Performance
| Networks will always experience problems. One of your goals is to make sure that you maximize your performance while minimizing your problems. You have to deal with three main issues while balancing networking performance and problems: application performance, capacity planning, and fault management. The first thing you'll want to do is to develop a baseline of the performance of your existing network. You need to document your existing network, including the layout of your devices and their current operation, CPU and buffer utilization, memory usage, and throughput. You also need to determine adequate response times for your users and their applications. After building a baseline, you need to take the growth in your network into consideration and perform capacity planning. You also need to use monitoring tools so that you can closely watch the operation of your network. Monitoring tools can also be used to help troubleshoot networking problems and issues, from connection problems to bandwidth issues. The following sections discuss the use of the switched port analyzer (SPAN) feature and the Network Analysis Module (NAM). Switched Port AnalyzerThe Switched Port Analyzer enables you to mirror traffic from one or more interfaces on a switch to a port that is connected to a network analyzer, packet sniffer, or remote monitoring (RMON) probe. This traffic can then be analyzed and processed for reporting. One nice feature of SPAN on Cisco's Catalyst switches is that it does not affect the performance of the switch, which is based on the switching process in the switch. For example, the Cisco 6000 moves a frame from an interface to the bus. Any other switch port can move that frame from the bus to the port's outbound buffer. The switching engine in the switch then tells which interfaces to drop the frame, indicating that the frame is not to be further processed by those interfaces. With SPAN, there is no extra overhead involved in the switching process because the frame is already copied into the buffer by the SPAN port.
SPAN TypesThere are two basic types of SPAN: local and remote. Local span has interfaces on the local switch redirected to a local port with an analyzer connected to it. The local SPAN feature supports the mirroring of traffic from both source ports and VLANs to one or more destination ports. If you're mirroring traffic in the inbound direction, it is called ingress SPAN. If you're mirroring traffic in the outbound direction, this is called egress SPAN. Remote SPAN is discussed later. SPAN ConfigurationBefore you set out to configure local SPAN on your Catalyst switch, you should be aware of the following:
Setting up SPAN is a two-step process: You must first specify which traffic to mirror and then specify which interface is the SPAN port. Use this command to specify the mirrored traffic: Switch(config)# monitor session session_# {source interface type/port_#}|{vlan VLAN_#} [,|-|rx|tx|both] The session number is used to group your monitor session commands. Following this is the port, ports, VLAN, or VLANs that you want to mirror. If you have multiple sources, separate them with a comma (,). For a range of ports or VLANs, separate them with a dash (-). If you don't specify which direction to capture traffic on the source port or ports, it defaults to both, for both the transmit and the receive directions. You can override this with the rx (receive) and tx (transmit parameters). Here is a simple example of capturing traffic from fastethernet0/1: Switch(config)# monitor session 1 source interface fastethernet0/1 both After you've specified the mirrored traffic, you next need to specify the SPAN port itself: Switch(config)# monitor session session_# destination interface type/port_# [encapsulation isl|dot1q] The session number you specify here references the session number of the source ports. You follow this with the destination interface. If the interface is a trunk, you can optionally specify the encapsulation type (this is only for IOS switches that support both trunking types). For the 2950, you don't need to specify the trunking encapsulation because the 2950 supports only 802.1Q. Here's a simple example of specifying the SPAN port for our previous monitoring session (1): Switch(config)# monitor session 1 destination interface fastethernet0/5 When you've configured the monitor session destination command, your switch is mirroring traffic from the specified source ports to the specified SPAN port.
Remote SPANRemote SPAN (RSPAN) is an extension of local SPAN. With local SPAN, all the source and destination ports are on the same switch. With RSPAN, these ports can be on different switches. This is very handy if you have only a limited number of network analyzers or RMON probes, but still want to see certain traffic across all your switches in an area.
The configuration of RSPAN is a three-step process. First, you must create a dedicated VLAN for RSPAN traffic that travels between the switches. Use the following configuration: Switch(config)# vlan VLAN_# Switch(config-vlan)# remote-span Assuming that you're using VTP in a server/client configuration, execute this command on the server switch. If you're using transparent mode with VTP, you'll have to configure the preceding command on all your switches that will see the RSPAN VLAN: the source, intermediate, and destination switches. The RSPAN VLAN is treated differently on the switches as compared to other VLANs. First, no MAC address learning occurs on the RSPAN VLAN because this is only mirrored traffic for network analysis purposes. Second, the RSPAN VLAN shows up on your trunks. Therefore, it is highly recommended that you either use VTP pruning or manual pruning to ensure that RSPAN traffic is not flooded across your entire network, but is contained within only those switches from the source port(s) to the destination. Third, to reduce any STP issues, BPDUs are not mirrored with RSPAN. If you have any performance issues with the amount of RSPAN traffic you're mirroring, you can use ACLs to filter information that is sent to the destination port with the analyzer or probe. In this example, VLAN 100 is set up as the RSPAN VLAN: Switch(config)# vlan 100 Switch(config-vlan)# remote-span After you've configured your RSPAN VLAN, you must set up monitoring for your source ports. This is the same command that you used in the local SPAN configuration (monitor session source). After defining the source ports on a switch, you have to specify the destination port. If the network analyzer or RMON probe is on a different switch, use the following command: Switch(config)# monitor session session_# destination remote vlan VLAN_# This command specifies the RSPAN VLAN to use to get the mirrored traffic to the destination.
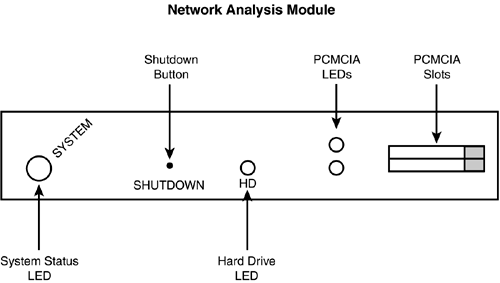
Here's a simple example where traffic from session 1 is sent out any interface(s) associated with the RSPAN VLAN: Switch(config)# monitor session 1 destination remote vlan 100 On the switch that has the network analyzer or probe connected to it, use the following configuration: Switch(config)# monitor session session_# remote vlan VLAN_# Switch(config)# monitor session session_# destination interface type/port_# The first command specifies that traffic coming into the switch in the RSPAN VLAN should be mirrored. That traffic is mirrored to the port specified by the second command. Here's a simple example: Switch(config)# monitor session 1 remote vlan 100 Switch(config)# monitor session 1 destination interface fastethernet0/5 It's important to point out that you do not have to configure anything special on intermediate switches that do not have any source ports just make sure that these switches have the RSPAN VLAN in their configuration. SPAN VerificationWhen you've configured SPAN or RSPAN, you can verify your configuration with this command: Switch(config)# show monitor session Here's an example of the output of this command: Switch# show monitor session 1 Session 1 --------- Type: Local Source Session Source Ports: RX Only: None TX Only: None Both: Fa0/1-3 Source VLANs: RX Only: None TX Only: None Both: None Source RSPAN VLAN: None Destination Ports: Fa0/5 Encapsulation: DOT1Q Ingress: Enabled, default VLAN=5 Reflector Ports: None Filter VLANs: None Dest RSPAN VLAN: None This is an example of local SPAN, where the source ports are fa0/1-3 and the destination port is fa0/5 (attached probe). Network Analysis ModuleInstead of using an external network analyzer or RMON probe to analyze or gather your traffic, the Catalyst 6000 Series switches support a Network Analysis Module (NAM). A NAM is similar to an RMON probe. You can use it to gather RMON (RFC 1757) and RMON2 (RFC 2021) information. A NAM cannot perform analysis on the captured data. However, you can use Cisco's TrafficDirector or any IETF-based RMON-gathering product. A NAM can only gather traffic from Ethernet-based ports or statistics exported from NetFlow data. Initial ConfigurationThe purpose of this section is not to show you the complete configuration process that you have to go through to set up a NAM. Instead, I'll cover the very basic configuration steps pertaining to the NAM. After you have the NAM up and running, most of the configuration is typically done via an SNMP-based product, such as CiscoWorks 2000, and all the data gathering is done from TrafficDirector or a similar RMON product. Basic NAM ConfigurationUnlike the configuration discussed so far in this book, the configuration of the NAM is done within the NAM module. The NAM module actually runs its own operating system and has its own disk drive. Figure 10.1 shows a picture of the NAM module. Figure 10.1. Network analysis module.
As you'll notice in Figure 10.1, the NAM does not have external connections, like a console or Ethernet interfaces. Instead, all interaction with the NAM is done across the backplane of the Catalyst 6000 Series switch. To log in to the NAM, you first log in to your Catalyst switch and use the following command: Switch# session slot slot_# processor 1 You are then logged in to the NAM, where you'll be prompted for a username and password. To make configuration changes on the NAM, you'll have to log in to the root account. If you aren't sure which slot your NAM is located in, use the show module command: Switch# show module Mod Ports Card Type Model Serial No. --- ----- ------------------------------------ ----------------- ----------- 2 2 Catalyst 6000 supervisor 2 (Active) WS-X6K-SUP2-2GE SAD04450LF2 3 48 48 port 10/100 mb RJ-45 ethernet WS-X6248-RJ-45 SAD03181469 5 0 Switching Fabric Module (Active) WS-C6500-SFM SAD04420JR3 6 2 Network Analysis Module WS-X6380-NAM SAD05130AXD In this example, the NAM is in slot 6.
When you're in the NAM, you'll have to enable basic IP connectivity. Doing so allows an external management device, such as TrafficDirector, to access the NAM. Here's the basic IP configuration you should perform, shown in Listing 10.1. Listing 10.1 NAM IP Configuration Commandsroot@localhost# ip address IP_address subnet_mask root@localhost# ip broadcast IP_network_broadcast_address root@localhost# ip gateway router_default_gateway_address root@localhost# ip host name_of_NAM root@localhost# ip domain domain_name root@localhost# ip nameserver DNS_server_address The ip address command in Listing 10.1 assigns an IP address to the NAM. The ip broadcast command assigns the IP broadcast address for the network number that the NAM is associated with. The ip gateway command assigns the address of the router that will function as the default gateway for the VLAN that the NAM is associated with. The ip host command assigns a name to the NAM used within IP and the ip domain command assigns the domain name. The ip nameserver command assigns the DNS server address that the NAM should use to resolve fully qualified domain names to IP addresses. Listing 10.2 shows a simple example. Listing 10.2 Using the ip nameserver Commandroot@localhost# ip address 172.16.254.8 255.255.255.0 root@localhost# ip broadcast 172.16.254.255 root@localhost# ip gateway 172.16.254.254 root@localhost# ip host nam1 root@localhost# ip domain dealgroup.com root@localhost# ip nameserver 172.16.253.2 To view your IP configuration, use the show ip command: root@localhost# show ip IP address: 172.16.254.8 Subnet mask: 255.255.255.0 IP Broadcast: 172.16.254.255 DNS Name: nam1.dealgroup.com Default Gateway: 172.16.254.254 Nameserver(s): 172.16.253.2 To have TrafficDirector or an SNMP manager access your NAM, you must configure SNMP on the NAM, as shown in Listing 10.3. Listing 10.3 NAM SNMP Configuration Commandsroot@localhost# snmp location descriptive_location_information root@localhost# snmp contact name_of_a_contact_person root@localhost# snmp name SNMP_name_of_NAM root@localhost# snmp community string_value rw root@localhost# snmp community string_value ro The snmp location command specifies a descriptive location of where the NAM is located (the switch, the floor of the building, the building itself, and the like). The snmp contact command lists the person someone should contact if there is a problem with the NAM. The snmp name command assigns a name to the NAM used with SNMP interaction. The snmp community commands assign the read/write and read-only community strings used to gain access to the NAM. To view your SNMP configuration, use this command: root@localhost# show snmp SNMP Agent: nam1.dealgroup.com 172.16.254.8 SNMPv1: Enabled SNMPv2C: Enabled SNMPv3: Disabled community check read community mate write sysDescr "Catalyst 6000 Network Management Module (WS-X6380-NAM)" sysObjectID 1.3.6.1.4.1.9.5.1.3.1.1.2.223 sysContact "The Big Cheese, Administrator: 555-1212" sysName "6500-NAM - Slot 3" sysLocation "Building 1, Floor 1, Data Center" If you experience connectivity problems with the NAM, reboot it and try again. After you've finished your IP configuration, you must enable the HTTP server on the NAM: root@localhost# ip http server enable This enables you to access the NAM via a Web browser interface. You can optionally use a secure HTTP server, but its configuration is beyond the scope of this book. Please refer to the NAM reference in the "Need to Know More?" section at the end of this chapter for additional information. Autostart ConfigurationAutostart is a NAM feature that enables you to gather RMON statistics of the Catalyst 6000 switch that the NAM is installed in (without having to set up SPAN). As soon as your switch is booted up and the NAM initializes, the NAM can begin gathering these statistics. However, this function is disabled by default. To enable it, use the following command: root@localhost# autostart collection_name enable The collection names you can specify include addressmap, art, etherstat, priostats, and vlanstats. The art collection state is for gathering application response time information based on sending and receiving data at the transport layer of the OSI Reference Model. This feature is not included with the basic NAM module; it requires the purchase of an additional software license. You can disable a collection name by using the keyword disable instead of enable. When you've either enabled or disabled a specific collection name, you'll have to reboot the NAM.
Switch ConfigurationAfter you've prepared the NAM for gathering traffic, you can set up the Catalyst 6000 Series switch to interface with the NAM. This requires two different configurations. First, you have to associate the NAM's IP address with a VLAN. Second, you have to associate it as a destination port for SPAN. In Figure 10.1, you can see that the NAM doesn't have any physical interfaces. Instead, it has two logical interfaces: 0 and 1. Interface 0 is associated with IP and interface 1 is associated with the SPAN function. Because the NAM has an IP address, you'll want to associate the IP interface with the VLAN where your management devices are located by using the following configuration: Switch(config)# interface gigabit slot_#/0 Switch(config-if)# switchport access vlan VLAN_# Remember to use a port number of 0 for the IP interface. Next, you need to associate the NAM's logical SPAN interface with the destination port for traffic mirroring: Switch(config)# monitor session session_# destination interface gigabit slot_# /1 This is the same command we discussed earlier in the "SPAN Configuration" section. Remember to use a port number of 1 for the SPAN port on the NAM. Here's a simple example associating it with the management VLAN, which is VLAN1: Switch(config)# interface gigabit 3/0 Switch(config-if)# switchport access vlan 1 Switch(config-if)# exit Switch(config)# monitor session 3 destination interface gigabit 3/1 In this example, gigabit 3/1 (the NAM's monitoring port) has traffic from session 3 mirrored to it.
|
EAN: 2147483647
Pages: 171
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations
- An Emerging Strategy for E-Business IT Governance
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Governing Information Technology Through COBIT
- Governance Structures for IT in the Health Care Industry