Managing Users
Users coming from operating systems such as Windows 9x and Windows Me will find in Fedora a more strict arrangement of permissions that describe what each user can and cannot do. One user s processes and data can t be accessed or modified by other users of the system, unless they are specifically permitted to do so. This concept of user security runs through the heart of the Linux system.
User management is discussed in depth in Chapter 8. However, the key points are summarized here.
Understanding User Management
As previously mentioned, the root user (or super user) has complete access over all the computer s resources. For this reason, various security restrictions are put in place in the system to ensure that this user privilege is not compromised. Even as the administrator of the system, you should attempt to do most of your work as a less privileged user, and assume super user privileges only when they re needed.
Many new users will also find it unusual that the Linux desktop allows many users to work on the system simultaneously . While only one user can work physically at the desktop, other users can log in through network services such as telnet and its more secure equivalent, secure shell (ssh).
Linux has a simple way of organizing users. Every user can be part of one or more groups . In addition to securing a resource by applying permissions to individual users, you can place users into a group and apply permissions to the group instead.
Understanding Permissions
We have already talked about how privileges are required to control other users processes; the same applies to files and directories . Every file and directory is associated with a single user (its owner) and also with a group. Then, specific permissions to access a file are given to the three classes of users:
-
The owner
-
The group members
-
Everyone else
Each of the classes is allowed a combination of three kinds of access permissions, as explained in the following table.
| Permission | Meaning when applied to files | Meaning when applied to directories |
|---|---|---|
| Read | Enables the user to read the contents of the file | Enables the user to list the contents of the directory |
| Write | Enables the user to change the contents of the file | Enables the user to create or remove files within the directory |
| Execute | Enables the user to execute the file | Enables the user to access files and subdirectories |
You can find the permissions of a given file using the ls program. The following example uses the command ls “l to display a long version of the file information:
$ ls -l /usr/bin/top -r-xr-xr-x 1 root root 56406 Aug 12 15:50 /usr/bin/top The read, write, and executable permissions are represented using the characters r , w , and x , respectively. The first part of the file information (in the preceding example, the expression -r-xr-xr-x ) indicates the file s permission. The first character indicates the file type (directory, character device, and so on), but it is the remaining characters that we re interested in right now. This sequence consists of three sets of three characters ”one set each to describe permissions of the owner, the group, and the others. For example, the sequence r-x indicates that only the read and execution permissions are set, and no write permission is available. Therefore, this file s permission specifies that all possible users can read and execute the file s content, but they cannot modify the file contents.
You can use the CLI tools chown , chmod , and chgrp to modify the permissions of files and directories in the system. You will learn more about these tools in Chapter 8.
You can add, remove, and modify user accounts on the system in a GUI by using the Red Hat user configuration tool, redhat-config-users , which you can launch using Main Menu>System Settings>Users & Groups. The primary interface of this tool is shown in Figure 2-50.
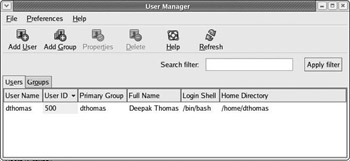
Figure 2-50
You ll need to provide the root password to use this utility. Using this interface you can add, edit, or modify users and groups.
The same operations can be carried out in the CLI, too. The various tools for the job are described in the following table.
| Program | Purpose |
|---|---|
| useradd | Add a user |
| userdel | Remove a user |
| chfn , chsh | Modify user details |
You can read more about the use of these programs in Chapter 8.
Because Fedora can be a multiuser system, it may be necessary for administrators to monitor the system s users. Unlike Microsoft systems, Linux systems allow multiple users to be logged on to the same system, each with their own account. The who command lists the currently logged-on users of the system. The finger command can be used to perform a lookup of the users of a remote system. This requires the finger daemon to be up and running; finger is disabled by default. The example in Figure 2-51 illustrates the use of the who and finger programs. The last command prints a history of user logins.
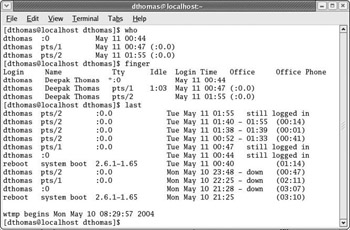
Figure 2-51
EAN: 2147483647
Pages: 170