Noncompliance Inquiries
|
Noncompliance inquiries (NCI) were identified as an ISSO responsibility and the process (Figures 8.9 and 8.10) developed by the InfoSec staff and coordinated with the audit and security management. The NCI process was as follows:
-
Receive allegations of non-compliance by auditors, security personnel, managers, users, and generally anyone else.
-
The allegation was evaluated and if not considered acceptable, filed. [7]
-
If the allegation was substantiated, an inquiry was conducted. The inquiry included interviews, technical reviews, document reviews, etc.
-
The information gathered was analyzed, collated, and provided in a formal report to management with copies to appropriate departments such as Security and Human Resources.
-
The report was protected for reasons of privacy and also included recommendations and trend analyses to mitigate future occurrences.
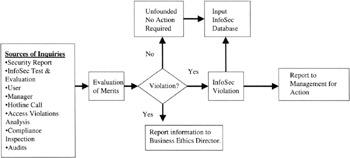
Figure 8.9: An overview of the NCI function.
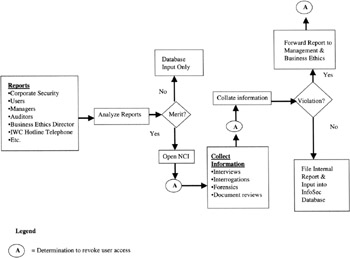
Figure 8.10: The NCI process where revocation of user access is a major consideration.
[7]The ISSO was sensitive to privacy issues and did not want to initiate an inquiry without substantiated information since someone may have a grudge against another and use the process to harass him or her.
|
EAN: 2147483647
Pages: 204