Introduction
|
We live in a world of information, known these days as an information environment (IE). Information that is pulled, pushed, dragged around the world through wireless, cable, optical fiber, and other assorted physical devices—and all of us along with it. We are dependent on information as individuals, companies, and government agencies. In fact, has that not always been the case? In days gone by, information was communicated by word of mouth, by drums, smoke signals, in writing carried by couriers on horseback, by telegraph, telephone, and now through the use of high technology.
The difference today is that in the "modern" countries of the world, we are more dependent on information and the high technology that allows us to communicate and do business, globally, at the speed of light. Today, more than ever, information—accurate information, and more of it, delivered faster—allows one an advantage. More than ever, this applies to companies, especially those involved in the global marketplace and in global competition.
Fast, accurate, and complete information provides the opportunity to gain a competitive advantage—assuming of course that the information is correctly acted upon in time to provide that advantage. The responsibility of the ISSO is to support this process by assisting in storing, processing, transmitting, and displaying that fast, accurate, and complete information in a secure manner. This support is necessary in order to assist in providing the company competitive advantage opportunities.
These opportunities to take advantage of information were summarized by Colonel John R. Boyd, United States Air Force, as a strategy based on the "OODA loop" (Observe-Orient-Decide-Act). The idea is to look at it from the viewpoint that whoever can be the quickest to move through this loop can gain a competitive advantage. Information has always been time dependent and probably is more so today then ever before. That is why it is crucial to be able to have a tighter (using less time) OODA loop than one's adversaries, whether they be a nation-state, a business, or an individual.
In addition, this advantage is created because the competitor becomes more confused and uncertain over events, and that may influence the competitor's judgement and decisions. In Patterns of Conflict, Boyd concluded that operating inside an opponent's OODA loop (see Figure 1.1) generates uncertainty, doubt, mistrust, confusion, disorder, fear, panic, and chaos.
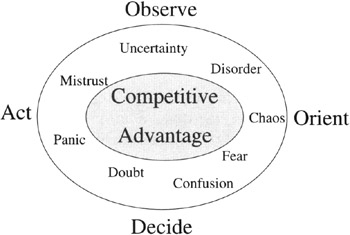
Figure 1.1: The OODA Loop Concept
Figure 1.1 is one example of the OODA loop where a company with a smaller OODA loop (inner circle) operates faster than the competition, shown by the large circle.
CASE STUDY
In his book Following the Equator,[2] Mark Twain wrote about how one can take advantage if one has information before the competitor and knows how to act on that information. At the time of Twain's world travels, sharks populated the harbor of Sydney, Australia. The government paid a bounty on sharks. A young man was down on his luck and walking around the harbor when he met an old man who was a shark-fisher, who had not caught a shark all night. The old man asked the young man to try his luck. The young man caught a very large shark. As was the custom, the shark was disemboweled, as sometimes one found something of value. As it happened this young man did.
The young man went to the house of the richest wool-broker in Sydney and told him to buy the entire wool crop deliverable in 60 days. They formed a partnership based on what the young man found in the shark. It seems that the shark had eaten a German sailor in the Thames River. In the belly of the shark were found not only his remains, some buttons, and a memorandum book discussing the German's returning home to fight in the war, but also a copy of the London Times that had been printed only 10 days before. At that time, news from London came by ship that took about 50 days. However, sharks traveled faster than the ships of that time. The Times stated that France had declared war on Germany, and wool prices had gone up 14% and were still rising. No other Australian wool brokers or wool producers would know that wool prices were skyrocketing for at least 50 days. By then the young man and his partner the wool broker would own all the wool, purchased at the "normal lower price," and could ship it to Europe for a very handsome profit.
This case study is an example of how accurate information received and acted upon within the competitor's OODA loop can give one a tremendous advantage in business. So, the old saying "information is power" is probably more true today than ever before, again providing that:
-
The information is accurate,
-
It is acted upon correctly, and
-
It is acted upon before it is acted upon by your competitor.
-
knowledge: definite knowledge acquired or supplied about something or somebody
-
gathered facts: the collected facts and data about a particular subject
-
making facts known: the communication of facts and knowledge
-
computer data: computer data that has been organized and presented in a systematic fashion to clarify the underlying meaning
Remember that if your company's information systems were the victim of a successful denial-of-service attack, important information could not get to the right people at the right time so that they could use that information to gain a competitive advantage.
Understanding Your Information-Driven Environment
As an ISSO, it is very easy to get caught up in high technology and view that as "your world." After all, in today's high-technology-driven and high-technology-dependent world, it is very easy to look at information and high technology as your working environment, what causes your problems, and where the solutions to your problems lie. However, the truth is that high technology is just a tool like any other tool. And as with any tool, it can be used as intended, abused, or used for illegal purposes—by people.
In today's information world environment that you must work in, it is much more than just high technology. You must understand this world and also us humans, as all these topics have a direct bearing on the protection of information and information systems. They include such things as:
-
Global and national marketplaces;
-
Global and nation-states' economies;
-
International politics;
-
World cultures and societies;
-
International and national laws, treaties;
-
Major languages of the world;
-
Major religions;
-
Business;
-
Human relations and psychology; and
-
Governments of nation-states.
To be successful, the ISSO must have a varied background not only in such things as computer sciences but also in psychology, social science, geopolitical matters, international business, world history, economics, accounting, and finance. Also, the more foreign languages the ISSO knows, the better. Volumes have been written about each of these topics. It would behoove the ISSO to have a working understanding of each of these topics, as they all affect the ISSO's ability to successfully establish and manage a successful information protection program. There are few professions today that offer the challenges that face the ISSOs of government agencies and businesses all over the world.
ISSOs must understand the world in which they will work in order to be successful. In the past, this understanding was generally limited to the company or government agency in which the ISSO worked, and to their computer systems, which were isolated within the company. The ISSOs generally were only concerned with the events that took place within their respective countries, as what happened outside of that limited world usually did not affect their work. However, that was in the past.
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.—Sun Tzu
The environment of the ISSO that may affect the protection of information and information systems is now global in scope, and high technology is changing more rapidly with each passing year. This new global business environment and its associated high technology must be clearly understood by the ISSO. This is because it is all integrated into a driving force which will dictate what must be done to protect the information systems and the information that they store, process, display, and transmit. It will also determine how successful the ISSO's information systems security (InfoSec) program will be in providing protection at least cost to the business or government agency.[4]
Today's computer system environments are all based on the microprocessor. The microprocessors have become cheaper and more powerful at the same time. This is the primary cause for their proliferation throughout the world. One systems specialist has found that one megabyte of storage in 1975 cost $350; in 1985 it cost $30; and in 1995 it cost $1! Now, its costs are measured in pennies. If this rate continues, storage may soon be free. And as we all know, the storage of information is one of the key elements needing protection within the company or government agency. In fact, some computer manufacturers now offer free upgrades when you purchase one of their systems online.[5]
Desktop Special Offers—Notebook Special Offers:
-
FREE Memory Upgrade—Online Only! With purchase of any new Dimension desktops. Ends Wednesday!
-
FREE Hard Drive Upgrade—Online Only! With online purchase of any new InspironTM 8200 or 4150 notebook. Ends Wednesday!
-
FREE 2nd Battery—Online Only! With purchase of new Inspiron 8200 notebooks. Ends Wednesday!
When we think of computers, we sometimes look at them as very complicated devices, when in fact they are not that difficult to understand. Computers are composed of the hardware, the physical pieces; the software, the instructions to the computer which can be altered; and the firmware, which are instructions embedded on a microprocessor. Together, they are used to process, store, display, and/or transmit information. Of course the more an ISSO knows about how hardware, firmware, and software work, the better position the ISSO will be in to protect those systems and the information they process, store, display, and/or transmit.
Computers have been around for some time. We continue to celebrate the "birthday" of the ENIAC, the world's first major computer system. The microcomputer, which is much more powerful than the ENIAC, has not been around that long.
In many of today's information-based nation-states, we have been able to network thousands of systems because of the rapid advances in high technology and cheap hardware. We have built the information systems of the nation-states' businesses and government agencies into major information infrastructures known as the National Information Infrastructures (NIIs). A standalone computer system (one with no external connections between it and other computers) today is relegated to a small minority of businesses and government agencies. We cannot function in today's business world and in our government agencies without being connected to other information systems—both national and internationally.
The protection of information systems and the information that they process, store, display, and/or transmit is of vital concern in this information world. Many nation-states are already in the Information Age, with many other nation-states now entering that age, with yet many more close behind. This will complicate the information protection problems of the ISSO.
The ISSO must remember that the information protection program must be service and support oriented. This is of vital importance. The ISSO must understand that the information protection program, once it is too costly, outdated, and does not meet the service and support needs of the business or government agency, will be discarded or ignored. So, one of the ISSO's challenges is to facilitate the networking of systems nationally and internationally while protecting company information and systems.
In order to provide the cost-effective information protection program, the ISSO must continually keep up with high technology. The ISSO must continuously be familiar with technological changes in general and intimately familiar with the technology being planned for installation within their business or government agency.
The ISSO must understand how to apply information protection and integrate information protection into, around, and onto the new high technology. Failure to do so would leave the information and their systems vulnerable to attack. In that case, the ISSO would have a serious problem—possibly a job security problem—if a successful attack occurred due to the new-found vulnerability brought on by the newly implemented technology.
The ISSO could delay installation of the new high technology until a suitable information protection "umbrella" could be installed. However, in most businesses, this would be considered a career-limiting or career-ending move. In today's business world, the phrase "time is money" is truer than ever. In today's and tomorrow's highly technologically based environment, innovation and flexibility are key words for the ISSO to understand and apply to the company's or government agencies' information protection program.
Thus, the ISSO has very little choice but to support the installation of the new high technology and incorporate information protection as effectively and efficiently as possible. And one of the ways to successfully provide that service and support is to keep up with technological changes.
[2]Twain, Mark, Following the Equator. P.F. Collier & Son, New York, 1992, pp. 109–116.
[3]Definition taken from Microsoft's Encarta World English Dictionary (see http://www.microsoft.com/encarta/).
[4]Throughout this book, we will use the terms "business," "company," and "corporation" interchangeably. Although the information provided is very applicable to government agencies, nonprofit entities, and the like, these terms will not usually be used. The reader who is responsible for information and information protection within these other entities is kindly asked to just think of "company" et al. as describing a government agency or other entity as applicable.
[5]http://www.dell.com/us/en/dhs/default.htm?rpo=true
|
EAN: 2147483647
Pages: 204