9.2 WebSphere Everyplace Connection Manager
9.2 WebSphere Everyplace Connection Manager
WebSphere Everyplace Connection Manager is composed of a Messaging Gateway (SMS Gateway and Push Proxy Gateway), a WAP Gateway, Remote Access enabler (VPN-IP tunneling), a wireless client and an administration interface (Wireless Gatekeeper).
| Note | WebSphere Everyplace Connection Manager is not part of the WebSphere Everyplace Access 4.2 product; it is a separate product from IBM. |
Following are some security solutions supported by each one of these components . Figure 9-3 also shows in a generic way the several network connections that WebSphere Everyplace Connection Manager supports.
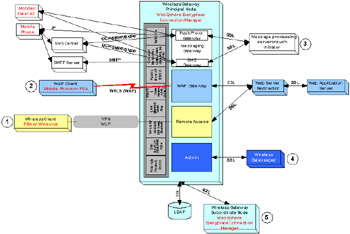
Figure 9-3: WebSphere Everyplace Connection Manager security
-
Wireless Client running on a PDA or a Windows accessing the WebSphere Everyplace Connection Manager through an IP tunnel solution.
This function provides a secure data communication between a client using a PDA or Windows over a public network and a secure network.
Considering that the user wants to access a Web Application that is behind the Wireless Gateway, the following considerations should be taken into account:
-
A secure IP tunnel will be implemented between the Wireless client and the Wireless Gateway
-
All the traffic inside the tunnel is protected
-
If the Web Application supports SSL, it will establish an HTTPS connection between the Web browser on the client and the Web server, and the content will be transported through the IP tunnel.
Authentication is a prerequisite for the communication link between the Wireless Gateway and Wireless Client to be encrypted. The Wireless Gateway uses a modified Point-to-Point Protocol (PPP) called wireless optimized link protocol (WLP) to authenticate the connection between itself and the Wireless Clients . WLP provides data compression, IP header reduction, selective packet filtering, and TCP retransmission optimizations that make data communications over these networks more efficient and cost-effective .
The Wireless Gateway supports:
-
Single-party key distribution protocol. The Wireless Client is authenticated to the Wireless Gateway.
-
Two-party key distribution protocol. The Wireless Gateway and the Wireless Clients authenticate each other.
-
Diffie-Hellman key agreement algorithm. Both the Wireless Gateway and the Wireless Client are given the means to compute the same key. Note that this choice does not perform authentication, only encryption.
In terms of encryption, the WebSphere Everyplace Connection Manager and Wireless Client support the advanced encryption standard (AES), digital encryption standard (DES), RC5 and Triple-DES.
-
-
Secure connection between a WAP client and a WAP Gateway
This functionality provides secure Web access to WAP clients such as mobile phones and PDAs using a WAP browser.
The solution used to provide encryption between the WAP client and the Web Application is as follows :
-
Wireless transport layer security (WTLS) protocol using public-key algorithms to manage key agreement and symmetric key algorithms to encrypt the communication link between the WAP clients and the WAP gateway.
-
SSL protocol to encrypt the communication link between the WAP gateway and the Web Application.
This solution has two secure connections: WTLS and SSL. The encrypted data from WTLS has to be decrypted in order to be re-encrypted under SSL, and vice-versa. The reason is that SSL is defined at the transport level (TCP), and that transport level protocol is different from the one in WAP. The consequence of this is that at one moment the data may pass through the gateway, and in some contexts this might create a security issue.
For solutions on these issue, refer to the IBM Redbook Mobile Applications with IBM WebSphere Everyplace Access Design and Development - SG24-6259-00.
The WAP Gateway supports several methods of authentication to validate a WAP client.
-
Native PPP connections: the Wireless Gateway accepts connections from dial-in devices that support the Point-to-Point Protocol (PPP) protocol. When users are first configured by the administrator, they are assigned a password that is stored securely by the gateway and is communicated to the person using the ID (by phone, secure e-mail, or postal mail) so both parties know the password.
Using either the PAP (password authentication protocol) or CHAP (challenge handshake authentication protocol) authentication protocols, users negotiate authentication with the Wireless Gateway. The Wireless Gateway validates the user's credentials using a persistent user storage database in an LDAP-compliant directory server, or using an external authentication server that uses the RADIUS protocol.
The authentication for establishing a PPP session to Wireless Gateway serves as the authentication mechanism for WAP proxy transactions.
-
Device resolver: though not a method of authentication, the device resolver serves to uniquely identify a WAP client. Authentication of the WAP client takes place elsewhere in the environment, usually at the server that provides network access.
In a typical service-provider environment, the Network Access Server (NAS) has direct access to the provider's wireless network infrastructure, where unique information about a device, such as its phone number, is available. The NAS uses the RADIUS protocol to inform the WAP proxy of that unique identity. The WAP proxy uses the device resolver to match this information to WAP requests and check that the device has previously been authenticated.
-
Account resolver: the account resolver is similar to the device resolver function, but instead of using the RADIUS protocol to get information about the WAP client, the WAP proxy uses HTTP to query the NAS for information about the device.
-
HTTP challenge: the Wireless Gateway can require that user credentials exist in each WAP transaction header.
When user IDs are first configured in the system by the administrator, they are assigned a password that is stored securely on the Wireless Gateway and is securely communicated to the person using the ID (by phone, secure e-mail, or postal mail) so that both parties know the password.
Any transaction that does not contain a user ID and password is discarded, and the WAP client browser is sent a reply with a status code of either Proxy-Authenticate or WWW-Authenticate, depending on the environment. The WAP client browser prompts users to enter their user ID and password, and then resubmit the transaction with the credentials included. These credentials, along with the network address of the WAP client, are used to authenticate the user. The Wireless Gateway can validate the user's credentials using a persistent user storage database in an LDAP-compliant directory server, or using an external authentication server, via the RADIUS protocol.
The encryption between the WAP Gateway and the Web Application is supported using SSL version 2 or 3, and the authentication is provided by x.509 certificates.
-
-
Secure connection between the Message Gateway and message-processing server or push initiator.
This functionality provides encryption and authentication between a message-processing server or push initiator and the Messaging Gateway.
The encryption between the Message Gateway and the message-processing server or push initiator is supported using SSL version 2 or 3, and the authentication is provided by x.509 certificates.
In the WebSphere Everyplace Access package, the message-processing server and the push initiator function is provided by the Intelligent Notification Services. However, the actual version of the Intelligent Notification Services does not support SSL at this moment, but it will be supported in a future release.
The messages flowing between the messaging gateway and the client devices are not encrypted.
-
Secure connection between the Wireless Gatekeeper administration console and the Wireless Gateway.
The Wireless Gateway uses its access manager subsystem to communicate with the Wireless Gatekeeper administration console. The access manager is a process (wgmgrd) that manages interactions between Wireless Gatekeeper, the persistent data store, and Wireless Gateways. The encryption supported is SSL version 2 or 3, and the authentication is provided by X.509 certificates. In addition to X.509 certificate validation, each administrator ID has an associated password. The Wireless Gateway can validate the administrator's credentials against a persistent user storage database in an LDAP-compliant directory server.
-
Inter-gateway cryptography
For load balancing and high availability performance, several Wireless Gateways can work together in a clustered configuration. The cluster manager subsystem controls the communications among the nodes. The encryption between the Wireless Gateways is supported by using SSL version 2 or 3, and the authentication is provided by X.509 certificates.
For more information about the load balancing and high availability solution for WebSphere Everyplace Connection Manager, refer to 11.4, "Applying to a Pervasive Portal solution" on page 249.
EAN: 2147483647
Pages: 83