Section 9.2. A Picture Is Worth a Thousand Words
9.2. A Picture Is Worth a Thousand WordsOne of the most compelling reasons for exploring the use of a graphical password scheme stems from the fact that humans seem to possess a remarkable ability for recalling pictures, whether they are line drawings or real objects. The so-called picture effectthe effect of pictorial and object representations on a variety of measures of learning and memoryhas been studied for decades.[7], [8], [9], [10], [11], [12] For the most part, cognitive scientists and psychologists have shown that there is a substantial improvement of performance in recall and recognition with pictorial representations of to-be-remembered material over verbal representations.
The picture effect has itself been the focus of numerous debates related to perception, and the most prevalent theory in its support is known as the dual-code theory, which postulates that language and knowledge of worlds are represented in functionally distinct verbal and nonverbal memory systems. Examples of dual process theory can be found in experiences that we have all had at some time or another: we meet someone, know them to be familiar, but do not know who they are; we recognize a melody, but fail to remember its name or when or where we heard it before; we read a line of a poem, know it, but do not know where we have read it before, much less the title or author of the poem. In all these cases, we experience a sense of familiarity, but we have, at least at first, no access to any contextual information.[13], [14]
Whatever the underlying reason, our ability to recall images may lend itself naturally to building robust human authentication and key generation technologies. In fact, much of the work that we see today on graphical passwords is motivated in part by the scientific literature in psychology and perception. Although we do not provide a complete survey of proposed schemes here, the following subsections present a set of representative examples in the three main areas: image recognition, tapping or drawing, and image interpretation. 9.2.1. Image RecognitionThe most widely explored paradigm for graphical passwords is that of image recognitionthat is, the user enters her "password" by recognizing the images that comprise it from among many more images. These images might be those of persons, everyday objects, or abstract images such as those in Figure 9-1, showing illustrative examples of "random art" which has been proposed for use in graphical password schemes based on image recognition.[15] A typical presentation of the interface would be to place a panel of several images in front of the user, from which the user would select one or more that she recognizes as being part of her password. After this, other panels may be placed in front of the user, for selection of additional images. In some cases, multiple images from a single panel can be selected, and in some schemes, the password includes the order in which the images are selected.
Figure 9-1. Illustrative examples of "random art," which has been proposed for use in graphical password schemes based on image recognition Generally, a scheme based on image recognition requires that the images within each panel be the same each time the panel is presented. Because the password images must always be present, doing otherwise would permit an attacker who is interacting with the system to determine those images in the password as those that appear repeatedly in the panel. In addition, it is commonplace for these schemes to present the (same) panel images permuted in a random fashion each time so that the user chooses images based on the image itself, as opposed to the position the image occupies in the panel. Because of the limited size of the password space in image recognition schemes, these systems are generally not suitable for key generation; an automated search would easily exhaust the space of possible passwords. Thus, they are generally used only for authentication, and then only when there is an online reference monitor that can stop an automated search. This is commonplace with short text passwords (e.g., PINs) as well, where an account might "lock out" after five incorrect password guesses, for example. Whether such a graphical password scheme is sufficiently secure depends on a number of factors. Later in this chapter, we give an example of two graphical password schemes that allow users to select their passwords, and show that the type of images can have a significant effect on security. 9.2.2. Tapping or DrawingOther techniques that have been explored regarding the design of graphical password schemes include displaying a reference image and asking the user to utilize a mouse or stylus to draw or click in reference to the object. In these schemes, the object is placed to provide the user a reference point for placing her drawing or clicks so that her input will be repeatable. For example, Blonder proposes a scheme in which a figure (e.g., a face) is displayed to the user, and the user is asked to click in various "tap regions" (e.g., the left ear), possibly in a particular order.[16] The sequence of tap regions constitutes the password. Jermyn et al. propose an approach, called "Draw-a-Secret" or DAS , in which they utilize merely a grid as the reference object.[17] Then, the user is asked to draw free-form on the grid, as shown in Figure 9-2. The sequence of line crossings on the grid constitutes the password in this scheme.
Jermyn et al. performed an analysis that suggests that the space of passwords in the DAS scheme, as well as the entropy of "memorable" such passwords, will be sufficiently large to enable the use of DAS for key generation. Such a claim can only be evaluated with substantial user studies, which to our knowledge have not yet been performed. However, recent analysis suggests that the scheme may not be as secure in this sense as initially thought (see the later discussion). 9.2.3. Image InterpretationRecently, Stubblefield and Simon have proposed a graphical password scheme based on the notion of image interpretation.[18] In this scheme, a series of n inkblots are generated
Figure 9-2. An example password in DAS; in DAS, a password is the sequence of line crossings made by the user's drawing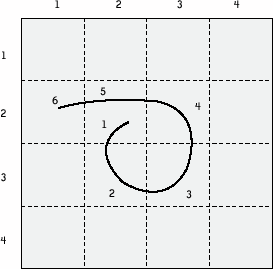 and displayed one at a time. For each image, the user forms a word association and enters it via the keyboard. For example, for the inkblot in Figure 9-3, she might enter "batman." After each word association is entered, the next inkblot in the series is displayed, and the final password is derived from the wordsfor example, concatenating the first and last letters of each word. This scheme presumes that words prompted by inkblot-like images are easier to recall than passwords recalled without such prompting, and moreover, that there is significant entropy in the word associations ascribed by users, even for the same set of inkblots. In fact, the authors believe that this entropy is sufficiently high that this scheme might be useful for key generation, not only for authentication. Again, such claims can only be adequately evaluated with sufficiently large user trials, but unfortunately, no such studies on this scheme have been conducted to date. Figure 9-3. An example inkblot; the password is derived from word associations made for each inkblot in a series of images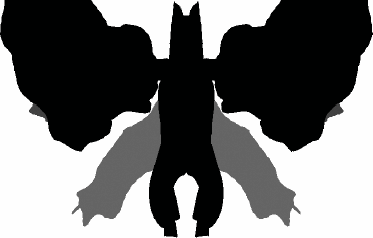 |
EAN: 2147483647
Pages: 295