How Firewalls Work
| Firewalls can protect your home network by monitoring your broadband Internet connection and only permitting legitimate traffic (the data packets coming in and out of your network) to reach its destination. Firewalls come in two basic types: stateful packet inspection (SPI) firewalls and personal software firewalls (sometimes referred to as packet-filtering firewalls). The following two sections discuss and compare the different types. Stateful Packet Inspection FirewallsLet's examine what an SPI firewall is. Packets are messages containing pieces of data used to communicate between your computers or with the Internet. Inspecting those packets means we look at each one and check whether it is a legitimate message. Stateful means that not only are we going to check each message itself, but check that the message is sent or received at the right time in the conversation. For example, suppose two people, Sally and Rick, are talking and the conversation goes something like this:
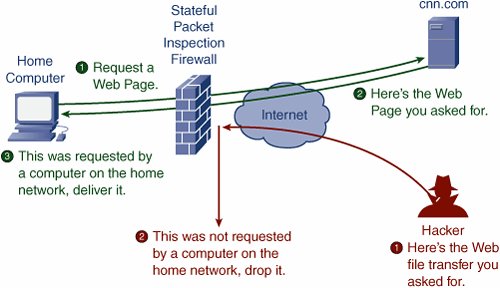
What can we learn? Well, after Rick asks, "'sup girl?" the first time, we expected Sally to say something witty, such as, "The sky and your cholesterol." Instead, she repeats, "Hi Rick." That sounds fishy because it is not what we expected Sally to say at that point in the conversation. Even fishier is she repeats it a third time. So we can conclude either that Sally has been taken over by an alien or replaced by a robot. Either way, we are probably done talking to her and politely smile as we walk away. SPI works in a similar way. Figure 1-3 shows an example of an SPI firewall on a broadband Internet connection. Figure 1-3. How SPI Firewalls Work
As shown in the green series of events in Figure 1-3, as a computer on the home network originates a request for a web page, the SPI firewall inspects the request as it passes and makes note of the request. Next, when the website responds with the web page, the SPI firewall inspects the response. It looks in its memory and realizes that, yes, this web page response was because of the computer on the home network asking for it, and the SPI firewall allows the web page through to the home network. If a hacker or some other computer attempts to send a message to a computer in the home network, such as in the red series of events in Figure 1-3, the SPI firewall inspects the message again. This time, however, the firewall cannot make the connection between the message and a request from the home network because such a request did not occur. So, the firewall blocks the message. Pretty neat. SPI firewalls are an effective way to keep out unwanted intrusions into your home network. They do not solve everything; after all, hackers are crafty and figure out ways around just about everything. However, SPI firewalls can at least dramatically increase the level of protection you have to start with. If only we had SPI firewalls for our phone lines to keep telemarketers from calling us unless we called them first. Personal Software FirewallsPersonal software firewalls have a slightly different role in your home network security. Whereas SPI firewalls are usually meant as a barrier to what can come from the Internet, personal software firewalls act as a barrier to what can go to the Internet from your computers. Figure 1-4 shows an example of a personal software firewall. A web browser, such as Internet Explorer, attempts to send a web page request to the Internet. The personal software firewall is set up to allow access for this program, so the request is allowed, and the web page is retrieved. Figure 1-4. How Personal Software Firewalls Work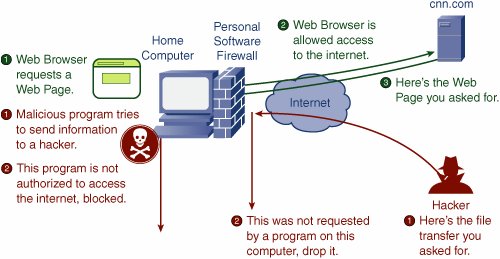 Suppose, however, that despite your best attempts, your computer becomes infected with a Trojan horse virus program (see Chapter 3, "Tip 3: Use Antivirus Protection," for more information on viruses). Now the little devil attempts to send information back to the hackers who planted it, as depicted in Figure 1-4. This time, however, the personal software firewall intercepts the access attempt because that program is not set up to be permitted access to the Internet. The request is denied, and the hacker does not receive the information from your computer. Just to confuse things a little, many personal software firewall programs also contain an SPI firewall for both outbound and inbound protection, as depicted in the lower right of Figure 1-4. Sweet. |
EAN: 2147483647
Pages: 130