4.7 Virus Protection
4.7 Virus Protection
| Caution | Every Excel file that you receive from a friend, acquaintance, or customer might contain a virus! It doesn't matter by what medium the file is transferred, since Excel viruses (or, more generally , Office viruses and VBA viruses) are a part of the file, and can be passed on via diskette, CD-ROM, or even by e-mail. As is usual with viruses, a virus can be transmitted by the sender (perhaps without the individual's knowledge). Therefore, be cautious, even if you know the sender! This section provides some background information on viruses and protection against them. |
Event procedures and the Auto_Open and Auto_Close procedures are a useful construction. However, they are the key to virus programming in VBA. (The first Excel virus appeared in the summer of 1996, only a few months after I warned about the possibility in the first edition of this book.)
VBA offers all of the essentials for programming a virus:
-
The possibility for program code to be executed automatically ( Auto_Open and Auto_Close , as well as countless event procedures).
-
The possibility to alter other Excel files (important for the " transplantation " of viruses).
-
The possibility to insert new program code or to alter already existing code. (The VBIDE object library included with Excel 97 offers unsuspected new possibilities for virus programmers. Is this really what the inventors had in mind?)
-
The possibility of doing damage to the computer in the most various ways. For example, thanks to DLL support, nearly all of the operating system functions can be called. Thanks to ActiveX automation, every object library installed in the computer can be used. For example, under Windows 2000 the settings in the entire security system can be altered with a few lines of VBA code if the code is executed by a user with Administrator status! For example, you can access all e-mail messages and their addresses if the user employs the e-mail client Outlook.
It would be pointless to go into all the details here. What is important is that you become aware that any Excel file can contain a virus, even if the file looks like a completely innocent worksheet. It goes without saying that this holds as well for templates and for add-ins (they are, after all, VBA programs).
Preventing Automatic Execution of Macros
In TOOLSMACROSECURITY there are three options among which to choose (see Figure 4.4):
-
High Security: "Only signed macros from trusted sources will be allowed to run." Signing indicates a process by which a VBA project is associated with a check sum, and in addition, the identity of the author is stored with the project. A subsequent alteration of the project is no longer possible. Trusted sources are developers or companies from whom you have already installed an Add-In or ActiveX component for Internet Explorer and have thereby proved that these sources are to be trusted in future without further inquiries.
Since it is somewhat difficult for a private user to sign VBA code, this means that the execution of macros is almost entirely prevented. For VBA programmers this is unacceptable, but for many standard users this setting is completely reasonable. Of course, it is then impossible to use Excel applications or templates such as those described in this book.
-
Medium Security (default setting): "You can choose whether or not to run potentially unsafe macros." When Excel files are loaded that contain VBA code, a warning appears. You can then enable or disable macros.
-
Low Security: All macros will be executed without any warnings. For VBA programmers especially this is the most convenient setting. But it is also the most dangerous!
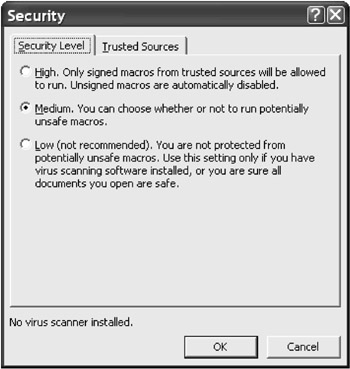
Figure 4.4: The three levels of virus security
In Excel 2000 the default setting is medium, while in Excel 2002 it is high. Note that in both versions of Excel many situations have been discovered in which the macro virus protection can be circumvented. Microsoft usually responds quickly with a security update, but these cases show that a blind trust in the security settings is unfortunately not warranted. In Excel 2002 the best virus protection consists in not installing VBA at all, though then, of course, you lose an enormous amount of functionality, and so this option does not make sense, at least for readers of this book.
| Note | Even traditional Excel 4 macros (without VBA code) can contain viruses. For reasons that are difficult to comprehend, it is impossible to prevent the execution of such macros.When Excel recognizes by means of active virus protection that the Excel file contains traditional macros, it gives notification of this fact.You can then decide whether you wish to open the file anyhow (and take your chances with the macros that might be executed). |
| Caution | The level of virus protection is stored in the registry. Virus programmers can make use of this fact and change the setting (through another program, such as VBScript code in an e-mail message). Therefore, take a look every now and then at your virus protection setting! |
| Note | When you pass an Excel file that contains VBA code to someone else, you should advise the recipient of that fact. Otherwise, the recipient may suspect that there may be a virus and deactivate code execution. Information on signing your VBA code can be found in Chapter 14. |
Viruses in Add-Ins and Templates
Templates are the basis on which Excel files are created (for details see Chapters 5 and 9). Add-ins offer the possibility to expand Excel's front end. Excel recognizes two types of add-ins for this purpose: traditional add-ins ( *.xla ) and COM add-ins ( *.dll ). Details and background information on add-ins are given in Chapter 14.
At this point it is important to note only that templates and both types of addins are further playgrounds for viruses. For these files, however, there is another method of protection. In the second tab of the virus protection dialog it is possible to set whether add-ins and templates are to be considered safe in general (see Figure 4.5). Warning: The default setting is to consider them safe! A file installed as an automatic template or a registered COM add-in will be started automatically without question the next time Excel is started.
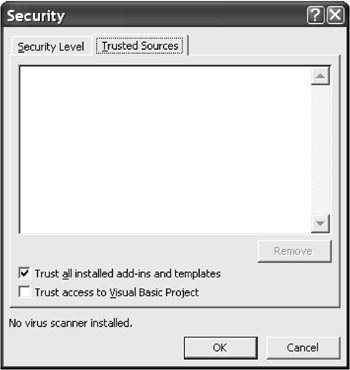
Figure 4.5: Add-ins are considered safe in the default setting
Since add-ins are an integral part of Excel, it is difficult to alter this setting: If you deactivate the option TRUST ALL INSTALLED ADD-INS AND TEMPLATES, then the security level that has been set holds for all add-ins and templates. If you have chosen medium security, then in the future, every time Excel is launched you will be bombarded by numerous virus protection tests (by every one of the countless included add-ins, for example). This leads to the inevitable result that you simply click on ENABLE MACROS, which turns virus protection into an absurdity. (Why Microsoft does not sign its own macros is yet another mystery.)
For this reason the option TRUST ALL INSTALLED ADD-INS AND TEMPLATES is usually activated, leaving add-ins and templates an open door for virus programmers. (Add-ins and template files are more unwieldy than normal Excel files for virus programmers, because they represent a danger only if they are correctly installed. But this hurdle is easily overcome .)
New in Excel 2002 is the option TRUST ACCESS TO VISUAL BASIC PROJECT. This option specifies whether VBA code is permitted to use the VBE library (VBIDE), which allows for the dynamic alteration of VBA code. This is particularly attractive to virus programmers, but there are also legitimate uses for this library.
Discovering Viruses on Your Own
If an Excel file appears suspicious to you, then load the file with virus protection activated. Then look at the following code:
-
Auto procedures. (Use the command EDITFIND and extend the search domain to the entire current project.)
-
All event procedures. (Potentially dangerous code can be hidden in an event procedure, which would be called, for example, on saving the file or changing sheets.)
-
Test with TOOLSREFERENCES whether the library VBIDE is activated. This library is the key to the manipulation of the program code of other Excel files. If this library is activated, then there should be a good reason for this, one that has been documented by the developer of the Excel file.
Excel 4 Auto Macros
Even the traditional Excel macro language (up to version 4) had various Auto macros, which for reasons of compatibility are executed, right up to the current version. These Auto macros are launched by means of Name objects whose name begins with "Auto_Open." Name objects can also contain references to external files (for example, to add-in files). Furthermore, the Visible property of Name objects can be set to False . If you are suspicious that a virus may be present and can find no Auto_Open procedure, then you should have a look at all Name objects (for all worksheets as well as for the Workbook object). In the immediate window the two instructions look like this:
For Each s In Worksheets: For Each n In s.Names: _ ?n.Name: Next: Next For Each n In ActiveWorkbook.Names: ?n.Name: Next
EAN: 2147483647
Pages: 134