your business? In addition, you have to consider the value of the information on your network. What can someone do (or get) if they break into your network? Finally, you have to consider the threat against your network. Is there a reason for someone to try and break into your network? If you do that analysis, and you decide (and only you can make that decision) to keep using your wireless network, here are some steps that you can follow to mitigate the risks to your network. Our goals in providing this information are to help you protect yourself as best you can. Remember, however, that your network and all of the information on it will be vulnerable, and our recommendation is that you make the investment in time and equipment to get it right rather than relying solely on these pointers. The whole idea is to make it as difficult as possible for someone to break into your network.
|
EAN: 2147483647
Pages: 151