Deploying an AAA Infrastructure
Once you have made the VPN server name resolvable on the Internet, you want to make sure that only users you approve of can gain access to the VPN services. The next step, therefore, is to deploy your identification systems, otherwise known as AAA services. Deploying the AAA infrastructure for remote-access VPN connections consists of the following:
-
Configure Active Directory for user accounts and groups.
-
Configure the primary IAS server computer.
-
Configure IAS with RADIUS Clients
-
Configure a VPN remote access policy with Windows Server 2003 IAS
-
Configure the secondary IAS server computer.
Configuring Active Directory for User Accounts and Groups
Active Directory is the center of your VPN security.
To configure Active Directory for user accounts and groups
-
Ensure that all users making remote access connections have a corresponding user account. This includes employees, contractors, vendors, and business partners.
-
Set the remote access permission on user accounts to Allow Access or Deny Access to manage remote access by user. Or, to manage remote access by group, set the remote access permission on user accounts to Control Access Through Remote Access Policy.
-
Organize remote access users into the appropriate universal and nested groups to take advantage of group-based remote access policies.
Configuring the Primary IAS Server Computer
IAS servers will allow you to handle all communications related to authentication and authorization by leveraging Active Directory. This capability is essential when you will have several points of presence to authenticate from. Along with considering the scenario of multiple VPN server sites, think about using IAS for the authentication of extranets, internal resources, and wireless networks. Because this will be a vital server resource and the loss of authentication services can stop an entire network from operating, it is always essential to specify a primary and secondary IAS server for redundancy.
To install IAS on the primary IAS server computer
-
Open Add Or Remove Programs in Control Panel.
-
Click Add/Remove Windows Components.
-
In the Windows Components Wizard dialog box, double-click Networking Services under Components.
-
In the Networking Services dialog box, select Internet Authentication Service. The resulting Networking Services window is shown in the following figure.
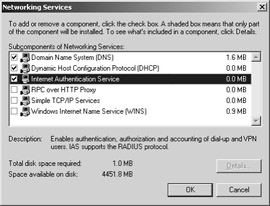
-
Click OK, and then click Next.
-
If prompted, insert your Windows product compact disc.
-
After IAS is installed, click Finish and then click Close.
The primary IAS server computer must be able to access account properties in the appropriate domains. If IAS is being installed on a domain controller, no additional configuration is required for IAS to access account properties in the domain to which it belongs. If IAS is not installed on a domain controller, you must configure the primary IAS server computer to read the properties of user accounts in the domain. You can do this by following the procedure described below.
To configure the primary IAS server computer to read the properties of user accounts in the domain
-
Click Start, point to Programs, point to Administrative Tools, and then click Internet Authentication Service.
-
In the console tree, right-click Internet Authentication Service (Local) and then click Register Server In Active Directory.
A Register Internet Authentication Server In Active Directory dialog box appears.
-
Click OK.
Alternatively, you can perform one of the following actions:
-
Use the netsh ras add registeredserver command.
-
Or add the computer account of the IAS server to the RAS And IAS Servers security group with the Active Directory Users And Computers snap-in.
If the IAS server authenticates and authorizes VPN connection attempts for user accounts in other domains, verify that the other domains have a two-way trust with the domain in which the IAS server computer is a member. Next, configure the IAS server computer to read the properties of user accounts in other domains by using the netsh ras add registeredserver command or the Active Directory Users And Computers snap-in.
If there are accounts in other domains and the domains do not have a two-way trust with the domain in which the IAS server computer is a member, you must configure a RADIUS proxy between the two untrusted domains. If there are accounts in other untrusted Active Directory forests, you must configure a RADIUS proxy between the forests. The good news is that IAS is also a RADIUS server and can do RADIUS proxy services as well. See IAS help in Help and Support Center for Windows Server 2003 for details on how to set up a complete RADIUS solution using IAS.
If you want to store authentication and accounting information for connection analysis and security investigation, enable logging for accounting and authentication events. Windows Server 2003 IAS can log information to a local file and to a structured query language (SQL) Server database using the new SQL-Extended Markup Language (SQL-XML) logging features. This facility allows for centralized auditing and logging of the corporation’s security services—a very useful tool with multiple points of access to control logging and to generate reports.
To enable and configure local file logging for Windows Server 2003 IAS
-
In the console tree of the Internet Authentication Service snap-in, click Remote Access Logging.
-
In the details pane, double-click Local File.
-
On the Settings tab, select one or more check boxes for recording authentication and accounting requests in the IAS log files:
-
To capture accounting requests and responses, select the Accounting Requests check box.
-
To capture authentication requests, access-accept packets, and access- reject packets, select the Authentication Requests check box.
-
To capture periodic status updates, such as interim accounting requests, select the Periodic Status check box.
-
-
On the Log File tab, type the log file directory as needed and select the log file format and new log time period.
To enable and configure SQL Server database logging for Windows Server 2003 IAS
-
In the console tree of the Internet Authentication snap-in, click Remote Access Logging.
-
In the details pane, double-click SQL Server.
-
On the Settings tab, select one or more check boxes for recording authentication and accounting requests in the IAS log files:
-
To capture accounting requests and responses, select the Accounting Requests check box.
-
To capture authentication requests, access-accept packets, and access- reject packets, select the Authentication Requests check box.
-
To capture periodic status updates, such as interim accounting requests, select the Periodic Status check box.
-
-
In Maximum Number Of Concurrent Sessions, type the maximum number of simultaneous sessions that IAS can create with the SQL server.
-
To configure an SQL data source, click Configure.
-
In the Data Link Properties dialog box, configure the appropriate settings for the SQL Server database.
Some configurations also need to take place on the SQL server for this process to operate. See the IAS help in Help and Support Center for Windows Server 2003 for information about the steps to set up the SQL server to accept IAS logs.
Configuring IAS with RADIUS Clients
You must configure the primary IAS server with the VPN servers as RADIUS clients. This configuration will allow both the primary and secondary IAS servers to access external RADIUS services to authenticate users.
To add a RADIUS client for Windows Server 2003 IAS
-
Right-click RADIUS Clients, and then click New RADIUS Client.
-
On the Name And Address page, type a name for the VPN server in Friendly Name. In Client Address (IP Or DNS), type the IP address or DNS domain name. If you type a DNS domain name, click Verify to resolve the name to the correct IP address for the VPN server.
-
Click Next.
-
On the Additional Information page, type the shared secret for this combination of IAS server and VPN server in Shared Secret, and then type it again in Confirm Shared Secret.
-
Click Finish.
Don’t take chances with your security systems! To ensure the maximum security for RADIUS messages that contain username and password information as well as extensive identification parameters, you need to use IPSec with certificate authentication and Encapsulating Security Payload (ESP). Doing this will provide data confidentiality, data integrity, and data origin authentication for RADIUS traffic sent between the IAS servers and the VPN servers. Windows 2000 Server and Windows Server 2003 support IPSec, set up an IPSec policy between the IAS and VPN servers. Also, set up an IPSec policy between the IAS and external RADIUS servers.
Configuring a VPN Remote Access Policy with Windows Server 2003 IAS
The VPN remote access policy will enable the extra security required for users coming into the network from an external network. It will define who is allowed to access the system and how they are allowed to access it. For instance, if you want remote users to access the VPN servers only if they are using L2TP/IPSec as a tunneling protocol or only if they are using EAP-TLS as an authentication protocol, the Remote Access Policy defines the parameters that they are allowed to use to connect.
To create a remote access policy for VPN remote access for Windows Server 2003 IAS
-
From the console tree of the Internet Authentication Service snap-in, right- click Remote Access Policies and then click New Remote Access Policy.
-
On the Welcome To The New Remote Access Policy Wizard page, click Next.
-
On the Policy Configuration Method page, type the name of the policy in Policy Name.
-
Click Next.
-
On the Access Method page, select VPN.
-
Click Next.
-
On the User Or Group Access page, select Group.
-
Click Add.
-
In the Select Groups dialog box, type the name of your universal or global VPN remote access group in Enter The Object Names To Select.
-
Click OK. Your VPN remote access group is added to the list of groups on the User Or Group Access page.
-
Click Next. On the Authentication Methods page, select the authentication methods you want your VPN remote access clients to use.
-
To enable EAP-TLS authentication, select Extensible Authentication Protocol (EAP), then Smart Card Or Other Certificate in Type. Then click Configure. In the Smart Card Or Other Certificate Properties dialog box, ensure that the name of the computer certificate installed on the IAS server is visible in Certificate Issued. If multiple computer certificates are installed on the IAS server, select the correct one in Certificate Issued.
If you cannot select the certificate, the cryptographic service provider for the certificate does not support SChannel, which is the industry-standard interoperable template for integrating third party certificates to standard CSPs. SChannel support is required for IAS to use the certificate for EAP-TLS authentication.
-
Click OK.
-
When using PPTP, on the Policy Encryption Level page, clear the encryption levels you do not want to use. For example, to use 128-bit Microsoft Point-to-Point Encryption (MPPE), clear the Basic Encryption and Strong Encryption check boxes.
-
Click Next, and go to step 18.
-
When using L2TP/IPSec, on the Policy Encryption Level page, clear the encryption levels you do not want to use. For example, to use Triple Data Encryption Standard (3DES), clear the Basic Encryption and Strong Encryption check boxes.
-
Click Next.
-
On the Completing The New Remote Access Policy Wizard page, click Finish.
Using Network Access Quarantine Control will allow you to check the user’s remote configuration for mandatory compliance with the organization’s configurations for virus checking, group policy, firewall usage, and so forth. If you are using Network Access Quarantine Control, you can use the MS-Quarantine-IPFilter vendor-specific attribute (VSA) or the MS-Quarantine-Session-Timeout VSA to specify quarantine settings. Both of these VSAs are configured from the Advanced tab in the profile properties of the remote access policy that you create for remote access connections.
You can use the MS-Quarantine-IPFilter attribute to configure input and output packet filters to allow only the following:
-
The traffic generated by the remote access client notifier component. If you are using Rqc.exe (from the Windows Server 2003 Resource Kit) and its default port, configure a single input packet filter to allow only traffic from Transmission Control Protocol (TCP) port 7250 and to TCP port 7250.
-
The traffic needed to access the quarantine resources. This includes filters that allow the remote access client to access name resolution servers (such as DNS), file shares, or Web sites to allow the user to get a client computer up to organization policies. For instance, if one of the organization’s mandatory policies is to have the most current virus signature files, the IPFilters can allow the user access to a store where she can grab the new signature file. Give users just enough access to get up to compliance in quarantine mode. One way to simplify quarantine resources is to set up a separate quarantine subnet with all the resources required and not allow access to any internal resources until remote access client pass their quarantine tests.
More Info The Windows Server 2003 Resource Kit tools are currently available at http://www.microsoft.com/windowsserver2003/techinfo/reskit/resourcekit.mspx.
You can use the MS-Quarantine-Session-Timeout attribute to specify how long the remote access server must wait to receive the notification that the script has run successfully before terminating the connection. Specifying a timeout length in this way makes sure that malicious users will not have an unlimited amount of time to meet the quarantine standards required to satisfy the organization’s policy. Another point to make here is to make sure to limit quarantine checks to a fast process. If your required quarantine checks take more than 30 seconds, the user experience is diminished and unsavvy users might perceive quarantine as a failure to connect and keep trying to disconnect and reconnect—thus never actually passing quarantine! The rule of quarantine is to keep it simple but comprehensive. You can make the preconnect quarantine action a customized experience. For instance, Microsoft tells its users what it is checking and shows a progress bar during quarantine—that way users know that things are happening and are not left wondering whether or not they are getting hooked up.
Because the quarantine VSAs can limit network access and automatically disconnect remote access users, you should configure these attributes only after a quarantine Connection Manager (CM) package has been distributed and installed on the remote access client computers of your organization.
For more information about Network Access Quarantine Control, see Chapter 5.
Configuring the Secondary IAS Server Computer
Now it is time to apply redundancy to the authentication systems of the VPN services. To configure the secondary IAS server computer, follow the instructions described in the Configuring the Primary IAS Server Computer section, specifically the instructions regarding installing IAS and registering the IAS server computer in the appropriate domains.
Next, copy the configuration of the primary IAS server to the secondary IAS server by using the following steps:
-
On the primary IAS server computer, type netsh aaaa show config > path\file.txt at a command prompt, which stores the configuration settings, including registry settings, in a text file. The path can be a relative, absolute, or network path.
-
Copy the file created in step 1 to the secondary IAS server.
-
On the secondary IAS server computer, type netsh exec path\file.txt at a command prompt, which imports all the settings configured on the primary IAS server into the secondary IAS server.
Best Practices If you change the IAS server configuration in any way, use the Internet Authentication Service snap-in to change the configuration of the IAS server that is designated as the primary configuration server and then use the previous procedure to synchronize those changes on the secondary IAS server.
EAN: 2147483647
Pages: 128