Introducing Cisco Self-Defending Networks
| Self-defending networks augment and complement the traditional network defense components outlined in the previous section. Self-defending networks differ from traditional network defenses in that self-defending networks have the capability to provide some amount of automatic protection of the network components and end-user workstations in the event of a network attack. Self-defending networks can also be implemented in layers, in a manner similar to defensive layers of a football or soccer team. The layered self-defending network includes components that can protect the network connections in the data center, at the remote or branch location, and at the desktop. Self-defending networks can either recommend a configuration or automatically apply a configuration to prevent certain network attacks. Self-defending network components include the following:
Figure 1-2 displays an example of a network diagram with self-defending components. The next sections describe the components in more detail. Figure 1-2. Self-Defending Network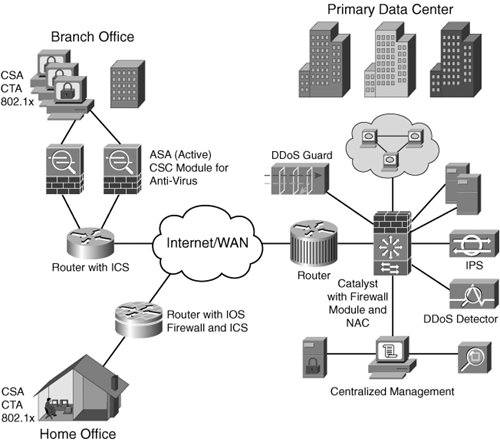 DDoS MitigationDDoS attacks can often be among the toughest to defend because they involve large amounts of what appears to be legitimate source traffic and multiple, distributed senders of this source traffic. Automatic or self-defending DDoS mitigation involves the automatic rerouting of the DDoS traffic while maintaining the valid network traffic connections. Cisco Guard and Detector appliances and Catalyst 6500/7600 DDoS service modules can provide this automatic DDoS mitigation by creating a baseline of normal network activity, detecting DDoS attacks and then automatically rerouting the DDoS traffic away from the target servers by updating the routing tables. In addition to customer-managed DDoS mitigation solutions, there are also ISP-managed DDoS mitigation or clean-pipe solutions. These ISP-managed solutions are implemented with Cisco DDoS mitigation appliances and service modules. The ISP-managed solutions often contain partner products from Arbor Networks, which complement the Cisco DDoS mitigation appliance and linecard products. Intrusion Prevention SystemsIntrusion Prevention Systems (IPSs) are the successor to IDS products. IDS operates on a copy of network traffic, from a source such as a span port on a LAN switch, so it can detect, but typically cannot prevent, an attack because the original network traffic has already propagated through the network. IPS operates inline and processes the actual network packet, not a copy of the network traffic. IPSs can detect a network attack based upon network traffic signatures or patterns of data in the network traffic. Since IPS operates inline, IPS has the ability to drop the packets of the attack and prevent a network attack rather than detect a network attack. IPS is an important part of the self-defending network, rather than a traditional network defense, since IPS has the ability to be self-defending and prevent a network attack without manual operator intervention during the attack. IPS can be implemented as a standalone IPS appliance or service module. IPS can also be implemented as an integrated component with the Adaptive Security Appliance (ASA). This book focuses on IPS as an integrated component with ASA rather than as a standalone product. Adaptive Security ApplianceASA is an integrated and extensible security appliance product line from Cisco. ASA is an integration of the PIX firewall, Network IDS/IPS system, and VPN 3000 concentrator. This ASA appliance contains many self-defending characteristics including inline IPS support, application layer inspection/enforcement, and SYN Cookie capabilities. These self-defending features can enable the ASA appliance to drop network attack connections and protect end servers and users from attacks by monitoring, inspecting, and restricting the network connection attempts to target devices. For example, the HTTP application inspection engine in ASA can inspect a specific HTTP connection flow and can drop an HTTP packet that does not conform to the proper packet format. The ASA IPS engine also allows specific IPS signatures to be applied to specific traffic flows. The inline IPS signature engine in ASA can be configured to automatically drop any packets in the traffic flow that match the IPS signature. The SYN Cookie feature in ASA can prevent a TCP connection attack against a host by creating a cookie for each TCP connection request. This cookie can be used to protect the host by preventing the host from allocating a buffer for each TCP connection attempt. Features like SYN Cookie can be very powerful self-defending mechanisms since many host computers can be crashed or compromised when they run out of buffer spaces like the ones used for each TCP connection. Incident Control ServiceCisco also offers the ability to contain a worm infection within the network. The Cisco Incident Control Service (ICS) is developed in partnership with Trend Micro. The Cisco ICS provides automatic updates of new vulnerability updates from Trend Micro. The Cisco ICS also provides the ability to automatically update these Outbreak Prevention Signatures on ASA, IOS router, and IPS platforms. In addition to Outbreak Prevention Signature update, Cisco ICS also provides Outbreak Prevention ACL (access list) updates, which can recommend or automatically apply a new ACL to an IOS router or ASA device in the event that a network infection has been identified to the Cisco ICS. Network Admission ControlNetwork Admission Control (NAC) can help to create a self-defending network by preventing a rouge or vulnerable user from entering the network, thus reducing the attack risk before the user enters the network. NAC allows network components to check the operating system (OS) service pack (SP) updates, antivirus updates, and Cisco Security Agent (CSA) updates before the user is granted access to the network. Any down-level or at-risk users are quarantined to a safe part of the network until they can be remediated or upgraded with the proper OS, antivirus, or CSA updates required to safely participate on the network. NAC components can be embedded directly into the framework of routers and switches, or NAC components can be deployed as dedicated, standalone appliances. The NAC components that are embedded directly in routers and switches require client or agent software on the user computer. This client is known as Cisco Trust Agent (CTA). The standalone NAC framework solution supports an optional software client or agent for the end-station. Both the framework and appliance NAC solution support an audit mode for agentless devices. Audit mode allows information to be gathered about unknown endpoints without an agent and to be used to influence the amount of network access that is granted to these agentless machines. The NAC appliance also leverages an integrated scanner. The scanner probes the network to identify hosts and information about hosts including IP address and OS. In addition to being a dedicated standalone solution, the NAC appliances also do not require IEEE 802.1x authentication. IEEE 802.1xIEEE 802.1x is a standard for machine authentication and user authentication. IEEE 802.1x is widely deployed today in wireless LAN environments and can leverage a supplicant that resides on the end-device or host. Cisco's embedded NAC framework solution can leverage IEEE 802.1x to provide the basic authentication prior to more advanced authentication including OS SP patches, antivirus patches, and CSA updates. Cisco's framework NAC solution leverages a unique end-device supplicant, the Cisco Trust Agent (CTA), to provide the advanced authentication features. CTA includes a base 802.1x supplicant. Many people are confused about exactly what 802.1x is. Chapter 5, "Demystifying 802.1x," reduces the confusion about 802.1x and identity management. Host Intrusion Prevention: CSACSA provides host intrusion protection for users or hosts on the network. CSA can be considered the last line of the layered self-defending network defense because CSA can prevent malicious behavior on a host, including attacks such as buffer overflow. CSA can be automatically and centrally updated with new policies to help protect against new network attacks. CSA is end-device or host software that monitors the behavior and critical resources of the end-device or host. CSA also contains an option that can implement a personal firewall service. CSA provides "day-zero" protection, which is a fancy way of saying that it can protect against certain attacks before the attack is known. CSA does not require signatures like legacy Host Intrusion Prevention and antivirus products. CSA provides this day-zero protection capability by detecting the symptoms of an attack, rather than the unique identifier of the attack. For example, CSA can prevent the modification of registry keys and can detect a buffer overflow. The ability to detect and prevent the symptom of an attack enables CSA to protect against certain attacks prior to the identification and naming of the attack. Cisco Security Centralized ManagementA good defense is typically a layered defense. This layered defense can be composed of router access lists and firewall service modules to protect the core network and data center, ASA to protect DMZs and the perimeter, NAC to provide secure network access at the perimeter, and CSAs to protect the server, workstations, and laptops. This defense is similar to that of a football team, starting with the front line to protect the servers, all the way to the safeties, or CSAs, as a last line of defense on the workstation or desktop. Like any layered defense, it is imperative to provide coordination and integration among the different layers of defense. This coordination, or coaching, can be implemented in an integrated fashion with centralized management products. Cisco Security Centralized management can be divided into two main functional areas:
Components from each of these functional areas are marketed under the Cisco Security Management product suite. The Cisco Security product for centralized configuration is the Cisco Security Manager (CS-Manager), and the centralized monitoring product is the Cisco Security Monitoring, Analysis, and Response System (CS-MARS). Centralized configuration management products, like the Cisco Security Manager, enable hundreds or thousands of routers and security appliances to be configured with a consistent or coordinated security policy. Centralized monitoring products, like the Cisco Security MARS, receive monitoring events like syslog, SNMP Traps, IPS Secure Device Event Exchange (SDEE), and Remote Data Exchange Protocol (RDEP) events and can create an end-to-end picture of what is happening in the network based upon the monitoring events from the devices in the network. The Cisco centralized monitoring Cisco Security MARS product also adds a response or self-defending feature where Cisco Security MARS can create a recommendation on how to stop a network attack as well as enable IPS signatures on IOS routers with the Distributed Threat Mitigation (DTM) feature. Cisco Security MARS also includes support for NetFlow to establish a baseline of what network traffic should look like prior to a potential network attack. Network traffic that is far in excess of this baseline can be used to determine that the network is under an attack. |
EAN: 2147483647
Pages: 112