Evaluation of all Hardware, Firmware, and Software
|
All new hardware, firmware, and software should be evaluated for its impact on the security of information and systems. This was determined to be necessary in joint agreement between the ISSO and the IT Department personnel, auditors, and security personnel.
In order to cost-effectively perform this function with minimal impact on cost and installation schedules, it was determined that a baseline checklist would be developed and that this checklist would be completed by the suppliers of the product, in concert with the InfoSec staff. Any items that adversely affected InfoSec would be evaluated based on a risk assessment, using the approved risk management and reporting process.
The process included completion of the baseline InfoSec checklist document, and a technical evaluation by InfoSec personnel in concert with IT personnel. If the item (hardware, software, etc.) was considered risk-acceptable, it was approved for purchase.
If the item was not risk-acceptable, the risk management process identified countermeasures. Although this process generally approves the purchase of almost all items, some items might have an unacceptable level of risk, but would still be accepted because of their value to the company. In those instances, special audit trails could be created to monitor the use of the item. In any case, the ISSO understood that it is always better to at least know that a system is vulnerable, than to not know the vulnerability existed until it was too late.
The ISSO identified the several potential processes relative to new, modified, or upgraded IWC systems' hardware, software, and firmware implementation where the protection of information and information systems could be subject to increased vulnerabilities (Figures 8.5, 8.6, and 8.7). The ISSO decided to form a project team to evaluate these and other processes. The project team would include ISSO's staff specialist as a project lead, as well as IT representatives, department representatives, procurement representative, contracts representative, and legal representative. These representatives were chosen for the following reasons:
-
IT: They are responsible for the major systems, such as intranets and Internet interfaces.
-
Departments: They are responsible for their own standalone systems, such as microcomputers, and for their own local area networks that are not connected outside the department.
-
Procurement: They are responsible for ordering the hardware, software, and firmware.
-
Contracts: They, based on ISSO coordination, include InfoSec-related specifications and clauses in the IWC contracts, such as software from a vendor certified free of malicious codes. Furthermore, if product is vulnerable or increases IWC systems' vulnerabilities, the contract may call for the vendor to patch the software or provide the source code for IWC programmers to patch the code.
-
Legal: They are responsible for ensuring that all issues related to contracts and procurement matters mandating InfoSec criteria are stated in such a way as to ensure their enforcement through legal means.
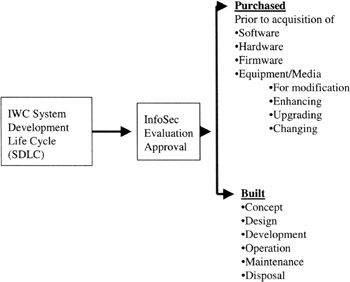
Figure 8.5: An overview of InfoSec input to a System Development Life Cycle (SDLC) process.
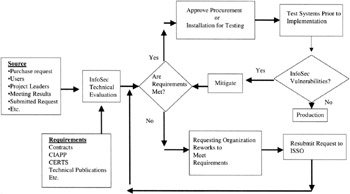
Figure 8.6: One view of the process of InfoSec technical evaluation and testing of a product for InfoSec vulnerabilities.
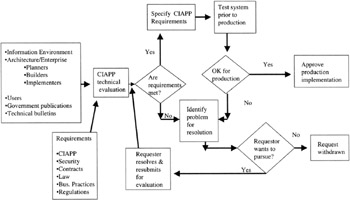
Figure 8.7: Another view of an InfoSec technical evaluation process.
|
EAN: 2147483647
Pages: 204