UTILITIES AND SETTINGS
Windows NT offers utilities and tools for such tasks as formatting hard drives and assigning drive letters to volumes; monitoring and logging the performance of workstation or server computers; viewing system, security, and application event logs; and backing up critical information. Some of the more commonly used tools and their functions are described next. All the following tools are located in the Administrative Tools [Common] area, which can be accessed by selecting Start > Programs > Administrative Tools [Common].
Backup
Windows NT comes with a built-in backup tool known as Backup. Backup provides the ability to back up and restore important system files and data. When Backup is first run, it attempts to find a tape drive unit attached to the system. If Backup does not find a tape drive unit attached to the system, a Tape Drive Error Detected window appears that suggests you check to see that the proper cables are connected, power to an attached tape unit is turned on, and that you have properly configured a tape unit using the Tape Devices option in Control Panel.
Once you enter the Backup main window, you can use the Operations drop-down menu to backup, restore, and perform general backup tape maintenance functions.
Most organizations today utilize third-party backup software that offers more functionality than the Windows NT Backup tool.
Disk Administrator
The Windows NT Disk Administrator is a very useful administrative tool that lets you format drive space, assign and change drive labels, and implement fault-tolerant systems by establishing disk mirror sets and disk stripe sets.
Disk Administrator is located in the Administrative Tools [Common] area. Once you open the Disk Administrator, the window shown in Figure 25.6 appears.
From the Partition drop-down menu, you can delete, create, or extend partitions and create volume sets or stripe sets. From the Tools drop-down menu, you can format a displayed drive or volume, assign a drive letter to a disk or volume, or display the properties of a drive.
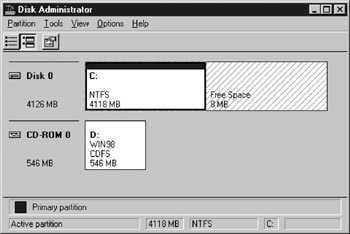
Figure 25.6: Windows NT Disk Administrator.
Explaining every function of the Windows NT Disk Administrator is beyond the scope of this book; however, it is important for you to understand the terms mentioned here for the A+ Operating Systems Technologies test.
Fault Tolerance and Raid
Fault tolerance is the ability of a computer system to recover from a hardware or software failure or crash. There are several types of fault-tolerant hard disk configurations and specifications known as RAID levels.
Several levels of RAID are available today that provide fault-tolerant systems. It is important that you have a basic understanding of the following three levels of RAID.
RAID level 0, or disk striping without parity: With this level of RAID, data is spread or written over multiple hard disks. This technique provides better performance of read-and-write operations than other levels of RAID, but it is not considered fault tolerant.
RAID level 1, disk mirroring, or disk duplexing: To use RAID level 1 and establish what is called a disk mirror with the Windows NT Disk Administrator, you need two installed hard drives. After you have established a mirror within Windows NT Disk Administrator, all data written to your first hard drive is also written to the second hard drive. This provides true fault tolerance. If one of your hard drives fails, the other drive can be used to recover data. With disk mirroring, only one hard drive controller card is used to support both hard drives. Disk duplexing is the same as disk mirroring, with one exception: a second hard drive controller card is used; therefore disk duplexing is more fault tolerant than disk mirroring.
RAID level 5, otherwise known as disk striping with parity: RAID level 5 is one of the most widely used fault-tolerant implementations. This RAID level requires a minimum of three hard drives installed in a single system and can support up to 32 hard drives. With RAID level 5, all information and parity data are spread across the disks. If one disk crashes, the information needed to implement a complete recovery by the system can be gathered from the other two disks.
If you encounter a question on the OS exam that asks which Windows NT built-in administrative tool can be used to format a drive, change a drive letter assignment, or establish a fault-tolerant recovery implementation, Disk Administrator should be your answer.
Volume Sets
A combination of hard disk space from different partitions that is used to form a single logical area is known as a volume set. A volume set can combine the free drive space from up to 32 separate partitions to form one logical drive. For example, if you have three hard drives with a combined free space of 4GB, you can select each area of free space from each of the three drives displayed in the Windows NT Disk Administrator utility and combine the three areas to form one logical drive.
Event Viewer
The Windows NT Event Viewer, also located in the Administrative Tools [Common] area, is used to monitor and evaluate significant events that occur within the operating system. Event Viewer maintains three separate event logs, each of which has its own unique purpose for monitoring and troubleshooting important events.
The three main event logs that can be viewed with Event Viewer are the System Log, the Security Log, and the Application Log.
System Log: This maintains information pertaining to important system events, such as services that have been stopped or started within the operating system. Some of these services may include the Event Log service, the computer browser service, DHCP service, or any other service run by the system. The System Log also maintains useful start-up information that can be used to troubleshoot components that are attached to the system.
Security Log: As mentioned earlier in the User Manager sections, enabled events in the Audit Policy are displayed in the Security Log. The Security Log can keep a record of successful and unsuccessful logon attempts to the domain or network. It can also track file and object access, as well as system restarts and shutdowns.
Application Log: The application log keeps track of important information about system-related applications. These applications may include Microsoft Office, antivirus software, and Windows Update.
Over time, the event logs that are maintained within the Event Viewer can use up important hard drive space and cause your system to run slowly or crash. A good practice is to change the default settings from “Overwrite events older than 7 days” to “Overwrite events as needed.”
Performance Monitor
Windows NT includes an important add-on utility that can be used to track and monitor the performance of system components and the overall performance of a workstation or server computer. This tool is called the Windows NT Performance Monitor. Some of the most useful information that can be gathered and logged by performance monitor includes processor utilization, memory utilization, memory page faults per second, percentage of free disk space, and real-time server counters to keep track of important server utilization.
Windows Nt Diagnostics
Yet another very useful tool included with Windows NT is the Windows NT Diagnostics utility. This utility can be used to view and troubleshoot system resources, such as IRQs, I/O ports, DMA channels, memory, and devices. All system services as well as environmental variables can also be viewed through Windows NT Diagnostics.
The Windows NT Diagnostics utility can be accessed through the Administrative Tools [Common] area or by selecting Start > Run and entering “WINMSD” on the Open line. The Windows NT Diagnostics utility is not meant to be used for updating or changing system or environmental settings; it is simply a representation of settings and information stored in the Registry, and used for diagnostics and troubleshooting.
TCP/IP Utilities
Several important utilities are part of the TCP/IP package and are installed with Windows NT Workstation and Windows NT Server by default. These utilities are used to troubleshoot and test network connectivity issues. Following are descriptions of the most commonly used TCP/IP utilities and their functions. Note that all these utilities work in a similar manner in Windows 2000.
PING
Short for Packet Internet Groper, PING is a utility used to test the connection between two computers. The following syntax is used to PING a computer by IP address or by name:
PING 209.15.176.206 PING CHARLESRIVER.COM
The PING utility works by sending a TCP/IP packet to a destination IP address and waiting for a reply. If the destination host receives the packet of information, four echo replies are received at the computer that initiated the PING command. PING is most commonly used to test connections to the Internet and ISPs. If you want to test a particular connection to a host IP address over a period of time (persistent), you can use the PING -t command. For example, to run a persistent PING to test your connection to the Charles River Media Web site, enter the following at a command prompt:
PING -t 209.15.176.206
To stop your connection test, simply press the Ctrl+C key combination.
IPCONFIG
You should recall from Chapter 24 that the WINIPCFG command is used at a Windows 9x command prompt to display TCP/IP information, such as a system’s IP address, subnet mask, and default gateway. Windows NT and Windows 2000 utilize the TCP/IP utility IPCONFIG to display the same information. You can display a system’s IP address and additional information by navigating to a Windows NT or Windows 2000 command prompt and entering “IPCONFIG.”
The following results are from entering the IPCONFIG command at a Windows 2000 command prompt:
Windows 2000 IP Configuration Ethernet adapter Local Area Connection 3: Connection-specific DNS Suffix . : srst1.fl.home.com IP Address . . . . . . . . . . . . : 192.168.1.101 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.1
TRACERT
The TCP/IP TRACERT utility is used to troubleshoot connections between routes that a packet will take before reaching its destination address. In other words, TRACERT measures the time it takes for a packet of information to move between routers in hops until it reaches its destination. You can view the results of TRACERT and the time it takes for the packet to move between routers to see where the slow response is located. To run a TRACERT to the Charles River Media Web site, enter the following command at a command prompt:
TRACERT CHARLESRIVER.COM
The results from a system running a TRACERT to the Charles River Media Web site are displayed next. The TRACERT results end when you see “Trace complete.”
Tracing route to CHARLESRIVER.COM [209.15.176.206] over a maximum of 30 hops: 1 10 ms 10 ms 10 ms 10.101.0.1 2 20 ms 10 ms 20 ms atm5-0-953.tampflerl-rtr2.tampabay.rr.com [65.32.11.146] 3 10 ms 10 ms 10 ms srp8-0.tampflerl-rtr4.tampabay.rr.com [65.32.8.228] 4 10 ms 10 ms 10 ms pop2-tby-P0-1.atdn.net [66.185.136.185] 5 10 ms 10 ms 20 ms bb1-tby-P0-3.atdn.net [66.185.138.208] 6 30 ms 30 ms 30 ms bb2-atm-P7-0.atdn.net [66.185.152.245] 7 30 ms 30 ms 30 ms pop2-atm-P5-0.atdn.net [66.185.138.43] 8 30 ms 30 ms 30 ms level3.atdn.net [66.185.138.34] 9 30 ms 30 ms 50 ms so-4-1-0.bbr2.Atlanta1.level3.net [209.247.9.169] 10 40 ms 50 ms 50 ms so-0-0-0.bbr1.Washington1.level3.net [64.159.1.2] 11 40 ms 51 ms 50 ms so-6-0-0.edge1.Washington1.Level3.net [209.244.11.10] 12 40 ms 70 ms 60 ms qwest-level3-oc48.Washington1.Level3.net [209.244.219.182] 13 40 ms 41 ms 50 ms dca-core-03.inet.qwest.net [205.171.209.113] 14 40 ms 50 ms 41 ms dca-core-02.inet.qwest.net [205.171.9.49] 15 60 ms 70 ms 60 ms atl-core-02.inet.qwest.net [205.171.8.153] 16 60 ms 60 ms 60 ms atl-core-01.inet.qwest.net [205.171.21.149] 17 51 ms 60 ms 80 ms atx-edge-01.inet.qwest.net [205.171.221.18] 18 70 ms 61 ms 60 ms genesis2net.net-gw.qwest.net [63.237.0.30] 19 50 ms 60 ms 60 ms 64.224.0.72 20 50 ms 61 ms 60 ms charlesriver.com [209.15.176.206] Trace complete.
The output, or ‘results’ of using PING, IPCONFIG, or TRACERT can be directed to a text file for future reference, documentation, and further troubleshooting purposes. To direct the results of any of these utilities to a text file, simply add the greater than sign (>) followed by any name you choose to the end of the command. For example, to direct the results of a persistent PING to CHARLESRIVER.COM to a text file named publisher, enter the following command at a command prompt:
PING -t CHARLESRIVER.COM >publisher
To view the results in the text file named publisher, navigate to C:\ and edit the file named publisher. You can also view these results by opening the text file “publisher” using Notepad in Windows.
NSLOOKUP
NSLOOKUP is used to query a DNS for a host name to IP address resolution. In simple terms, when the NSLOOKUP command is given, a request is issued to resolve a fully qualified domain name, such as CompTIA.com, to an IP address.
From a command prompt, enter “NSLOOKUP CompTIA.COM”. The results of this command would be:
Name: Comptia.com Address: 216.219.103.72
Telnet
Telnet is a TCP/IP terminal emulation program/protocol that allows a user to access another system by entering the command “telnet” at a command prompt followed by a valid host name. For example, if you wanted to access a program or directory on a computer named joeshmo.edu, you would enter the following command at a command prompt:
telnet joeshmo.edu
You would then be welcomed and challenged for a user name and password. If you enter the proper credentials, you will be able to access information as a normal user of the system named joshmo.edu.
For an excellent and detailed description of how the Telnet protocol really works, visit the following www2.rad.com Web site: http://www2.rad.com/networks/1997/telnet/proj.htm#INTRODUCTION.
EAN: 2147483647
Pages: 390