Why Use Host Intrusion Prevention
| The primary purpose of this book is to show you how to use PIX version 7 and ASDM to deploy defense in depth in your network. As explained in Chapter 2, "Principles of Network Defense," the ASA/PIX Security Appliance does an excellent job of providing security services at the network level and some services at the application level. By following the steps in the previous chapters, you have already mitigated numerous potential attacks, providing examples on how to implement the following:
In the Internet of yesterday, one could feel safe with the security deployed so far in this book. However, in this modern day, new vulnerabilities are constantly discovered and exploits (malicious code) are being written that take advantage of these vulnerabilities. Most of these new attacks (called day-zero attacks) use valid traffic, follow valid protocol rules, and are still capable of exploiting a vulnerability and compromising your systems. Because a valid protocol was followed and valid traffic was used, firewalls (or any signature-based or most protocol behavior-based systems) cannot recognize these attacks. For this reason, it is important to deploy intrusion prevention software on hosts and servers as the final layer of defense for attack mitigation. NOTE Do not make the mistake of thinking that intrusion prevention needs to be deployed only on servers; many virus or worm outbreaks are targeted at hosts. After a host is infected, it will, in turn, infect the remaining hosts or servers in your network that are not adequately protected. Not all attacks focus on taking your systems down. Some are focused on gathering information or using your system as a zombie to launch other attacks. Day-zero attacks are the most costly to you and your organization. They are designed to take advantage of the time lapse between when the attack is let loose in the wild and when a signature is created to stop them. The bad news is that, in most cases, a tangible cost is already incurred before a signature is created. Slammer was a worm that hit the Internet in 2002. It infected 1.4 million hosts in less than 48 hours. Blaster infected approximately 400,000 hosts in the same amount of time. The list goes on with Nimda, Sasser, Code Red, and many others. The cost of cleaning up after these incidents is staggering. Companies needed to perform some or all of the following to recover from these attacks:
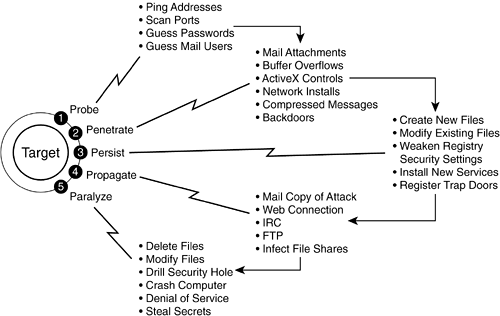
It would be impossible to know exactly how much these attacks cost consumers, but a simple web search investigating costs of viruses reveals that even LoveBug, which had relatively low interest as far as viruses or worms are concerned, costs consumers between $8 billion to $10 billion dollars to mitigate, isolate, and clean up. The same investigation for the Slammer and Blaster worm indicates that each of these attacks cost companies in excess of $3 billion dollars. Customers that had deployed CSA fortunately did not incur any tangible costs as a result of these costly security incidents. In all cases, CSA (with its default rules) recognized that malware was trying to run on host machines and stopped the attempt. The net cost for these customers was zero dollars. Anatomy of a Host or Server AttackOne of the reasons that host intrusion prevention software can be so effective in stopping day-zero or unknown attacks is because the same attack paradigm has been used since the first recorded attack, the Morris worm, on November 2, 1988. This attack paradigm is divided into five phases, as shown in Figure 10-1. Figure 10-1. Worm/Virus Attack Model
NOTE Later, this chapter explains how CSA mitigates attacks in each of the attack phases. Probe PhaseIn the probe phase, attackers attempt to learn as much as they can about the hosts or servers that they plan on attacking. They do this usually by using off-the-shelf freeware tools such as NMAP or Nessus. These tools probe systems and then return the following:
After hackers obtain this information, they can easily access databases on the Internet that tell them how to exploit the specific operating systems and applications. In the case of Nessus, it is easier for hackers; this freeware tool creates a report that also lists the vulnerabilities. Several tools perform this function; these just happen to be two popular and free ones. NOTE Don't be too quick to pass judgment on these tools and their authors. Many businesses and enterprises use these same tools to do security assessments on their systems to ensure that they know and have addressed all of their systems' own vulnerabilities. In most cases, these tools were not meant for malicious purposes. PenetrateThe penetrate phase is where the hacker actually runs the exploit and injects his attack code onto a host or server. In many cases, this is done via a buffer overflow, but it can also be accomplished by other means such as malware running as follows:
If the penetrate phase is successful, the malware has either already run on your machine or will run when the e-mail attachment or the ActiveX code is executed. PersistThe persistence phase is the hacker's attempt to maintain a presence on the host or server he has penetrated the device. This phase involves one or more malicious actions by the attacking software:
If the persistence phase is completed, the hacker has compromised your host or server to a point where not only can he access it any time he wants, but he also probably has administrative or root access and can easily gain access to other machines inside your network. PropagateDuring the propagation phase, hackers try to spread the attack to other devices within your network. They might even go outside your firewall to infect machines on the Internet that belong to other companies and individuals. It was during the propagation phase that attacks such as Slammer and Blaster infected millions of devices in a short period of time. Many small businesses believe that they won't be compromised because they have nothing that anyone else wants. Unfortunately, this isn't correct. Many times, an attack just needs your CPU cycles and a network connection. For example, in a distributed denial-of-service (DDos) attack, a hacker needs several machines to participate in the attack. In this case, the malicious software installs itself on any machine it can compromise. These machines are called zombies; they are usually devices that have limited security, such as those in the following locations:
At a predefined time, the software on these machines will all start simultaneously and attack a specific target. Whitehouse.gov was a victim of such an attack. Another reason an attacker might want to gain access to your PC is to use "your" machine for an attack against someone else. In this case, if law enforcement gets involved, the attacker's tracks are covered and it looks like you launched the attack. CAUTION Propagation attacks could also be used against critical-infrastructure websites. Therefore, it is important to be a good web citizen and take steps to protect your systems even if you think that no one wants the data on your machines. The propagation phase can be done using several different methods:
ParalyzeIf you are a small business or an enterprise, the paralyze phase of an attack could be the most devastating. The paralyze phase usually consists of one or more of the following malicious activities:
This phase of the attack can be costly. Both intangible and tangible costs can be quite high; intangible costs can be a high factor if the attack stole business secrets and customer data; tangible costs of recovery can be quite high. Recently, attackers have favored stealing information and then extorting money from these companies to keep the attack or information secret. To take a deeper look at the paralyze phase of an attack, consider the damage Slammer, which infected 1.4 millions hosts, could have done. The widespread effects could have been devastating to many corporations. An attacker had full administrative or root access to every machine it compromised; the attacker could have decided to do some or all of the following operations on those servers:
Depending on how a hacker wrote her malware, you might be in a position where you need to do a full recovery on all infected devices on your networks. This recover could include the following:
It is precisely because of these reasons that host intrusion prevention is included as a layer of defense in depth. A firewall can protect and mitigate against many attacks, but your systems are not completely secure until you have deployed host intrusion prevention software on your systems. |
EAN: 2147483647
Pages: 120