Implementing Additional Password Security Options
Protecting your user accounts with strong passwords is critical. As you've now learned, however, any person with physical access to your computer can potentially bypass even the most complex logon passwords using any one of a number of password cracking or recovery utilities.
To use these various tools, a person not only needs physical access to your computer, but also the capability to start your system with a bootable CD or floppy disk. Unfortunately (from a security perspective), the default BIOS settings on most computers are configured so that your system will first attempt to boot from a floppy disk, then a bootable CD, and finally your hard drive. What this means is that any user with the right tools who inserts a bootable disk can potentially get past any of the Windows Vista security settings you've implemented.
Thankfully, all is not lost. Although the current BIOS settings on your computer may allow the system to be booted from a floppy disk or CD, you can change these settings. Furthermore, you can protect your computer with different BIOS passwords to restrict BIOS configuration changes. The following section explores the different passwords that can be implemented to control what users can do when they have physical access to your Windows Vista system.
BIOS Passwords
When you first start your computer, an on-screen message appears giving the key (or key combination) that must be pressed to access your system's BIOS configuration settings. Usually something like F1, F2, or the Delete key, it differs depending on the make and model of your computer, as well as the type of BIOS that is installed. You may be prompted with a message that tells you to "press this key to enter the BIOS, System Setup," System Configuration Settings, or similar.
| Tip | If you're having trouble accessing or configuring your computer's BIOS settings, Wim's BIOS Page (http://www.wimsbios.com) is an excellent reference site. |
Your computer's BIOS won't be secured in any way by default, and that's potentially dangerous if you're worried about someone making configuration changes to your PC. In fact, if left unprotected, a user could seriously damage your system or render it virtually unusable by changing BIOS settings alone. Worse yet, he could implement BIOS passwords before you do, locking you out of your own system.
Although their names may differ slightly depending on the manufacturer, almost every BIOS can be protected by two different passwords:
-
A supervisor password, which must be entered to change BIOS configuration settings.
-
A user password, which must always be entered before the computer launches into any main boot process.
Figure 3-9 shows the BIOS Password configuration screen for a computer with a common Phoenix BIOS.
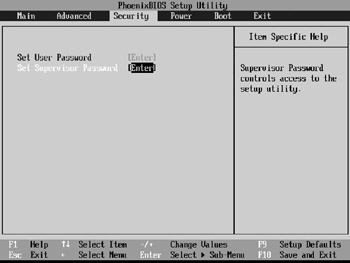
Figure 3-9: BIOS Security configuration screen.
The exact steps to configure user and administrator passwords for a BIOS differ by manufacturer, but are generally similar to the following:
-
Reboot your computer. Watch for the on-screen message that lists the key you need to press to enter the BIOS. Press that key when the message appears - if it passes you by and the Windows Vista boot process begins, reboot and try again.
-
When the BIOS configuration screen appears, look for a section marked Passwords or Security. Once found, enter a password for Supervisor access.
-
Next, enter a User password if that's your preference. If you do enter a User password, keep in mind that any user attempting to start your computer will need to know and supply this password to boot into Windows Vista.
-
Even with a User password in place, the default BIOS configuration will allow any user who knows the password to boot from a floppy disk or CD. If you're concerned about this, look for a section in your BIOS marked Boot or Main. You should find settings that enable you to configure the order in which your computer will attempt to boot, usually something along the lines of A:, D:, C: - meaning your floppy drive first, CD drive second, hard disk third). You can usually change the order of this list to make your hard drive the first boot device in the list, or even remove the other options completely.
-
Press the appropriate key sequence to save your new BIOS settings (usually Esc, then Y for yes).
| Caution | If you do opt to configure BIOS passwords, it's imperative that you remember them or your PC could be rendered unable to boot. If necessary, write these passwords down and store them in a safe place. |
If you lose or misplace BIOS configuration passwords and cannot boot your system or change BIOS settings, there may still be hope. Many BIOS manufacturers configure backdoor passwords that can be used to access and change configuration settings should the need arise. Some PC vendors (such as Dell) can also help you reset the BIOS password for your computer if you call their technical support line and can provide the necessary details about your system. Utilities that claim to be able to crack BIOS passwords can also be found on the Internet.
Although it depends on the specific BIOS used, BIOS passwords can also sometimes be circumvented or erased by removing and then replacing a computer's CMOS battery, or by shorting the jumper pins on the motherboard that control CMOS memory. Of course, you should not rely on either of these methods as an alterative to remembering your password. Furthermore, attempting such changes might result in physical damage to your PC.
Hard Disk Passwords
In addition to BIOS passwords, many laptops include a feature that allows you to configure a hard drive password. Although fundamentally similar to a BIOS User password, it's actually more complex. When a hard drive password is configured, a user cannot boot from or access the drive without that password. Even if the hard drive is physically removed from the laptop and installed in another computer, the password is still required for access - erasing CMOS memory or other BIOS-like techniques cannot circumvent it.
Although a hard drive password certainly appears to be a secure way to protect your computer, proceed with caution. If you forget this password your only real option is to replace the drive, or employ the services of a dedicated (and potentially expensive) hard disk recovery service in an attempt to crack or reset the password.
However, if your laptop's hard drive includes extremely sensitive information that you cannot risk another user gaining access to, you may want to consider configuring this option. If your system includes the capability to configure a hard drive password, the setting is usually configured from the same BIOS screen as User and Supervisor passwords.
Syskey Password
As you learned earlier in this chapter, the Windows Vista SAM database stores hashed copies of user account passwords, and encrypts the database for extra protection. By default, the system key (also known as the startup key) used to encrypt the database is also stored on the computer. As an added security feature, you can export this key to a floppy disk that must be inserted each and every time you attempt to boot Windows Vista. Alternatively, you can leave the startup key on the hard disk, and assign it a password that must be supplied toward the end of the Windows Vista boot process.
Obviously either of these methods can be used to add yet another layer of security to the Windows Vista startup process. However, if this floppy disk is created and lost (or if you assign a password and forget it), it's unlikely that you can access your system. Although some of the tools designed to recover passwords claim to be able to bypass or reset this password, they should not be relied upon as a backup method.
The tool used to change how the startup key is stored or protected on a Windows Vista system is called Syskey, and can run by any Administrator user account.
Follow these steps to run the Syskey utility on a Windows Vista system:
-
Click Start. In the Search text box, type Syskey.exe and press Enter.
-
When the User Account Control dialog box appears, click Continue.
-
Type syskey.exe in the Open text box and click OK.
-
At the Securing The Windows Account Database window, click Update.
-
To protect the system key with a password, choose Password Startup (see Figure 3-10), enter and confirm your password, and click OK. Alternatively, to store the system key on a floppy disk, choose Store Startup Key On Floppy Disk, click OK, and insert a blank disk when prompted.
-
When the Success dialog box appears, click OK.
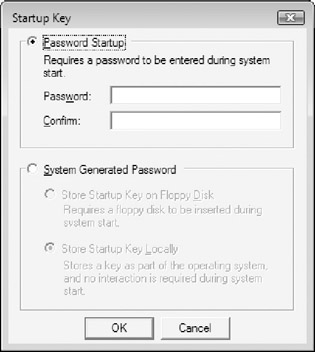
Figure 3-10: Configuring a startup password with Syskey.
Follow these steps to boot a Windows Vista system protected by a startup password:
-
Restart your Windows Vista system.
-
Toward the end of the boot process, the Windows Vista Startup Password dialog box will appear. Enter the startup password that you configured with the Syskey tool, and click OK.
-
When the startup password is accepted, log on to Windows Vista normally.
| Caution | If you choose to store the Windows Vista Startup key on a floppy disk, be sure to make a copy of this disk and store it in a safe place in case the original is ever lost or stolen. Without a disk, you will not be able to log on to your Windows Vista system. |
Even if you use the strongest user account passwords and implement multiple layers of password security, no computer is ever 100 percent secure (in a true computer security sense) if other people can gain physical access to it. The best you can do when attempting to secure your Windows Vista system is implement the strongest security settings available, and then ensure that physical access to the computer is restricted to users (to the greatest extent possible) who you know and trust. If this side of things has you worried, however, you'll want to explore some of the options that can be used to better secure the physical aspects of your computer.
If your Windows Vista system is a desktop computer, you may want to look into locking cases that require an actual key to gain access to internal components such as hard drives, CMOS batteries, and so forth. Of course, that won't stop a thief from picking up the computer and walking away with it.
This is especially true with laptop computers, where theft tends to be far too common. A variety of vendors supply cable locks that can be used to fasten both laptop and desktop PCs to an immovable fixture, but you shouldn't rely on these as more than a temporary barrier to theft. Although they may keep a laptop safe in a public location, they're no match for a set of good bolt cutters. To address this issue, some cable locks include piercing alarms that are triggered when cut or moved, and other manufacturers provide complete system replacement insurance if your computer is stolen while locked down. That may provide some comfort on the financial front, but it doesn't address the fact that someone else may now have access to your personal files and e-mail messages.
Of course, don't forget the old tried-and-true battle horse of physical security - the locked door. Sometimes the most simple security techniques are also the most effective.
EAN: 2147483647
Pages: 135