Implementing Password and Account Lockout Policies
Convincing users to apply passwords to their user accounts is sometimes tough, but getting them to configure good strong passwords is even more challenging. Even after you've explained their importance and outlined the potential dangers of choosing a weak password, most users still opt for a basic or familiar password that they have no trouble remembering. Even worse, some users configure a password in short term, and then remove it once they get tired of typing it in.
Understanding that old habits die hard, Windows Vista (Business, Enterprise, and Ultimate edition only) includes the capability to configure policy settings that enforce password requirements on all system users. For example, you can configure settings that control how often passwords must be changed, how long they must be, and even force users into selecting a reasonably strong password. As you've already learned (by the fact that users can log on without a password), no such policy settings are enabled or enforced by default. If you want to get your system's security situation under control, however, the configuration of Password Policy settings is an absolute necessity.
The Windows Vista primary Password Policy settings include:
-
Enforce Password History - Dictates the number of new and unique passwords a user must use before he can go back to using an older password. The higher this number, the better.
-
Maximum Password Age - Controls how many days a user can use her current password before being forced to change it. Forty-two days is the default value, but shorter time periods are obviously more secure.
-
Minimum Password Age - Controls how many days a user must use his current password before he's allowed to change it. Effectively, this setting stops users from getting around settings like Enforce Password History by immediately changing their password a number of times until they can get back to using their previous (and perhaps preferred) password. By default, users are allowed to change their password immediately. Consider setting this value to a few days or more.
-
Minimum Password Length - Dictates the minimum number of valid characters in a user's password. Eight is a good start, but 15 or more is definitely more secure.
-
Password Must Meet Complexity Requirements - Controls the characteristics that make a user's password valid, including character requirements.
| Note | If you enable the Password Must Meet Complexity Requirements policy setting, user passwords must be at least six characters long, cannot contain the users' real names or usernames, and must include at least three of the following four elements: uppercase letters, lowercase letters, numbers, and symbols. The password Mydoghasfleas would not meet these complexity requirements, but the password My&do6hasFlea5 would. |
Password Policy settings are an excellent first step toward enforcing some basic rules and requirements in the user password arena. However, it's equally important to ensure that your Windows Vista system can guard against hacking attempts. For example, under the Windows Vista default configuration, any person can try to log on with another user's account an unlimited number of times by attempting to guess the password. Implementing password complexity requirements will certainly make the challenge more difficult, but it's still better to be safe than sorry.
Windows Vista Professional systems address the issue with Account Lockout Policy settings. In a nutshell, these policy settings enable you to dictate how many incorrect logon attempts can occur before an account is locked. When locked out, an account cannot be used to log on to your Windows Vista system until an Administrator unlocks it, or a pre-configured period of time has passed.
The Windows Vista Account Lockout Policy settings include:
-
Account Lockout Duration - Dictates the number of minutes that an account remains locked out until it is unlocked automatically. If set to a value like 5, a user could attempt to log on again 5 minutes after being locked out (enough time to take a break, and perhaps remember the password). If set to 0, accounts are locked out until unlocked by an Administrator.
-
Account Lockout Threshold - Controls the number of failed logon attempts before a user's account is locked out. When set to 0, user accounts will never be locked out.
-
Reset Account Lockout Counter After - Dictates the number of minutes that must pass before the account lockout threshold value is reset to 0.
The Reset Account Lockout Counter After setting can be a little confusing. The purpose of resetting the account lockout counter is to ensure that incorrect logon attempts don't add up over time. For example, if you set the account lockout threshold to 3, then 3 incorrect logon attempts will lock out the account - regardless of whether they all happened over the last minute, or cumulatively over the course of the last six months. Configure Reset Account Lockout Counter to a value like 30 minutes to ensure that incorrect logon attempts don't accumulate toward a lockout days or weeks from now. Every user occasionally forgets or mistypes his password!
| Caution | When Account Lockout settings are configured to lock out accounts on a Windows Vista Professional system, these settings are enforced for all users, including those with Administrator accounts. The only exception is the built-in Administrator account, which cannot be locked out. Don't forget the password (and potentially the new username) that you've applied to this account. If all other user accounts get locked out, you need to be able to log on with this account to unlock them. |
Configuring Password Policy Settings
Security-related policy settings are configured using the Local Security Policy MMC on a Windows Vista Professional system. Only users with Administrator accounts can use and make configuration changes with this tool.
Follow these steps to configure password policy settings on a Windows Vista Professional system:
-
Click Start → Control Panel.
-
In the left-hand Control Panel menu, click Switch To Classic View (if necessary).
-
Double-click Administrative Tools.
-
Double-click the Local Security Policy shortcut.
-
When the User Account Control dialog box appears, click Continue.
-
In the Local Security Settings window, expand Account Policies.
-
Click the Password Policy folder (Figure 3-2) to view the default policy settings.
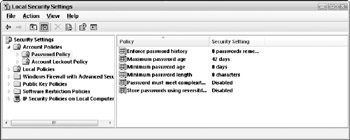
Figure 3-2: Password Policy settings. -
Double-click Enforce Password History to open its properties window (see Figure 3-3). Select the number of user passwords to be remembered, and then click OK.
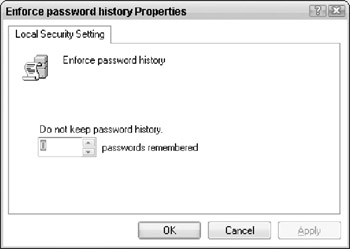
Figure 3-3: Enforce password history -
Double-click Maximum Password Age, select an appropriate value in days, and click OK.
-
Double-click Minimum Password Age, select the minimum number of days that a user must use a given password before changing it, and click OK.
-
Double-click Minimum Password Length, select a minimum length for user password (such as 8), and click OK.
-
Double-click Password Must Meet Complexity Requirements, click Enabled, and then click OK.
-
Close the Local Security Settings window.
Follow these steps to test your new password policy settings on a Windows Vista Professional system:
-
Click Start → Control Panel.
-
Double-click the User Accounts applet.
-
At the Make Changes To Your User Account screen, click Change Your Password.
-
At the Change Your Password screen, enter your current password and then enter (and confirm) a new password such as testpass that does not meet the new password policy requirements. Click Change Password. The dialog box shown in Figure 3-4 appears, stating that the new password does not meet the configured password policy requirements. Click OK.
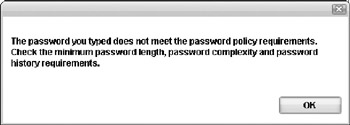
Figure 3-4: Message displayed when a password doesn't meet policy requirements. -
Enter a new password that does meet your new password policy requirements and click Change Password.
Configuring Account Lockout Policy Settings
Like Password Policy, Account Lockout Policy settings are configured using the Local Security Policy tool, which is only accessible by Administrators.
Follow these steps to configure account lockout settings on a Windows Vista Professional system:
-
Click Start → Control Panel.
-
In the left-hand Control Panel menu, click Switch To Classic View (if necessary).
-
Double-click Administrative Tools.
-
Double-click the Local Security Policy shortcut.
-
When the User Account Control dialog box appears, click Continue.
-
Click the Account Lockout Policy folder to view the default policy settings (see Figure 3-5).
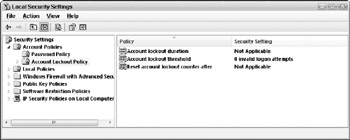
Figure 3-5: Account Lockout Policy settings. -
Double-click Account Lockout Threshold and then configure the number of invalid logon attempts (for example, 3) that can be attempted before an account is locked out. Click OK.
-
When the Account Lockout Threshold is configured, the Suggested Value Changes window will open to suggest settings for the remaining Account Lockout Policy settings. Click OK.
-
Double-click Account Lockout Duration, and type 0 in the Account Is Locked Out For box. When set to 0, accounts are locked out indefinitely. Click OK.
-
Close the Local Security Policy window and log off.
Follow these steps to test your new account lockout policy settings and unlock a locked user account:
-
Attempt to log on to another user's account using an incorrect password until you reach the configured Account Lockout Threshold.
-
After configured number of failed attempts has been reached, you get a message stating that the account has been locked. Click OK.
-
Log on with your Administrator account.
-
Click Start, right-click on Computer, and select Manage to open the Computer Management MMC. User accounts cannot be unlocked via User Accounts in Control Panel.
-
When the User Account Control dialog box appears, click Continue.
-
Expand Local Users and Groups, and then click the Users folder.
-
Double-click the locked-out user account.
-
On the General tab, uncheck the Account Is Locked Out check box, and click OK.
-
Close the Computer Management MMC.
Implementing Account Lockout Policy settings is one easy way to track whether someone has been trying to log on to your Windows Vista system as another user. Assuming that the user in question hasn't simply forgotten his username and password combination (you'll have to ask him), chances are good that another person has been playing a password guessing game with the account.
A suspiciously locked-out account provides a good clue that something may be amiss, but there is another way to gather more information on logon attempts. The tool you need for this purpose is the Security Log in Event Viewer, which automatically logs details of all successful and failed user logon attempts on both Windows Vista Home and Professional systems.
To check the contents of your system's security log, follow these steps:
-
Click Start, right-click Computer, and select Manage. The Computer Management MMC opens.
-
When the User Account Control dialog box appears, click Continue.
-
Expand Event Viewer → Windows Logs and click Security. Successful events are listed with a key icon; failed events are designated with a lock.
-
In the Task Category field look for events of the Logon/Logoff type. Click a Failure Audit event of this type to view details about the event.
In the case of a failed logon attempt, the Description section lists details including the user account associated with the logon attempt, the reason the logon failed, and the time at which the event occurred.
As a general rule, take some time to browse through your system's security log at least every couple of weeks, even if nothing appears to be amiss. You may not find anything suspicious, but it's better to keep an eye open for potential issues than to assume that everything is perfectly fine.
EAN: 2147483647
Pages: 135