| The next step is to install ACID or create a web interface that displays all alerts generated by Snort. Remember to download the latest version of ACID from its homepage, http://acidlab.sourceforge.net. You also need the programs ADODB and phplot. If you have ACID Version 0.9.6b22 or higher, use JpGraph instead of phplot. Try both to see which version works best.  | Be aware that ACID is not a very secure web program. Although this chapter does explain how to set up password protection and although the register globals option is disabled, ACID may still be easy to crack. Use caution as to what machines are running ACID and to whom the pages are accessible. Keep ACID pages internal and limited to select users. It's a good idea to locate the ACID console server on the management network. |
|
The examples presented here are what work for me. More HowTos and FAQs appear on the Internet each week, explaining new methods of installing ACID or configuring Snort. There are plenty of papers and tutorials online. If you have not already installed it, the latest version of GD is also required by the system. You may opt to use the GD library that is included with the PHP source code instead. After downloading all the necessary files, place the source code in the root directory of your web server. If you are using Apache as described previously, all files are placed in the /usr/local/httpd/htdocs/ directory. If you are using the default Apache that came with Red Hat Linux, place the compressed files in /var/www/html/. Copy all additional program files to the web root directory. Update the version numbers to the most recent releases. These examples are current as of this writing. # cp acid-0.9.6b23.tar.gz /usr/local/httpd/htdocs/ # cp adodb360.tgz /usr/local/httpd/htdocs/ # cp jpgraph-1.12.1.tar.gz /usr/local/httpd/htdocs/ # cp phplot-4.4.6.tar.gz /usr/local/httpd/htdocs/ # cp gd-2.0.12.tar.gz /usr/local/httpd/htdocs/
Uncompress the transplanted files within the web root directory. # cd /usr/local/httpd/htdocs/ # gunzip -c acid-0.9.23.tar.gz | tar xvf - # gunzip -c adodb360.tgz | tar xvf - # gunzip -c jpgraph-1.12.1.tar.gz | tar xvf - # gunzip -c phplot-4.4.6.tar.gz | tar xvf - # gunzip -c gd-2.0.12.tar.gz | tar xvf -
Some of the directories require renaming along with a shuffling of files. # cd jpgraph-1.12.1/src/ # mkdir /usr/local/httpd/htdocs/jpgraph # cp -R * /usr/local/httpd/htdocs/jpgraph/ # cd /usr/local/httpd/htdocs/ # rm -rf jpgraph-1.12.1/ # mv gd-2.0.12/ gd/ # mv phplot-4.4.6/ phplot/
Be sure to remove the version number from those directories as specified. Normally, only the gd/ and phplot/ directories require this. 10.2.1 Confirming GD Support If you think everything installed correctly, you can skip this step. It is intended more as a troubleshooting section for those who may not have installed GD properly or who want to be certain that they can generate images on-the-fly from within their ACID web page. You might want to confirm that GD support is enabled on your system in the event you are using phplot for ACID Versions 0.9.6b9-0.9.6b21. To do this, first make certain that all the directories in the Apache root directory are owned by the default webuser or nobody or whatever user you chose to own the Apache web processes. # cd /usr/local/httpd/htdocs/ # chown -R webuser.webuser *
Run the following commands within the gd/ directory if you are using the GD libraries compiled from source: # ./configure ; make ; make install
If you are using JpGraph, make certain it recognizes your current GD installation. Use a local URL such as the following to confirm this: - http://<youracidhost>/jpgraph/utils/misc/chkgd.php
You should get a notification back saying: "You have GD 2 installed. Version 2.0 (or higher)." Check to see if PHP can generate graphical images. First, create a /tmp/jpgraph_cache directory and then change ownership of the directory to the default webuser. # mkdir /tmp/jpgraph_cache/ # chown -R webuser.webuser /tmp/jpgraph_cache/
Open the URL to verify that your images were generated correctly. - http://<youracidhost>/jpgraph/utils/misc/gencolorchart.php
You should be able to locally bring up the .html pages and/or .png images in the /tmp/jpgraph_cache directory. There should be several blocks of color along with a small description of each. Test some of the options using the following URL. You should be able to view simple graphical representations depending upon what sort of graphical support you compiled in with PHP and GD. - http://<youracidhost>/jpgraph/examples/
Figure 10-2 is an example showing the images generated via the web page. Figure 10-2. Example image generated using the JpGraph utility 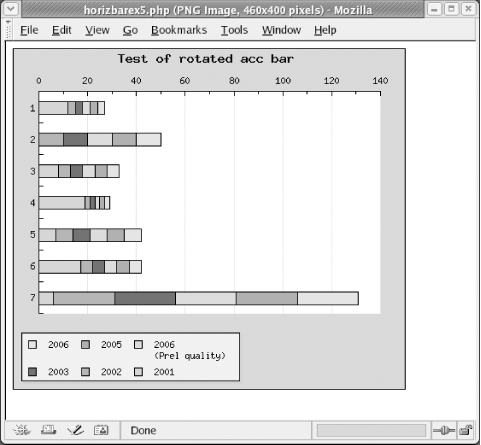
If everything works properly and you can bring up graphical images similar to the examples shown previously using the *.php links, move on to the next step. 10.2.2 Customizing the ACID Configuration Files Once all the programs have been placed in the Apache web root directory and you have verified that GD support has been enabled in the respective programs, begin editing the configuration files for the ACID program. The ACID configuration files should first be examined. Use your favorite text editor; vim, pico, nedit, or emacs all work nicely. Change to the directory holding the configuration files and make the needed modifications. My editor of choice is vim. # cd /usr/local/httpd/htdocs/acid # vim acid_conf.php
In the acid_conf.php file, modify the following entries. Change the variable xxxxxxxx to reflect the password you chose for the Snort database account. $DBlib_path = "../adodb "; $alert_dbname = "snort "; $alert_host = "localhost "; $alert_port = ""; $alert_user = "snort "; $alert_password = "xxxxxxxx "; $ChartLib_path = "../jpgraph ";
There are other options available in this configuration file that can be edited to enhance performance. Exercise caution when modifying anything other than these recommended items. Changing anything other than what is shown may cause your database and program to quit working. Set up the "view only" ACID portal, which again does not allow for event deletion. This is good precaution for those who only need to view alerts, such as managers, helpdesk users, or administrative folk who may do more harm than good. (You know who you are.) Copy the files located in the /usr/local/httpd/htdocs/acid directory to a new directory created in the same root web directory, /usr/local/httpd/htdocs/acidviewer. # mkdir /usr/local/httpd/htdocs/acidviewer # cd /usr/local/httpd/htdocs/acid/ # cp -R * /usr/local/httpd/htdocs/acidviewer/ # cd ../acidviewer # vim acid_conf.php
Modify the following variables in the /usr/local/httpd/htdocs/acidviewer/acid_conf.php file. Again, change the variable yyyyyyyy to reflect the password you've chosen for the acidviewer account. $alert_user = "acidviewer "; $alert_password = "yyyyyyyy ";
Next, secure both of the ACID web sites using the Apache htpasswd utility. Set up two separate accounts for accessing both the snort and acidviewer pages on the ACID website. When prompted, enter the web password you've chosen for that web account. Be careful to omit the -c option when adding more users to the password account. Make certain that the passwords/ directory is owned by the default web user, which, in this case, is webuser. You can opt to create these files and accounts wherever you like. The examples suggested here are only recommendations. # mkdir /usr/local/httpd/passwords # htpasswd -c /usr/local/httpd/passwords/acid_passwords admin # htpasswd /usr/local/httpd/passwords/acid_passwords acidviewer # cd /usr/local/httpd/ # chown -R webuser.webuser passwords/
Add the following lines to /usr/local/httpd/conf/httpd.conf file in the Directory portion of your file. You can place these portions of text near the general area of the other <Directory> sections. <Directory "/usr/local/httpd/htdocs/acid"> AuthType Basic AuthName "your_company_name" AuthUserFile /usr/local/httpd/passwords/acid_passwords Require user admin AllowOverride None </Directory> <Directory "/usr/local/httpd/htdocs/acidviewer"> AuthType Basic AuthName "your_company_name" AuthUserFile /usr/local/httpd/passwords/acid_passwords Require user acidviewer AllowOverride None </Directory>
Restart the HTTP daemon using your command of choice: # /usr/local/httpd/bin/apachectl restart
or the following, if using the Apache RPMs: # service httpd restart
Remember to add one of the above lines to your /etc/rc.d/rc.local or enable startup of the web daemon using the ntsysv or serviceconf command. You may also enable the httpd RPM in all run levels by doing the following: # chkconfig --level 2345 httpd on
A reboot may be the best method to check that everything starts up correctly: the Apache web daemon, permissions, etc. Finally, test your installation and configuration by attempting to connect to these web pages. You should be prompted for a password. If not, go back and check your syntax. Your ACID installation is now complete. However, do not try to modify anything quite yet on the ACID web page. Some additional configuration files still require editing. 10.2.3 The ACID Console You should now have two web sites for the ACID console: one for administrative users to view and delete alerts, the other for management or helpdesk users to only view alerts. They should not have permission to delete alerts. Here is a more detailed listing of the available sites running on the management console machine: - http://<youracidhost>/acid/index.html
This site is for administrative tasks and can be accessed using the "admin" or equivalent account created earlier. View, delete, and sort events using this web address: - http://<youracidhost>/acidviewer/index.html
Anyone requiring read-access only to the intrusion event log should use this web page. It is accessed with the acidviewer account created earlier. Users of this site cannot delete events. 10.2.4 Initializing the ACID Web Page Now you're ready to access and configure the default ACID web page. There are a variety of ways to do this: by accessing the ACID host via its Fully Qualified Domain Name, by its IP address, or by means of its loopback address when configuring the system locally. The first time you connect to the ACID web site, a web page appears stating the following: The database version is valid, but the ACID DB structure (table: acid_ag) is not present. Use the Setup page to configure and optimize the DB. Click on the link labeled "Setup page" to proceed to database initialization. You are then prompted to create the ACID AG, which adds tables to the Snort database and extends the functionality of ACID. Select the button labeled "Create ACID AG." When the table creation process is complete, a new page appears informing you of the successful creation of the ACID tables and the Search Indexes. Click on the hyperlink labeled "Main Page" near the bottom of the browser window. This brings up the main ACID web page. Through this page, you access alerts and notifications regarding any and all suspicious packets captured by the Snort program. From here, you can navigate through all other stored messages, packet headers, and information regarding the captured packets. | 