| E-mail and other forms of online messaging are terrific communication tools that let you exchange information with coworkers and clients, transmit files and pictures, and stay in touch with friends and family. But always be careful about what mail you open, especially if there are attachments or inserted graphics, and what information you send out. To help promote your safety, many e-mail providers will strip out attachments and graphics when they cannot verify the legitimacy of the attachments. Taking the First Steps So what can you do about spam? Here are four steps that can help to protect you from the negative effects of spam: First, set your e-mail service's spam filters to a high setting (review the settings to find what works best for you). You'll then need to check your junk e-mail folder periodically to see if a potentially legitimate e-mail message was somehow blocked. If it was, you might want to add the legitimate e-mail address to your list of approved senders to avoid this in the future. Your e-mail provider can give you instructions on how to do this if you are unsure. Second, never respond to a spam message. While it may be very tempting to respond to the spammer, if only to complain about the mail, it will likely not work. The e-mail account you send it to will rarely ever be legitimate, and you will have validated that your e mail account is in fact legitimate and active, which can increase the amount of spam you get. Third, report spam to your e-mail provider. There should be an easy-to-find way for you to report spam in your e-mail inbox. The more you report, the better the spam filters will become at determining what should be blocked. You'll do yourself and hundreds of millions of other users a favor by reporting spam. Fourth, never buy something offered through a spam message. If no one purchased through this mechanism or was fooled by the scams that spam so often veils in get-rich-quick offers or phishing schemes, spam would not be lucrative and it would subside. Figure 10-1 on the next page shows an example of classic "storefront" spam. Figure 10-1. A typical spam message 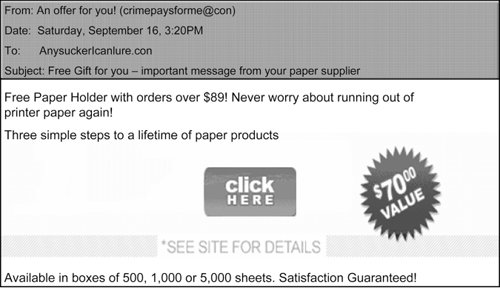
You help perpetuate the problem when you respond to this type of e mail and make it financially rewarding for these cybercriminals to operate. You also run a very high risk of exposing your personal and financial information. Think About It It's important that you understand the protective services that your e-mail provider makes available to you. Microsoft e-mail products, for example, provide spam filtering and automatic attachment scanning for viruses and malware.
Avoiding Incoming Threats Just as you toss away several pieces of unwanted paper mail every day, you also need to weed through e-mail to get rid of unwanted or potentially malicious messages. Here are some guidelines to help you swim through the sea of spam without sinking: No reputable company should send you e-mail telling you to follow a link to validate your account or personal information. If you get this kind of e-mail, it is surely an attempt at fraud. If you're ever in doubt or have any questions, call the number on your credit card or account statement. Do not call any number that might appear in that e-mail message, and notify the bank about the mail you received. Don't fall for flattery. Another angle for spam and stalkers is to flatter and express interest in you (see Figure 10-2). They leave the reference to when they met you vague and often send a photo of an attractive girl or guy, depending on who they are targeting. If you provide more information, agree to meet them, or open any attachment, you could fall victim to a scheme. Figure 10-2. Don't be taken advantage of by false flattery. 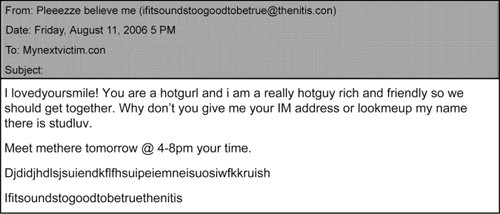 Avoid clicking on links that are sent in e-mail. It is better to type the address into your browser yourself than to follow a link, or look up the company in a search engine and use that link to get to the site. If you must follow e-mail links, verify that the link takes you to where it says it does, and be very cautious about what information you enter. People can name a link anything, but where it actually takes you is another story. Remember that a destination URL can be cleverly disguised to look like another site. Consider using a secondary e-mail address as the address you provide for an online classified ad or to online dating contacts, for example. Until you can trust someone, don't expose your primary e-mail account address. If you want to unsubscribe from the e-mail sent to you from legitimate companies, you do need to use the unsubscribe functionality found at the bottom of their e-mail or go to the company's Web site and find their unsubscribe process.
Remember, if you stick to personal or business communications in e-mail and verify each sender, you are likely to stay safe. Respond to any sales pitch, get-rich-quick messages, account validation requests, or would-be admirers and you're taking a risk with both your finances and your identity. |

