A Little Anatomy of Computer Security Systems
| for RuBoard |
Why have computer security systems in the first place? Why is it necessary to spend (sometimes considerable amounts of) money and computing time making computers more safe? And what does safety mean in this context? These are the questions that guide the fundamental constitution of any security system and will start us on our discussion of the properties that define computer security systems.
The primary function of any computer security system (and, in fact, of most security systems in general) is the protection of a resource from illicit access. Generally, resources that are in need of protection are those whose misuse could cause annoyance or even considerable loss to the user or users of a computer. For example, unrestricted access to a private medical record or the number of the bank card of a user could cause considerable problems. The following is a list of some resources to which computer security systems typically limit access:
-
Files and Folders ” Limiting access prevents information leaks and information loss.
-
Intranet and Internet access ” Limiting access to intranet and Internet locations can prevent the spreading of information not intended to leave a computer, as well as preventing the contraction of malicious or erroneous programs of unsafe or unknown origin.
-
Memory ” Protecting access of memory location of other programs prevents information loss, exposure, or undue intentional or unintentional side effects on other programs.
-
Special purpose devices ” Access to printers or special computation devices (such as a dedicated hardware instantiation of a cryptography algorithm) is limited to protect the owners of these services from costs incurred due to illicit access or misuse.
-
Global machine or domain configuration state ” Access to the registry, environment variables , machine security configuration files, and so on is limited to prevent the security system from being undermined, as well as to reduce the likelihood of having to reinstall and reconfigure a computer or network of computers due to malicious or erroneous access to the global configuration state.
The better a computer security system protects against illicit access to resources, the more safety it provides. You may now rightfully wonder exactly what defines "illicit access." Unfortunately, there can be no encompassing definition for this concept, because the right to access a resource is a privilege defined largely socially , not by hard and fast rules of computer science. For example, which user of an enterprise gets to write information to an expensive color laser printer, or what program gets to read the files and folders of the computer standing in the CEO's office, is dependent on organizational and social context. Most security systems can be configured to express what illicit access means in a particular usage context.
NOTE
See Part IV, ".NET Framework Security Administration," to find out how to administer the security systems impacting managed code.
Figure 4.1 shows the structure of security systems as we have defined them so far.
Figure 4.1. Control over resource access by security systems.
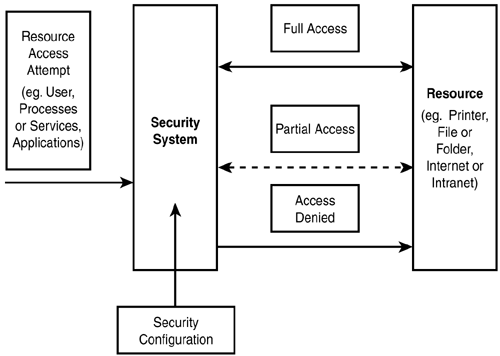
As you can see in Figure 4.1, attempts to access a protected resource will lead the security system to allow either full or partial access to the resource or, conversely, completely reject the access attempt. An example of partial access to a protected resource is the read-only access to a write-protected file or folder. As can be seen, security configuration settings influence the success of resource access attempts. In a sense, a security system is nothing more than a filter that sorts attempts to access resources, blocking some attempts, while partially or fully letting others pass. What then are the mechanisms that make security systems work?
Attempts to access a resource are judged by the identity of who or what makes the call to the resource. Thus, based on the identity of the caller to the resource, the security system determines, in accordance with security configuration settings, what access to the resource the caller should be given. This mechanism of mapping security configuration state and identity of the caller to a set of access rights is termed authorization. Before authorization can take place, however, the security system must collect information and be assured about the identity of the caller to the resource in the first place. That process is called authentication. Finally, for the security system to be effective at all, it must implement an enforcement system. An enforcement system consists of all the mechanisms that block the caller to a resource from working around the access restrictions that authentication may have placed on the caller. We can now replace the ambiguous Security System box in Figure 4.1 with something more concrete.
As can be seen in Figure 4.2, before access to a protected resource can succeed, the caller needed to be authenticated. This means that information about the identity of the caller was collected and potentially ascertained. Authentication is therefore the security system's way of making sure the caller to a resource is who he claims he is, and is used to establish an identity on which security decisions can be based. The identity information is used to determine the access rights to the resource. In other words, the security system authorizes resource access. Finally, the enforcement system blocks and prevents access to the resource that circumvents the authentication or authorization mechanisms.
Figure 4.2. Resource protection through the interplay of authentication, authorization, and enforcement.
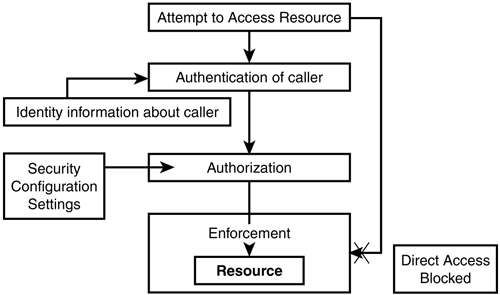
There are actually examples of such security processes at work outside the realm of computer security. One example is the process of entering the United States. At the border, your identity is established and ascertained by a thorough screening of the documents you present. If you carry a U.S. passport that fits your appearance, you will be authenticated as an American citizen. This authorizes you to stay as long as you want within the territory of the U.S., work, and take advantage of other benefits only available to citizens . If, on the other hand, you present a passport of one of the European Union countries , you are authenticated as a non “U.S. citizen from, say, Germany. Without any other identity information (such as additional visas) European Union citizenship authorizes you for a tourist stay within the territory of the U.S. for a few months, but would not give you the right to work or study. Finally, for these authorization regulations to have any value, a certain enforcement system must be in place. For example, all, not just a few, passengers on inbound international flights are required to authenticate themselves .
Much like the system protecting U.S. borders, computer security systems draw boundaries around resources, strongly regulating access to those resources. Specific security systems just differ in the type of resources they protect and the type of identity they are authenticating and authorizing against. We will now look at security systems that grant access rights to and authenticate against user identity.
| for RuBoard |
EAN: 2147483647
Pages: 235
- The Second Wave ERP Market: An Australian Viewpoint
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Context Management of ERP Processes in Virtual Communities
- Development of Interactive Web Sites to Enhance Police/Community Relations