Addressing
Addressing is one of the important components of a network layer protocol. IPv4 identifies each host[4] by a 32-bit address. This address is normally represented in the form A.B.C.D. This notation is commonly referred to as dotted decimal notation where each symbol is a byte (8 bits). An example of an IPv4 address is 128.127.126.125. This representation is chosen instead of a flat number space because it imparts hierarchy to addressing and also is easier to perceive.
[4] A host is an entity that is involved in the communication.
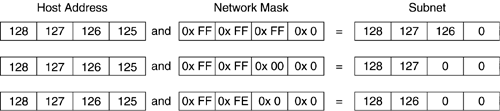
An IP address has two parts a network ID and a host ID. The network ID logically groups a set of IP addresses together. The grouping is required to provide efficient routing and other services, such as IP broadcast.[5] The network ID part of an IP address is obtained by logical AND of the IP address with the network mask. The network mask is always a contiguous bit of 1s. Examples of network masks are 255.255.255.0, 255.255.0.0, and 255.254.0.0. In these examples the leftmost (starting from the most significant bit) 24, 16, and 15 bits are 1's respectively. The network ID for the IP address 128.127.126.125 with the example network masks is 128.127.126, 128.127, and 128.126 respectively. This is obtained by logical AND of the network masks with the IP address as shown in Figure 2.4. An IP address is always represented along with its network mask.There are two representations: 128.127.126.125/255.255.255.0 or 128.127.126.125/24. Both representations have the same meaning, i.e., the network ID are 24 most-significant bits of the IP address.
[5] Broadcast is the ability to communicate with a set of hosts without duplicating the packets. In this case, the network ID part of the destination address is used to identify the destination and hence all nodes with the same network ID get the packet.
Figure 2.4. Relationship between subnets and network masks.
To realize the importance of network mask, let us consider an analogy of how telephone numbers are allocated and maintained. The telephone numbers in the United States have a well-known structure (xxx)-yyy-zzzz where xxx represents the area code, yyy represents the city code, and zzzz identifies the line within that city. It is important to provide the structure for the purposes of routing and telephone number allocation. Imagine what would happen if there was no such structure. How will one know if a number is already allocated or not? Moreover, if someone wants to call a number from California, how does the switch in California know how to reach all the telephones in the U.S., which is 1010! IP address allocation is no different. It allows logical grouping of addresses to ease the task of address allocation, routing, and providing other services.
An organization that gets a network ID can define subnets recursively. Let us go back to the telephone address allocation. For the purpose of illustration, let us say that the top 3 digits (xxx) are allocated to a state. It is up to the state to use the lower 7 bits. The state uses 3 out of the 7 digits to identify the town. The town uses 4 digits that are left to identify the telephone of a particular house. In this case, there is a three-level address allocation state, city, and house. Network address allocation is no different. An organization that gets a chunk of network addresses would like to allocate it to make its routing and traffic separation easy. Various departments may like to have addresses in the same range as they may want to keep some traffic local to their network. For example, if an organization receives a network ID 132.131/255.255, it can use some bits to form its own subnets. Let us say that it uses 8 of the 16 bits to form its own subnet. Then the network mask within the organization is 255.255.255.0. However, this is oblivious to the outside world. For the outside world, the network mask for the organization is still 255.255.0.0.
You may be wondering why it is necessary to define subnets. The following are the advantages of defining subnets:
The routing table size in the Internet core decreases because it is unnecessary to specify each host in an organization. A router can be delegated the task of forwarding a packet originating or destined to any host on the subnet. Normally, at least one router is assigned for each subnet.
Subnets are used to contain some types of IP traffic, such as IP broadcasts. There are packets that are sent to all the hosts on a subnet. If an organization has a network ID 125.126, a broadcast packet would be sent to all the 65,000 hosts! If subnets are used, these packets are restricted just to the subnet.
IP supports three kinds of addresses unicast, multicast, and anycast. Unicast addressing is where an IP address is uniquely a host. Any IP address in the range 1.0.0.1 to 223.255.255.255 represents a unicast address. Address range 224.0.0.0 to 239.255.255.255 represents a multicast address and address range 240.0.0.0 to 247.255.255.255 represents an anycast address, and 248.0.0.0 to 255.255.255.255 is reserved for future use. Anycast address is still a research topic, and is not covered in this book.
As there are 32 bits in an IPv4 address, one can address up to 232 hosts[6]! One would imagine that this should be more than sufficient to address hosts in the Internet. However, the Internet is running out of address spaces and this has led to the design of IPv6.
[6] In reality, the number of addressable hosts is less than this number because some addresses are reserved.
IPv4 Header
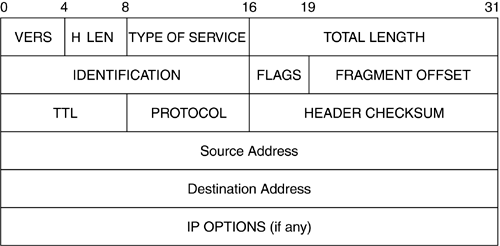
The IPv4 header is shown in Figure 2.5
Figure 2.5. IPv4 header.
The usage of various fields is described below.[7]
[7] We describe in detail only those fields that are used by IPSec. For example, the options field is not discussed in detail.
Version field: This 4-bit field is used to indicate the version. This value is 4 for IPv4. The version field is normally used for backward compatibility. When new versions are defined, they may be required to interoperate with the legacy systems.
Header length: The header length indicates the length of the header in 32 bits (4 bytes). This limits the maximum length of the IPv4 header to 60 bytes. This is one of the limitations of IPv4 that led to the development of a newer version of IP discussed in the next section.
Type Of Service (TOS): TOS is used to indicate the traffic requirements of the packet. This field is currently under review at the IETF.
Length: The length of the datagram in bytes (including the header) in the network byte order.[8] THIS FIELD INDICATES THE SIZE OF THE DATAGRAM TO THE NETWORK LAYER AT THE RECEIVING END.
[8] In the rest of the book, the network byte order is assumed. There are two types of representation of integers big endian and little endian. In big endian, the most significant byte of an integer is in the most significant byte (Motorola chips use big endian). In little endian, the most significant byte of an integer is in the least significant byte (Intel). Network byte order corresponds to big endian.
Identification: The 16-bit identification field is used to uniquely identify an IP datagram. The term IP datagram refers to the transport payload plus IP header, and is used in the context of end hosts. The identification field is used mostly in the context of fragmentation that is described later. The identification field is used to uniquely identify which IP packets belong to an IP datagram.
Flags: Only 2 out of the 3 bits in the flag are defined. The first bit is used to specify not to fragment the IP packet. When this is set, a router sends back a control message to the host indicating its MTU (Maximum Transfer Unit). This bit is used in Path MTU. This is a process by which the end host discovers what size the IP packets it generates should be so that the packets do not get fragmented en route to the destination. This is necessary because fragmentation is detrimental to the operation of the network. The transport layer has to send the entire datagram if a fragment is lost. The second bit is used to indicate if the packet is the last fragment of a fragmented datagram or if there are more to follow. This bit is used in reassembling fragmented packets.
Fragmentation offset: This field indicates the offset of the IP packet in the IP datagram. The utility of this field is discussed in the fragmentation section.
Time To Live (TTL): This field is used to avoid packet looping and also to administratively scope the transmission of a packet. The host sets this field to a certain default value and each router along the path decrements this field by 1. If a router sees a packet with a TTL of 1, it drops the packet. This is crucial in case of routing loops as the packet will be roaming in the network forever if nobody drops it.
Protocol: This 8-bit field is used to indicate the transport protocol carried by this IP packet. This field is used by the end host to demultiplex the packet among various transport protocols.
Checksum: The checksum is calculated on the IP header and is used to guarantee the integrity of the IP header. The checksum is not a cryptographic checksum and can be easily forged.
Source address: This 32-bit field indicates the IP address of the source that generated this packet.
Destination address: This 32-bit field indicates the IP address of the destination host.
Options: An IP header can optionally carry additional information. As options are not important in understanding IP security, they are not discussed in this book.
IPv6
IPv4 limits the address space to 32 bits. To avoid the address crunch, the IETF started working on the next version of IP and called it IPv6. One of the main advantages of IPv6 is that it increased the address space from 32 bits to 128 bits (16 bytes).
Other modifications include:
No fragmentation support for transit packets in routers. The end hosts are required to perform PMTU now.
Richer options support. The options are treated as separate headers instead of being part of the IP header. This is called header chaining and is more flexible. In this case, the IP extension headers (options) are inserted between the IP header and the transport layer header.
Conceptually, both the address and subneting of IPv6 are similar to that of IPv4. IPv6 address is 128 bits long and their representation is different. Instead of the dotted decimal notation used in IPv4, IPv6 uses a different notation hexadecimal numbers separated by colons:
0123:4567:89AB:CDEF:0123:4567:89ab:cdef
There are a number of variations to compress the address. The reader is encouraged to refer to IPv6 addressing architecture IETF documents for a more detailed discussion.
The concept of network mask and subnet in IPv6 is similar to what exists in IPv4. IPv6 implements a much richer hierarchy for addressing to ease the problem of routing and addressing.
IPv6 Header
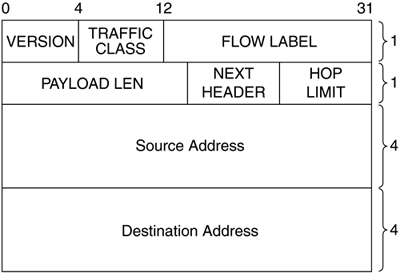
The IPv6 header is shown in Figure 2.6.
Figure 2.6. IPv6 header.
The usage of various fields is described below.
Version: This 4-bit field indicates the version. For IPv6 this value is 6.
Traffic Class: This 8-bit field is used to indicate the traffic requirements of the packet and is similar to the TOS field in the IPv4 header.
Flow Label: This 20-bit field is still experimental and it is still not clear how this will be used in the future. One possible usage is to identify a flow that requires special processing by the routers.
Payload Length: This 16-bit field indicates the length of the payload excluding the IPv6 header.
Next Header: This 8-bit field is similar to the next protocol field in IPv4 header, the only difference being that the option header may appear in this field unlike IPv4.
Hop Limit: This 8-bit field is the same as TTL field in the IPv4 header.
Source and Destination Address: These 128-bit fields represent the source and destination IPv6 addresses respectively.
Extension Headers
As mentioned before, IPv6 defines option headers to provide the capabilities that IPv4 option fields provide. These are called extensions. The option extensions are inserted between the IPv6 header and the transport header as shown in Figure 2.7.
Figure 2.7. IPv6 header with options.
![]()
Each option header is assigned a unique protocol ID and is encoded using the same format as shown in Figure 2.8.
Figure 2.8. IPv6 options format.
![]()
There are two kinds of options hop by hop and destination-based. Hop-by-hop options can change along the path and are normally included immediately following the IPv6 header. Destination-based options do not change along the path and are inserted after the hop-by-hop options.
Fragmentation
Fragmentation is the process whereby an IP packet is fragmented into multiple IP packets at the source or in a router. After fragmentation, each packet is transmitted independently and is reassembled at the destination. The question that immediately comes to mind is: Why should we fragment IP packets?
The IP layer accepts any transport layer payloads. The transport layer payloads can be of any size (restricted only by the buffer limitations on the system). The IP layer does not have the ability to restrict the data that is passed to it from the upper layers. However, as the network layer (IP) has to transmit the packet over a physical interface, there are limitations with respect to the size of the packet it can transmit. These limitations arise because of the physical limitations of the medium over which a packet is transmitted. For example, over Ethernet the maximum size of the packet cannot exceed 1518 bytes. If the IP layer's transport payload is more than 1480 bytes (assuming there are no options), it has to fragment the packet before it is transmitted. Otherwise, the length of the packet will exceed 1518 bytes 1480 + 20 bytes for IP header + 14 bytes for Ethernet layer header + 4 bytes of CRC used for detecting errors.
The network layer packets can also be fragmented in any router where there is a mismatch in the maximum length of the packets between two physical layers. For example, the incoming interface can be a token ring that has a maximum packet size of 4096 and the outgoing interface can be Ethernet that has a maximum packet size of 1518. If the IP packet coming in on the token ring is greater than 1500 bytes, the router has to fragment the packets even though it did not generate the packet.
On the destination, the IP layer has to reassemble all the fragmented packets before it passes the payload to the transport layer. Referring to Figure 2.3, the transport layer on the destination should see the same information that was passed from the transport layer down to the network layer on the source. Hence, it is up to the IP layer to reassemble all the fragmented packets, construct the transport payload, and pass it up to the transport layer.
The IP layer achieves this process of fragmentation and reassembly by using the flags, length, and fragmentation offset fields in the IP header.
Fragmenting a packet is considered detrimental to the operation of the network. This is because, even if one packet is lost, the transport payload has to be retransmitted by the reliable transport layer as the IP layer does not cache packets. The IP layer avoids fragmentation by monitoring the MTU along the path from the source to the destination. This process is called Path MTU discovery or PMTU. After the IP layer discovers the PMTU, it never sends a packet that exceeds the PMTU.
ICMP
ICMP (Internet Control Message Protocol) is used to ensure the proper operation of the network and for debugging. The protocol runs on top of a network protocol such as IPv4 or IPv6.
ICMP messages are generated both by hosts and routers to monitor the network and to ensure proper operation of the network. For example, if a router does not have a route to a particular network, it sends an ICMP message back to the host indicating the network is unreachable. If the router drops the packet without any indication, monitoring the network becomes a nightmare. ICMP is used to determine if a host is reachable or not. ICMP is used in PMTU discovery. If a router needs to fragment a packet but the do not fragment bit is set, then the router sends back an ICMP message to host indicating the MTU of its link so that the host can generate packets whose size does not exceed this MTU.
Multicast
IP also provides the ability to send a packet to multiple hosts anywhere on the Internet. This is a special case of broadcasting where only interested hosts receive a packet. Consider the example of pay-per-view broadcast. If a cable company intends to telecast a program over the Internet to all its subscribers, it has three options:
Telecast individually to each subscriber. This process has a very high overhead as the same data is duplicated to all the subscribers. It has lot of undesired side effects. It increases the Internet traffic substantially and also increases tremendously the load on the server that is distributing data.
Telecast by sending a broadcast to the whole Internet. This process is unacceptable because even nonsubscribers get to see the pay-per-view program. Moreover, Internet-level broadcast is very bad.
Telecast only to subscribers by using a technique called multicast. Multicast is an intelligent packet distribution mechanism where only subscribers get the packet. The data is distributed on only those links with subscribers. The traffic is delivered only to those nodes that have subscribed to the traffic.
Multicast packets have the same format as unicast IP packets. However, the destination field in the IP header has a multicast address and not a unicast address. The obvious question that comes to mind is, How do you know where to send the packet if you cannot uniquely identify a host? That is the beauty of multicast. There is support from the routing layer that has the knowledge of the hosts that are listening on a particular multicast address. A detailed discussion of multicast is out of the scope of this book. In fact, multicast discussion is a whole topic in itself.
Transport Layer
The TCP/IP protocol suite implements two protocols at the transport layer Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP is a connection-oriented protocol ensuring ordered and guaranteed delivery of packets. It has mechanisms built into it to provide these services to the application layer. In addition, TCP also implements mechanisms such as flow control, that ensures that the destination is not bombarded with packets. UDP is a connectionless protocol that does not ensure either guaranteed or ordered delivery of the packets nor does it ensure flow control. The choice of using TCP or UDP is entirely up to the application.
Although we will not discuss the TCP and UDP headers in detail, we will briefly discuss two fields that are present in both the headers the source port and the destination port. These two fields are critical in identifying how to process the data once the destination receives it.
The TCP/IP protocol suite identifies the application a packet is destined to by a five tuple: <source address, destination address, source port, destination port, protocol>. This tuple must be unique for each application running on a host. We have already discussed the source and destination address fields. These fields are set in the network header. The source and destination ports are 16-bit fields set in the transport header. The source port is allocated by the source host and the destination is allocated by the destination host. For an application to communicate with another application on another host, it needs to know three things the address of the destination, the port number on which the application is running, and the protocol over which to communicate. For example, most Web servers are listening on port 80 and use TCP protocol. An application binds to the source and destination port and also specifies the transport protocol to use for the transmission. The transport protocol uses this tuple to identify the application that receives the data.
| Top
IPSec (2nd Edition) ISBN: 013046189X
EAN: 2147483647 Year: 2004
Pages: 76 Authors: Naganand Doraswamy, Dan Harkins
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |