How Does Windows Differ from Linux?
How Does Windows Differ from Linux?
The Windows NT team made a few design decisions early on that profoundly affected every resulting architecture. The NT project was in full swing in 1989, with its first release in 1991 as Windows NT 3.1. Most of the internals originally were taken from VMS, although there were several major differences between VMS and NT, notably an inclusion of kernel threads in the early versions of the NT kernel. In this chapter, we will visit some major features of NT that may not be recognizable to someone used to Linux or Unix internals.
Win32 API and PE-COFF
OllyDbg, a full-featured , assembler-level, analyzing debugger that runs on Windows (see Figure 6.1), is a powerful tool for binary analysis. You will best understand the content in this chapter when working with a binary analysis debugger such as OllyDbg. To apply what you learn here, you will need a tool with its features. OllyDbg is distributed under a shareware license and found at http://home.t-online.de/home/Ollydbg/ .
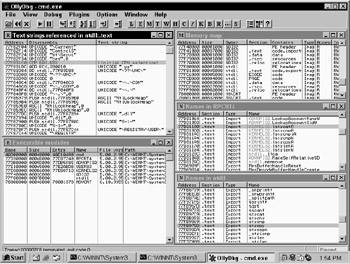
Figure 6.1: OllyDbg can show you all the information you need about any DLLs loaded into memory.
The native API for Windows programs is the 32-bit Windows API, which a Linux programmer can think of simply as a collection of all the shared libraries available in /usr/lib .
| Note | If you are a little rusty on the Windows API or are entirely new to it, you can read an excellent online tutorial on the Windows API by Brook Miles at www.winprog.org/tutorial/. |
A skilled Linux programmer can write a program that talks directly to the kernel, for example by using the open () or write() syscalls. No such luck on Windows. Each new service pack and release of Windows NT changes the kernel interface, and a corresponding set of libraries (known as Dynamic Link Libraries [DLLs]) are included with the release to make programs continue to work. DLLs provide a way for a process to call a function that is not part of its own executable code. The executable code for the function is located in a DLL, containing one or more functions that are compiled, linked, and stored separately from the processes using them. The Windows API is implemented as an orderly set of DLLs, so any process using the Win32 API uses dynamic linking.
This gives the Windows Kernel Team a way to change their internal APIs, or to add complex new functionality to them, while still providing a reasonably stable API for program developers to use. In contrast, you can't add a new argument to a syscall in any Unix variant without a horde of programmers calling foul.
Like any modern operating system, Windows uses a relocatable file format that gets loaded at runtime to provide the functionality of shared libraries. In Linux, these would be .so files, but in Windows these are DLLs. Much like a .so is an ELF file, a DLL is a PE-COFF file (also referred to as PE ”portable executable). PE-COFF was derived from the Unix COFF format. PE files are portable because they can be loaded on every 32-bit Windows platform; the PE loader accepts this file format.
A PE file has an import and export table at the beginning of the file that indicates both what files the PE needs to find and what functions inside those files it needs. The export indicates what functions the DLL provides. It also marks where in the file, once loaded into memory, to find the functions. The import table lists all the functions that the PE file uses that are in DLLs, as well as listing the name of the DLL in which the imported function resides.
Most PE files are relocatable. Like ELF files, a PE file is composed of various sections; the .reloc section can be used to relocate the DLL in memory. The purpose of the .reloc section is to allow one program to load two DLLs that were compiled to use the same memory space.
Unlike Unix, the default behavior in Windows is to search for DLLs within the current working directory before it searches anywhere else. This provides certain abilities to escape Citrix or Terminal Server restrictions from a hacker's perspective, but from a developer's perspective it allows an application developer to distribute a version of a DLL that may be different from the one in the system root (\winnt\system32). This kind of versioning issue is sometimes called DLL-hell . A user will have to adjust their PATH environment variable and move DLLs around so that they don't conflict with each other when trying to load a broken program.
An important first thing to learn about PE-COFF is the Relative Virtual Address (RVA). RVAs are used to reduce the amount of work that the PE loader must accomplish. Functions can be relocated anywhere in the virtual address space; it would be extremely expensive if the PE loader had to fix every relocatable item. You'll notice as you learn Win32 that Microsoft tends to use acronyms (RVA, AV [Access Violation], AD [Active Directory], and so forth) rather than abbreviating the terms themselves as done in Unix (tmp, etc, vi, segfault). Each new Microsoft document introduces a few thousand additional terms and their associated acronyms.
| Note | Fun fact for conspiracy theorists: Near the Microsoft campus is a rather prominent Scientologist building that no one ever seems to go into or come out of. |
RVA is just longhand for saying "Each DLL gets loaded into memory at a base address, and then you add the RVA to the base address to find something." So, for example, the function malloc() is in the DLL msvcrt .dll . The header in msvcrt.dll contains a table of functions that msvcrt.dll provides, the export table. The export table contains a string with malloc and an RVA (for example, at 2000 ); after the DLL is loaded into memory, perhaps at 0x80000000 , you can find the malloc function by going to 0x80002000 . The default Windows NT location into which an .EXE is loaded is 0x40000000 . This may change depending on language packs or compiler options, but is reasonably standard.
Symbols for PE-COFF files distributed by Microsoft are usually contained externally. You can download symbol packs for each version of their operating systems from Microsoft's MSDN Web site, or use their Symbol Server remotely with WinDbg. OllyDbg does not currently support the remote Symbol Server.
For more on PE-COFF, search Microsoft's Web site for "PE-COFF." As a final note, keep in mind that, like a few broken Unixes, Windows NT will not let you delete a file that is currently in use.
EAN: 2147483647
Pages: 198
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability
- Chapter XVII Internet Markets and E-Loyalty