Section 10: Security (10 Points)
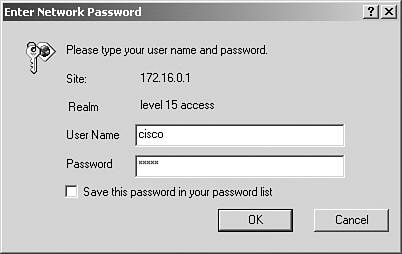
You can manage a router via http as the command ip http server is enabled by default; to add local password access, use the command ip http authentication local, and then configure a username and password on the router both to cisco. Figure 3-15 shows the Password screen when attempting to access R3 by HTTP. If you configured this correctly as shown in Example 3-92, you have scored 2 points. Example 3-92. 1R3 HTTP Accessusername cisco password 0 cisco ! ip http authentication local Figure 3-15. R3 HTTP Access
You need to configure an access list to block port 135, 139, and 445 on R2 FastEthernet0/0. Because you have not been told if this is TCP or UDP, you must block both. To provide the detailed information, you are required to enable logging and use the log-input command at the end of your access list. Doing so will provide both MAC and IP address details of any device that matches the list on VLAN2. If an IP address is targeted that does not exist, the router will send an ICMP unreachable message, which will increase CPU resource activity. To stop this, you are required to configure no ip unreachables under interface FastEthernet0/0. Although you have only been requested to block the virus from entering your network, it is good practice to also stop it from leaving your network so you are not responsible for spreading the virus if your network does become infected. If you have configured this correctly as shown in Example 3-93, you have scored 3 points. If you have only configured the ACL inbound on R2 and not also outbound, you have only scored 2 points. Example 3-93. R2 Virus Protection Configurationlogging buffered ! interface FastEthernet0/0 ip address 172.16.0.1 255.255.0.0 ip access-group 115 in ip access-group 115 out no ip unreachables ! access-list 115 deny tcp any any eq 135 log-input access-list 115 deny udp any any eq 135 log-input access-list 115 deny tcp any any eq 139 log-input access-list 115 deny udp any any eq 139 log-input access-list 115 deny tcp any any eq 445 log-input access-list 115 deny udp any any eq 445 log-input access-list 115 permit ip any any |
EAN: 2147483647
Pages: 268