NAC Appliance Manager
| The NAC appliance servers are managed by the NAC appliance manager. NAC appliance also offers optional subscription services for automatic OS, antivirus, and antispyware updates. A web browser is used as the client GUI to the NAC appliance manager. Configuration from the web GUI client is secured by using HTTPS between the client web browser and the NAC appliance manager. Users must provide a username and password to log on to the NAC appliance manager. Usernames and passwords can be stored in an external LDAP database or can be stored locally on the NAC appliance manager server. In addition to LDAP, Kerberos is also supported as an external administrator authentication method. The NAC appliance manager can be ordered as an appliance or as standalone Linux software. The NAC Appliance (CCA) Manager contains a monitoring summary page that contains information about product version and online users. This monitoring summary is displayed in Figure 7-1. Figure 7-1. NAC Appliance Manager Monitoring Summary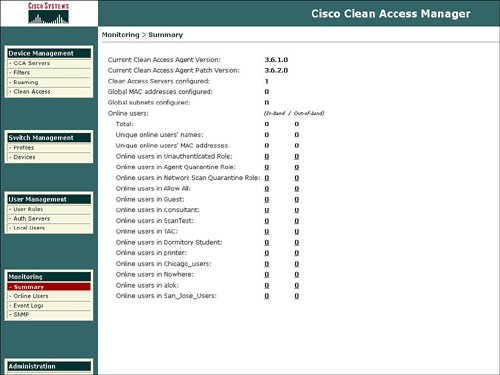 The main functional areas of the manager homepage are organized under the five categories, as follows:
Device ManagementDevice Management is the first item displayed in the manager. Device Management features are configured in the following categories:
CCA ServersThe CCA Servers option displays a list of managed servers and also allows the ability to define a new server to be managed. The process to add a new server and select the server mode is displayed in Figure 7-2. Figure 7-2. Add New CCA Server with Server Type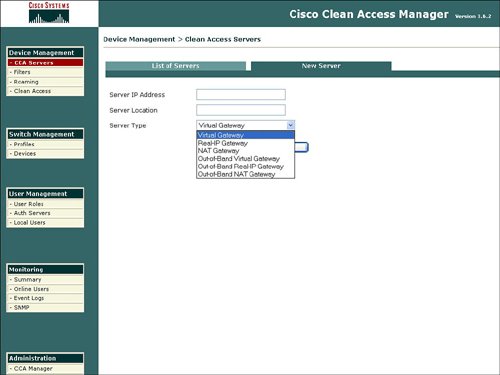 The Cisco Clean Access Server can be configured in the following modes:
The next sections describe each mode in detail. Real IP GatewayIn the Real IP Gateway mode, the server sits between an untrusted subnet and a trusted subnet. The IP addresses for the server interfaces must be configured. Static routes must be configured since the server is not a router and does not broadcast routes. Both DHCP server and DHCP relay functions are supported in this mode. The server can either assign authenticated users an IP address from a DHCP pool or allow the DHCP-assigned process to relay through the server from the internal DHCP server on the trusted network to the end point on the untrusted network. Architecturally, this is similar to the functionality of a router. Virtual IP GatewayThe Virtual IP Gateway mode is essentially a bump-in-the-wire deployment. In this mode, the server is inserted inline into an existing network segment. No readdressing of subnets or IP addresses is required for the Virtual IP Gateway, or bump-in-the-wire, deployment. In this mode, both interfaces on the server can share the same IP address. Only DHCP relay is supported because the Virtual IP Gateway does not allow a native DHCP server. VLAN termination also is not supported in Virtual mode. The manager must reside on a different subnet from the server, even in Virtual IP Gateway mode. NAT GatewayThe NAT Gateway includes a NAT function that enables the user IP address on the untrusted network to be translated to a new IP address on the trusted network. If you select NAT Gateway, you will be presented with a pop-up window that indicates that NAT Gateway is recommended only for testing/demo purposes. The CCA (NAC Appliance) 3.6 documentation takes this idea a step further and indicates that NAT Gateway mode is not supported for production network deployment. OOB Real IP Gateway, OOB Virtual IP Gateway, and OOB NAT GatewayCisco introduced support for out-of-band (OOB) deployments with the CCA 3.5 release. Prior to OOB support, the server was always inline with all user traffic from the client. This user traffic includes the initial authentication traffic and all of the actual data traffic from the client. OOB support allows the server to participate only in the authentication, scanning, and remediation flows for the user client and not the data traffic from the client for web browsing, e-mail, and so on. OOB support enables the implementation of a NAC deployment with fewer servers and can result in a more scalable solution, as all data traffic does not have to travel through a server after authentication. The OOB solution requires a separate license key. A server can be deployed in OOB Real IP Gateway, or OOB Virtual IP Gateway modes. An OOB deployment can remove the bottleneck of the processing power of the server for data traffic. OOB deployment enables greater than 1 Gbps, because all data traffic does not have to flow through the server after successful authentication. In an OOB deployment, only network traffic for authentication, security posture validation, and any required remediation flow through the NAC appliance server. OOB is an option only for wired (LAN) networks because OOB is not supported on wireless networks. It is also not recommended to enable 802.1x on a LAN switch interface that will participate in an OOB NAC appliance deployment due to potential conflicts with VLAN assignments. The OOB deployment modes work in concert with the supported line of Layer 2 LAN switches. The manager defines which VLAN on the LAN switch will be assigned to the authenticating device. The manager uses SNMP v2c and v3 to obtain MAC address table information and to assign VLANs to authentication devices. The out-of-band modes also support VLAN quarantine because the server performs device remediation and can reside on the quarantine VLAN. Supported Catalyst LAN switches for OOB deployments include the following device models:
FiltersFilters provide the ability to exclude devices or subnets from the authentication process. Many security operators will want to provide filters to nonPC devices like printers and IP phones in order to ensure easy access to the network without going through the authentication process. Filters can be configured based upon device MAC address. A filter enables the ability to automatically allow or deny a device on to the network. Device filters also enable the ability to put a machine into a specific user role, such as employee or consultant, based upon MAC address. Figure 7-3 provides an example of device filters. Figure 7-3. Device Filters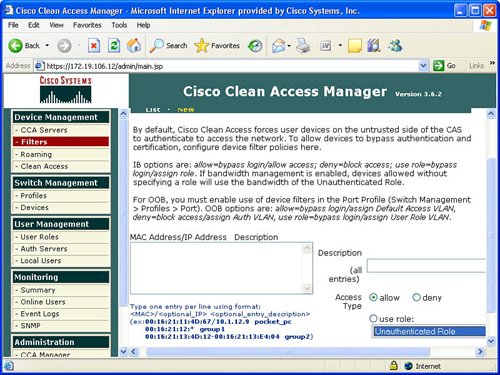 In addition to MAC address device filters, the manager also supports the configuration of filters based upon subnet or IP address. The Device Management area of the manager allows the configuration of a user to bypass authentication based upon the user's IP address. This subnet filter capability also supports the mechanism to permit or deny a user access to the network based upon IP address. Similar to device filters, a user can also be assigned a user role such as employee or consultant based upon the source IP address. An example of how to configure a subnet filter is provided in Figure 7-4. Figure 7-4. Subnet Filters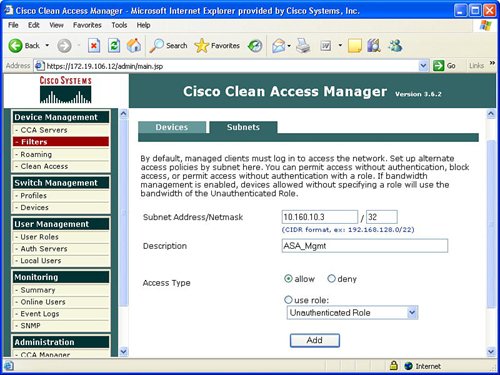 Note Previous versions of the NAC appliance managed wireless access points and allowed mobile users to roam between different access points and maintain an authenticated connection. Roaming and wireless access point management is now performed by the wireless LAN controller (WLC) management product and is no longer configured by the NAC appliance manager. Clean AccessThe Clean Access area under Device Management in the manager allows the display and configuration of exempt devices, floating device, general setup, network scanning, and agent configuration. Exempt devices are devices that are exempt based upon MAC address as discussed earlier in this chapter. Floating devices are designed for public places like online kiosks. Floating devices are authenticated during the user session. Once the user logs off, the next user on that deviceeven if it is the same usermust be reauthenticated. Floating devices are defined by their L2 MAC address. An example of the location to configure a floating device by adding its MAC address is displayed in Figure 7-5. Figure 7-5. Floating Device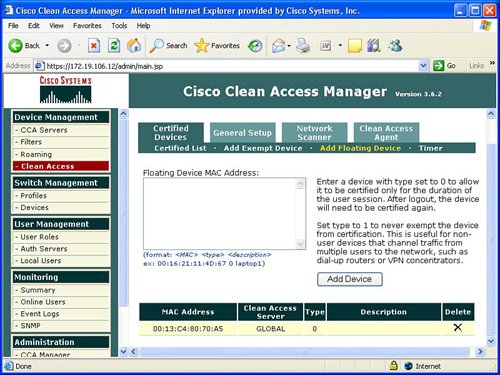 General setup involves configuring the logon or restriction information that is displayed for the users in the various user roles. General setup also specifies whether the agent is required for a specific user role. Figure 7-6 displays an example of the General setup configuration parameters for a particular user role. Figure 7-6. General Setup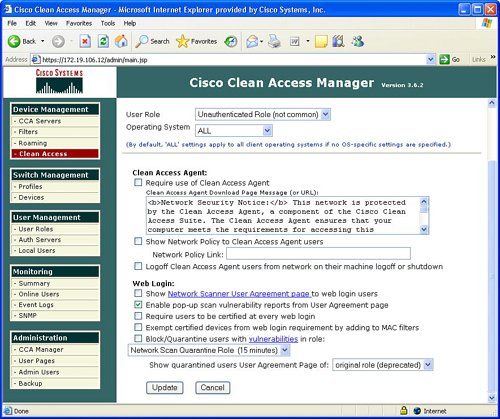 The NAC appliance contains an embedded Nessus network scanner. The NAC appliance server supports Nessus plug-ins and provides a mechanism for users to download new Nessus plug-ins. Figure 7-7 provides the configuration options for the user-agreement that is displayed to the user to access a network, based upon a network scan. Figure 7-7. User Agreement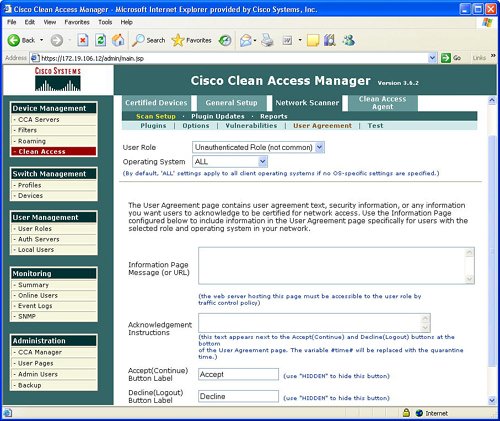 The optional agent provides an extra dimension of scanning and authentication to Windows clients. The agents can be distributed to Windows clients directly from the server. Agents allow registry checks to determine if OS hotfixes are applied. These registry checks can also be used to determine the existence of a specific software application and the inspection for a potential worm or virus infection. In addition to registry checks, rules can also be defined in the manager to check if an end station with the agent has a specific file on the machine, or if a specific service or application is active on the Windows end station. Figure 7-8 displays some of the rules check list to determine if specific Windows hotfixes have been applied to a client with the agent. Figure 7-9 shows the parameters used to create a rule to inspect a client for a specific registry key. Figure 7-10 displays rules for checking the presence of specific antispyware products on clients with the agent installed. Figure 7-8. Rules Check List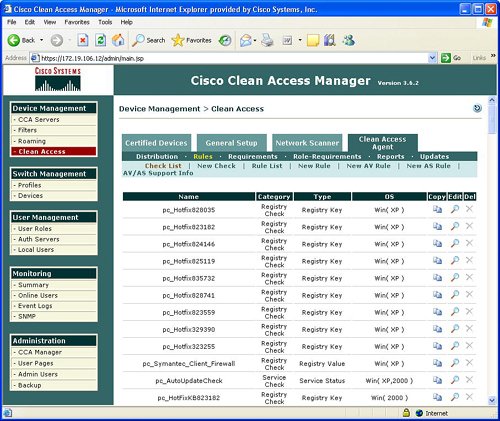 Figure 7-9. Registry Check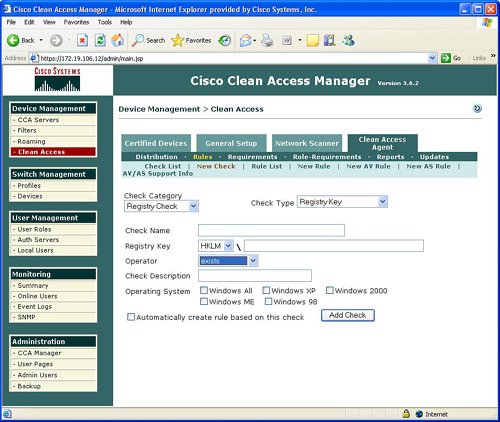 Figure 7-10. Antispyware Check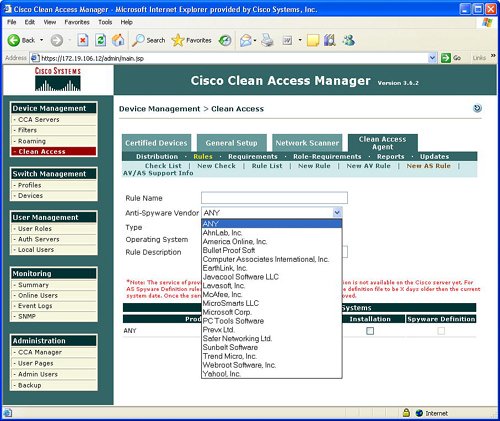 Switch ManagementThe switch management function is designed to configure LAN switches that will be used in an OOB NAC appliance deployment. The NAC appliance manager uses SNMP to manage the OOB LAN switches. Switch management is composed of the profiles and devices categories. A profile defines the type of LAN switch and the SNMP parameters that are used to manage the LAN switch. Figure 7-11 displays an example of the location and settings to configure a LAN switch profile. Figure 7-11. Profile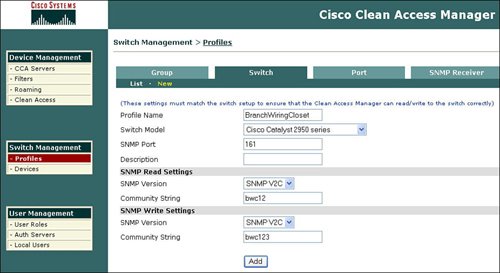 The device option under switch management enables the user to define or discover LAN switches that can be used for an OOB deployment. The IP address of a LAN switch can be defined, or the user can enter a range of IP addresses to search and discover LAN switches that can be used for OOB. The device option also displays the discovered clients or end stations of the OOB LAN switch. The clients are discovered based upon SNMP MAC notification updates or Link-up/Link-down SNMP traps from the LAN switch to the NAC appliance manager. User ManagementEach user is classified to participate in a specific user role. User roles are both predefined and customized. User roles are used to determine what an authenticated user can do on a network. Some of the parameters associated with user roles include the following:
By default all user traffic is denied unless explicitly permitted by a global or local policy for authenticated users. Figure 7-12 displays a sample list of user roles. Figure 7-12. List of Roles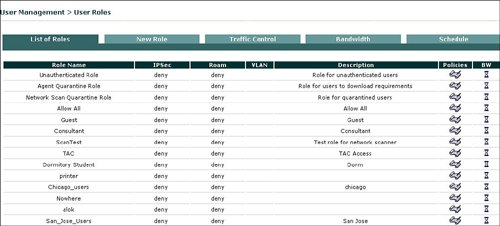 NAC appliance has a quarantine role for Windows users with the agent and a quarantine role for users with a vulnerability that was discovered during a network scan by the NAC appliance. The vulnerable user is placed in the quarantine role until they update their device to remove the identified vulnerability. Users will be moved from the quarantine role after remediation and a successful logon. One of the main drivers behind the different user roles is the definition of what a specific type of user is allowed to do on the network. The quarantine role allows users to access only a part of the network in order to download the required software updates to address the identified vulnerability in order to be remediated and be removed from the quarantine role. Figure 7-13 displays an example of how the quarantine role is allowed permission to access only the remediation server. Users who are placed in the quarantine role must be remediated before they can join one of the other user roles that are designed for successful authentication and certification. Figure 7-13. Traffic Control of Agent Quarantine Role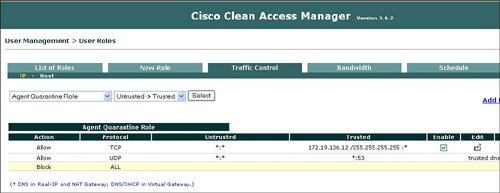 Several mechanisms can associate, or map, a user to a user role during the authentication process. One example is the ability to map a user to a role based upon their VLAN ID. The NAC appliance can authenticate users who are locally defined on the NAC appliance or leverage an external LDAP, RADIUS, or NTLM (Windows NT LAN Manager) database for user authentication. The NAC appliance manager allows the ability to define a local user, a user's logon password, and mapping to a specific user role that will define what the user can do once authenticated into the network. Figure 7-14 displays an example of defining a new user on the local user database and mapping that user to the consultant user role. Figure 7-14. Create a Local User and Map to User Role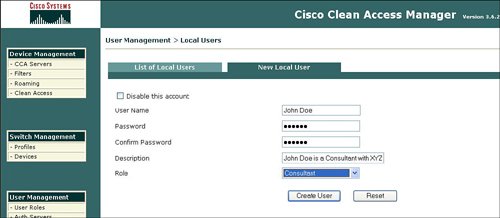 Leveraging of an external authentication server offers several advantages over using the local user database on the NAC appliance. The benefits of the external authentication server include scalability and the ability to deploy the NAC appliance without having to manually redefine each user. The NAC appliance manager allows mapping rules to be defined to determine which role a user is assigned to after authentication and certification by the NAC appliance. Figure 7-15 displays how you can use an external LDAP database for authentication and mapping rules of user roles, based upon VLAN ID and group name. Figure 7-15. Mapping Rules with External User Authentication Server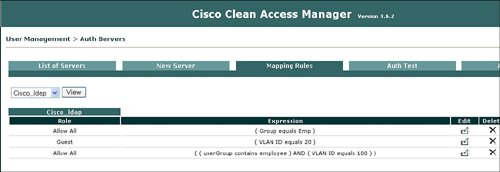 MonitoringThe NAC appliance manager provides excellent monitoring capabilities that can be used to identify what is going on in the network. With the Monitoring feature of the manager, you can display all online users with specific details, including the following:
Figure 7-16 displays a summary of the monitoring statistics, and Figure 7-17 shows the specific user characteristics or parameters that can be displayed for each online user. Figure 7-16. Monitoring Summary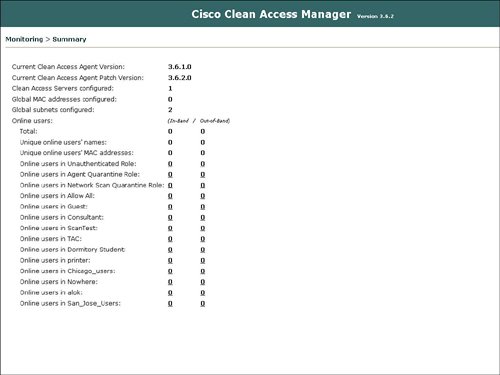 Figure 7-17. Online User Information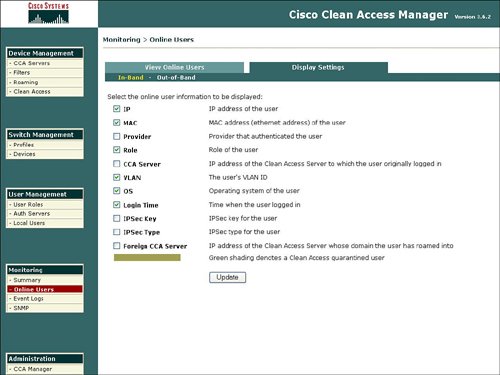 The NAC appliance manager also features the display of event logs as an option under Monitoring. Event logs can contain items including admin logon, rule creation, policy deployment, and antivirus/antispyware updates. Figure 7-18 displays a sample of events in the event log. Figure 7-18. Event Log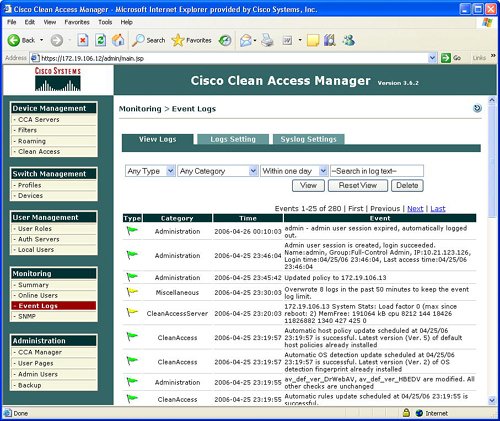 The Monitoring function also provides the ability to configure SNMP parameters. SNMP parameters that you can configure under Monitoring include community strings and threshold values. The SNMP area under Monitoring also provides the ability to download updated SNMP MIBs for the NAC appliance. Figure 7-19 displays a sample of the configurable SNMP parameters for Monitoring. Figure 7-19. SNMP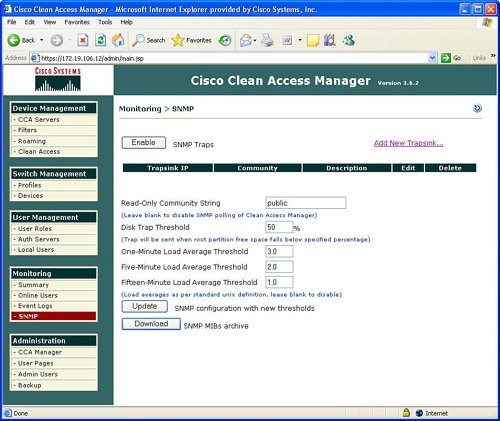 AdministrationThe NAC appliance manager also contains an Administration option in the manager GUI. The functions contained under the Administrative option include the traditional IP addressing, the manager, SSL certificates, definition of admin users, and the ability to back up the NAC appliance manager. These administrative features are not described in detail because they are conventional and not the focus of this chapter on the security features of the NAC appliance. |
EAN: 2147483647
Pages: 112