How Antivirus Works
| Antivirus programs work by searching computer data for viruses and malicious software code (which includes viruses, worms, and Trojan horses) and then removing the infections they find. Several elements of any antivirus software are important to understand:
These concepts are discussed in more detail in the rest of this chapter. Virus DetectionJust about every antivirus program on the market today works by recognizing the so-called signature inherent in all viruses. In this case, a signature refers to the unique sets of bit arrangements within the virus code. Antivirus software programs contain thousands of signatures. Figure 3-4 shows how the virus-detection process works. As new e-mail and data arrive at a computer, the antivirus software checks the new information against its list of known virus signatures. Figure 3-4. Virus Detection Using Known Virus Signatures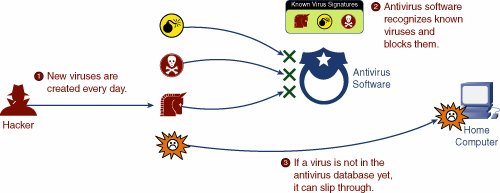 These programs run in the background and do not generally affect the performance of your computer unless you have very processor-intensive programs running (such as high-end games or a computer-assisted design [CAD] program). When a match is found, an additional detailed comparison is made against the actual virus program to protect against false positives. If that comparison is positive, the e-mail or download is blocked, and the data is flagged for removal from your computer. When a new virus is discovered, teams of engineers at the antivirus software companies begin working to identify the unique signature. After the signature is identified and distributed to everyone who purchased the antivirus software program, the program adds the signature to the list of what it looks for during the scanning process. During the interim period between a new virus release and the discovery and distribution of the new signature for that virus, antivirus programs do not have the signature necessary to detect the virus. How to block these "time-zero" viruses is the focus of much work right now. Virus PreventionOne of the biggest problems today is that an Internet virus or worm can travel around the Internet faster than news about the virus or worm. So, even if the antivirus people start working on finding the signature as soon as the virus launches, by the time they find and distribute the signature, the virus could have gone around the world. In most cases, this is exactly what happens. Therefore, the antivirus people are under pressure to protect their customers from being affected by worms and viruses before a "cure" is found. Their answer to this is heuristic detection. Heuristic detection looks at behavior patterns of files and executables on your machine. If a program launches and starts behaving oddly or in a virus/wormlike way, the program is flagged, and the user is notified. Figure 3-5 shows an example. Suppose the virus that escaped detection in Figure 3-4 earlier now starts executing. It searches the Outlook Express address book on your computer and attempts to start mass e-mailing itself to everyone on your contact list. Figure 3-5. Virus Prevention Using Heuristics It is possible that if heuristic detection is enabled, the antivirus program might recognize the behavior of the program as viruslike, and halt or quarantine it until further notice. Unlike signature-based detection, heuristic detection will also notice and flag remote-control behavior and keystroke loggers, offering protection against the most common Trojan horse attacks. Although heuristic detection greatly improves your time-zero (the early moments of a virus or worm explosion) defense, there are some limitations:
Even with these limitations, however, behavior-based protection software is worth enabling and recommended. Heuristics are included in most of the major antivirus software programs, including those from McAfee, Symantec, Trend Micro, and Zone Labs. |
EAN: 2147483647
Pages: 130