How the Registry Is Organized
| The Registry leaves the plain text files of AUTOEXEC.BAT and WIN.INI far, far behind. It is a specialized database organized a lot like the files and folders on a hard disk. In fact, the Registry Editor navigates through the Registry using the same expandable list display that Windows Explorer uses to display a disk. Just as a hard disk contains partitions, the Registry contains separate sections called hives. (The reason Microsoft chose the word hive is unclear. It had something to do with busy bees, but more than that, the folks there won't say.) In each hive is a list of named keys that correspond to the folders on a hard disk. Just as a file folder can contain files and yet more folders, a Registry key can contain values, which hold information such as numbers or text strings, and yet more keys. Even the naming of file folders and keys are similar: A folder might be named \Documents and Settings\brian\chapter32, and a Registry key might be named \HKEY_CURRENT_USER\Software\Microsoft. Let's look at the Registry starting with its top-level keys. The two main "top-level" keys are as follows:
The Registry Editor also presents three other sections that look like separate top-level keys:
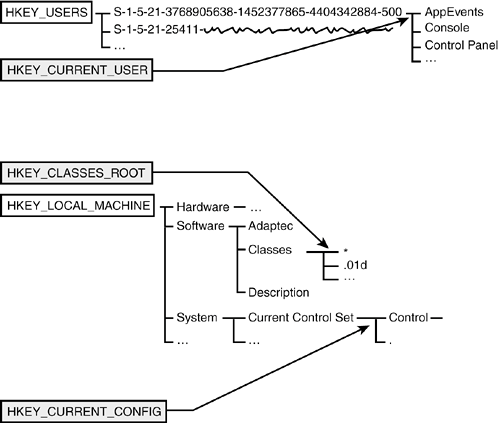
In reality, these keys are views into subkeys of the first two, as illustrated in Figure 32.1. Figure 32.1. The Registry is composed of two true top-level keys and three "virtual" top-level keys.
These three "virtual" top-level keys are there for convenienceit's easier to look in HKEY_CURRENT_USER than to try to remember where to find user entries under the ugly numbered keys inside HKEY_USERS. Within each of the top-level keys, there are several subkeys holding related information. HKEY_CURRENT_CONFIG, for example, contains two keys: Software and System. Software in turn contains two keys: Fonts and Microsoft. (By the way, with keys, just as with folders, you can spell out the full pathHKEY_CURRENT_CONFIG\Display\Settingsor just refer to Settings, if you know you're discussing HKEY_CURRENT_CONFIG\Display). All this might seem a little daunting, but remember that the purpose of the Registry keys is to organize setup information sensibly. Instead of having this information in many mysteriously named and randomly located files, it's all here, filed away in the Registry. CAUTION Another similarity between Registry keys and file folders is that both can have "access permissions" set to prevent unauthorized users from examining or modifying them. I won't go further into this topic, except to recommend that you don't attempt to set or modify the default permissions in the Registry. It's too easy to make a mistake that will prevent even Windows itself from having access to the information it needs. If you implement Group Policies, the Policy Editor will adjust Registry permissions as necessary. The Registry database itself is stored in several separate files, called hives, which I mentioned earlier. HKEY_LOCAL_MACHINE is stored in the folder \windows\system32\config, in several hive files: SAM, SECURITY, SOFTWARE, and SYSTEM. HKEY_USERS is stored with each user's subkey in a separate hive file. These are kept in each user's profile folder (\Documents and Settings\username) as a file named NTUSER.DAT, except the "Default User" key, which is in \windows\system32\config\DEFAULT. Finally, each user has a list of keys used to add to or override HKEY_CLASSES_ROOT, which is stored in \Documents and Settings\username\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat. (If you're interested, you can see that even the information about which file supports which section is maintained in the Registry, under the key HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\hivelist. Just don't try to change these values!) You generally can't examine or modify these files directly while Windows is running because Windows maintains exclusive control of them. Backup software uses special Windows program functions to get access to back up or restore them. The exception, though, is that the NTUSER.DAT files for users not currently logged in are not locked, so they can be copied and backed up as normal files. |
EAN: 2147483647
Pages: 450