Groups
Creating groups also requires planning. Groups are objects that enable a number of users to be administered as a single account. Whereas users are created to identify individuals on the network, groups are created for the purpose of assigning permissions for a particular task or role. Users can be given permissions to resources directly, but this is not recommended; groups are the standard mechanism for granting access. Therefore, you will want to create a number of groups, some of which may even have only one member!
| Tip | Creating a group of one may seem like a lot of unnecessary work, but this process has a number of advantages over simply giving that user permissions to resources directly. For instance, if the user who performs backups goes on vacation, you can simply put the user who is covering for that person into the backup group temporarily. If you did not have a group, you would have to assign the temporary backup user rights and permissions equal to the original backup user. This would take time and be confusing to administer. Once again, plan early and avoid trouble later! |
local groups
Groups that are created on Windows NT workstations and Windows NT servers and allow for local administration of resources. Global groups or domain users could be placed into these groups to give them permissions on the NT machine.
global groups
Groups that hold users in the domain and that are placed into local groups. Global groups are primarily used to group users with similar network roles.
Types of Groups
Windows NT 4 featured two types of groups: local groups and global groups. Windows 2000/Server 2003 expands on this, allowing four types of groups: global, domain local, universal, and local. Each of these has a particular scope (area of use), and Windows 2000 is stocked by default with a number of built-in groups of each type.
In general, the use of groups in Windows 2000 and Server 2003 is similar to the use of groups in Windows NT domains, and indeed many of the built-in groups listed in this section are identical to Windows NT 4 groups. A user is created and placed into one or more global groups based on their job function. These global groups are then placed into domain local groups, and the domain local groups are given permissions to resources.
If you are looking for a process to remember this by, Microsoft has two acronyms it recommends:
AGLP This stands for Accounts into Global groups, into Local groups, which are given Permissions to resources.
UGLR Users are placed into Global groups, which are placed into Local groups, which are given permissions to Resources.
| Tip | Neither of the “official” acronyms is especially catchy, and you might find this works better: Remember that setting permissions is one of the U-G-L-ie -R tasks you will need to perform! |
Besides the standard built-in groups, there are also five other default System Groups that are not based on who the user is, but on how they are connected to a resource. These are the Everyone, Authenticated Users, Creator Owner, Network, and Interactive groups. The Interactive group, for instance, includes only those users who are logged on locally to a machine. If the same user accesses a share across the network, they are considered to be in the Network group. These last five groups cannot be configured through the Active Directory Users and Computers tool, but they can be used while setting permissions on resources.
Global Group
Only users from the domain in which the global group is created can be added to this group, but the group can be used to access resources in any domain in the forest. Global groups are generally used to organize users with similar roles in the organization. One user may be in a number of global groups.
| Built-in Global Group | Description |
|---|---|
| Domain Users | Includes all users created in the domain. |
| Domain Admins | Accounts added to this group gain full administrative power of the domain. |
| Domain Guests | The only default member in this group is the Guest user, which is disabled by default. Users can be added to this group to allow them temporary, low-level access to the network. |
| Enterprise Admins | Administrators on the domain who need to administer other domains in the forest as well can be added to this group, which must then be given rights in the other domains (usually by being added to the domain local Administrators group in those domains). |
Domain Local Group
This group allows users and global groups from any domain in the forest to be members, but can be used to access resources only within the domain in which the users or groups are created. These groups are generally used to identify resources that have a similar function on the network.
| Built-in Domain Local Group | Description |
|---|---|
| Account Operators | Allows members to create and configure user and group information, but not network resources. |
| Server Operators | Allows members to create, configure, and delete network resources such as printers, files, and shares. Members can also set permissions on these resources, but cannot create or modify users or groups. |
| Administrators | The Domain Admins global group is placed into this group, and it is this Administrators domain local group that wields power on the domain. Members can add users and groups as well as create and configure resources. |
| Guests | The Guests global group is a member. Any permissions granted to Guests will be available to all Guest users (if Guest is enabled). |
| Backup Operators | Allows members to perform backup and restore procedures. |
| Users | Contains the Domain Users global group and, by extension, all users on the domain. |
Universal Group
Users, local groups, and global groups from any domain in the forest can be members of this group, and they can be given permissions to resources in any domain. This group is generally used only in large multidomain networks. There are no built-in universal groups.
Local Group
The local group is used to assign permissions only to resources that are on the machine that the group was created on. These groups are available on Windows 2000 Professional/XP Professional workstations and on Windows 2000/ Server 2003 servers that do not have Active Directory installed on them. For the most part, they mirror the domain groups they are named for, but their scope does not extend past the machine they are created on.
| Built-in Local Group | Description |
|---|---|
| Administrators | Allows full access to all machine configuration and resources |
| Power Users | Allows users to install software and hardware, and do some admin tasks |
| Backup Operators | Allows access to file resources for backup |
| Users | Includes accounts that need non-admin access to the machine |
| Guests | Can be used to grant low-level guest access to the machine |
Power Users
Intended to allow Windows 2000 Professional or XP Professional users greater authority over their workstations. Power Users are not as powerful as the Administrator, but can do far more than just Users, in that they can install software and configure more workstation options.
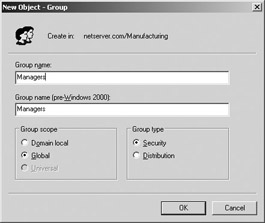
Creating a Group
Although the built-in groups can help get you started, you will likely want to create groups of your own. Creating a group is relatively straightforward. Within the Active Directory Users and Computers tool, select a container for the new group and create the group by using the New Object–Group window shown here. After you have created a group, you can add users to it as they are created. You can also add users from the group’s Properties window later.
Configuring a Group
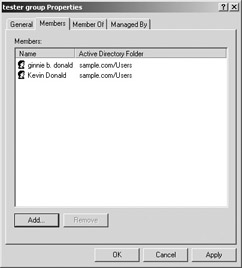
After you have created a group, you can configure a number of elements concerning that group, including adding users to the group. To do this, right-click the group in Active Directory Users and Computers and select Properties. Using the Members tab, you can select users and add them to the list of members. You can also add the group to other groups, select a manager for the group, and add other information regarding the group object.
Organizing permissions in groups is easier than organizing them on an individual basis. Here are two other reasons for getting used to using groups:
-
If you create a network by using standard Microsoft techniques (remember A-G-L-P?), another administrator who knows the same techniques can easily manage the network when you go on vacation—or when you take a more lucrative position elsewhere!
-
Microsoft MCSA/MCSE tests expect you to assign permissions the “right” way, meaning the Microsoft way.
|
|